Four different malicious frameworks designed to attack air-gapped networks were detected in the first half of 2020 alone, bringing the total number of such toolkits to 17 and offering adversaries a pathway to cyber espionage and exfiltrate classified information. "All frameworks are designed to perform some form of espionage, [and] all the frameworks used USB drives as the … [Read more...] about Researches Detail 17 Malicious Frameworks Used to Attack Air-Gapped Networks
Malicious
11 Malicious PyPI Python Libraries Caught Stealing Discord Tokens and Installing Shells
Cybersecurity researchers have uncovered as many as 11 malicious Python packages that have been cumulatively downloaded more than 41,000 times from the Python Package Index (PyPI) repository, and could be exploited to steal Discord access tokens, passwords, and even stage dependency confusion attacks. The Python packages have since been removed from the repository following … [Read more...] about 11 Malicious PyPI Python Libraries Caught Stealing Discord Tokens and Installing Shells
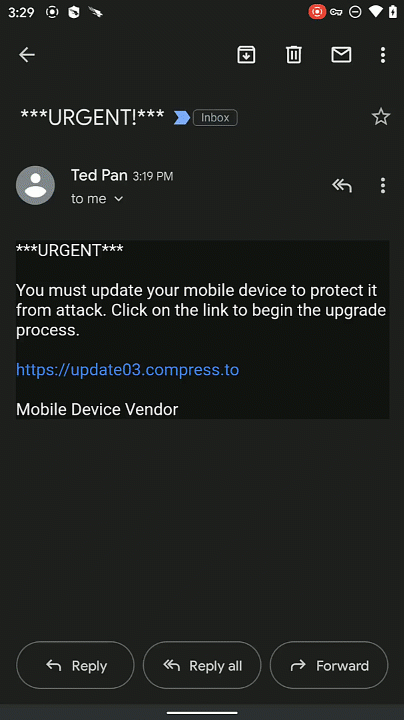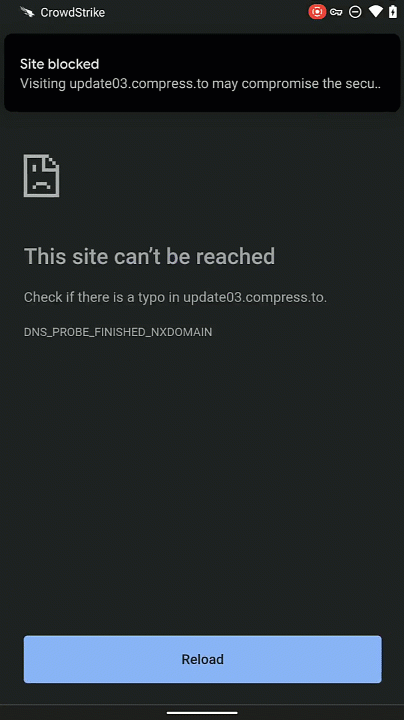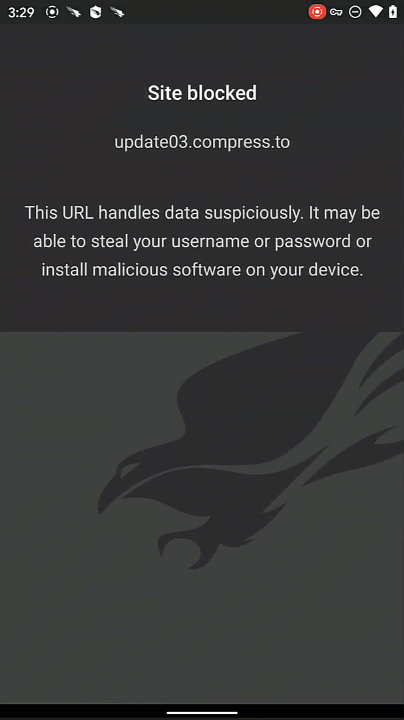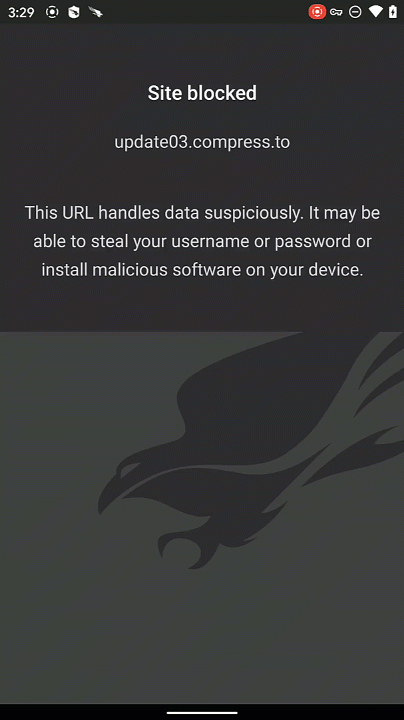
Protecting Users from Malicious Sites with Falcon for Mobile
Introduction Today, mobile devices are ubiquitous within enterprise environments. But with their proliferation, it provides adversaries with yet another attack surface with which they can target users and cause a breach. From phishing attacks to malicious apps, mobile users tend to let their guard down and potentially click on obfuscated links to malicious sites. Falcon for … [Read more...] about Protecting Users from Malicious Sites with Falcon for Mobile
Experts Detail Malicious Code Dropped Using ManageEngine ADSelfService Exploit
At least nine entities across the technology, defense, healthcare, energy, and education industries were compromised by leveraging a recently patched critical vulnerability in Zoho's ManageEngine ADSelfService Plus self-service password management and single sign-on (SSO) solution. The spying campaign, which was observed starting September 22, 2021, involved the threat actor … [Read more...] about Experts Detail Malicious Code Dropped Using ManageEngine ADSelfService Exploit
Malicious Ads Target Cryptocurrency Users With Cinobi Banking Trojan
A new social engineering-based malvertising campaign targeting Japan has been found to deliver a malicious application that deploys a banking trojan on compromised Windows machines to steal credentials associated with cryptocurrency accounts. The application masquerades as an animated porn game, a reward points application, or a video streaming application, Trend Micro … [Read more...] about Malicious Ads Target Cryptocurrency Users With Cinobi Banking Trojan
Several Malicious Typosquatted Python Libraries Found On PyPI Repository
As many as eight Python packages that were downloaded more than 30,000 times have been removed from the PyPI portal for containing malicious code, once again highlighting how software package repositories are evolving into a popular target for supply chain attacks. "Lack of moderation and automated security controls in public software repositories allow even inexperienced … [Read more...] about Several Malicious Typosquatted Python Libraries Found On PyPI Repository
Malicious NPM Package Caught Stealing Users’ Saved Passwords From Browsers
A software package available from the official NPM repository has been revealed to be actually a front for a tool that's designed to steal saved passwords from the Chrome web browser. The package in question, named "nodejs_net_server" and downloaded over 1,283 times since February 2019, was last updated seven months ago (version 1.1.2), with its corresponding repository leading … [Read more...] about Malicious NPM Package Caught Stealing Users’ Saved Passwords From Browsers
Malicious spam spreading banking Trojans
For employees facing hundreds of e-mails, the temptation to speed-read and download attachments on autopilot can be great. Cybercriminals, of course, take advantage, sending out seemingly important documents that might contain just about anything from phishing links to malware. Our experts recently discovered two very similar spam campaigns distributing the IcedID and Qbot … [Read more...] about Malicious spam spreading banking Trojans
Minnesota University Apologizes for Contributing Malicious Code to the Linux Project
Researchers from the University of Minnesota apologized to the maintainers of Linux Kernel Project on Saturday for intentionally including vulnerabilities in the project's code, which led to the school being banned from contributing to the open-source project in the future. "While our goal was to improve the security of Linux, we now understand that it was hurtful to the … [Read more...] about Minnesota University Apologizes for Contributing Malicious Code to the Linux Project
Malicious Amazon Alexa Skills Can Easily Bypass Vetting Process
Researchers have uncovered gaps in Amazon's skill vetting process for the Alexa voice assistant ecosystem that could allow a malicious actor to publish a deceptive skill under any arbitrary developer name and even make backend code changes after approval to trick users into giving up sensitive information. The findings were presented on Wednesday at the Network and Distributed … [Read more...] about Malicious Amazon Alexa Skills Can Easily Bypass Vetting Process