Google has stepped in to remove several Android applications from the official Play Store following the disclosure that the apps in question were found to serve intrusive ads. The findings were reported by the Czech cybersecurity firm Avast on Monday, which said the 21 malicious apps (list here) were downloaded nearly eight million times from Google's app marketplace. The apps … [Read more...] about Google Removes 21 Malicious Android Apps from Play Store
Malicious
Amazon Alexa Bugs Allowed Hackers to Install Malicious Skills Remotely
Attention! If you use Amazon's voice assistant Alexa in you smart speakers, just opening an innocent-looking web-link could let attackers install hacking skills on it and spy on your activities remotely.Cybersecurity researchers today disclosed severe security vulnerabilities in Amazon's Alexa virtual assistant that could render it vulnerable to a number of malicious … [Read more...] about Amazon Alexa Bugs Allowed Hackers to Install Malicious Skills Remotely
How We Trained Overfit Models to Identify Malicious Activity
In this blog, we present the results of some preliminary experiments with training highly “overfit” (interpolated) models to identify malicious activity based on behavioral data. These experiments were inspired by an expanding literature that questions the traditional approach to machine learning, which has sought to avoid overfitting in order to encourage model … [Read more...] about How We Trained Overfit Models to Identify Malicious Activity
Finding the malicious needle in your endpoint haystacks
Accelerate Threat Hunts and Investigations with Pre-Curated Complex Queries Security teams often lack the ability to gain deep visibility into the state of all their endpoints in real time. Even with a bevy of tools at their fingertips, once an incident occurs, conducting investigations can be likened to searching for a needle in a haystack. Teams struggle to make well informed … [Read more...] about Finding the malicious needle in your endpoint haystacks
Over A Billion Malicious Ad Impressions Exploit WebKit Flaw to Target Apple Users
The infamous eGobbler hacking group that surfaced online earlier this year with massive malvertising campaigns has now been caught running a new campaign exploiting two browser vulnerabilities to show intrusive pop-up ads and forcefully redirect users to malicious websites.To be noted, hackers haven't found any way to run ads for free; instead, the modus operandi of eGobbler … [Read more...] about Over A Billion Malicious Ad Impressions Exploit WebKit Flaw to Target Apple Users
CamScanner is a malicious Android app with more than 100 million downloads in Google Play
Kaspersky researchers recently found malware in an app called CamScanner, a phone-based PDF creator that includes OCR (optical character recognition) and has more than 100 million downloads in Google Play. Various resources call the app by slightly different names such as CamScanner — Phone PDF Creator and CamScanner-Scanner to scan PDFs. Official app stores such as Google … [Read more...] about CamScanner is a malicious Android app with more than 100 million downloads in Google Play
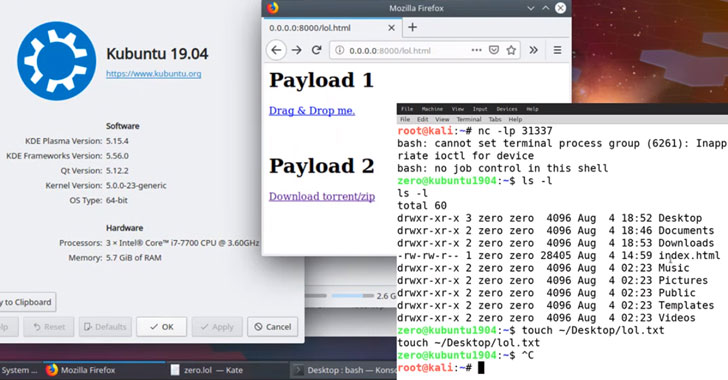
KDE Linux Desktops Could Get Hacked Without Even Opening Malicious Files
If you are running a KDE desktop environment on your Linux operating system, you need to be extra careful and avoid downloading any ".desktop" or ".directory" file for a while.A cybersecurity researcher has disclosed an unpatched zero-day vulnerability in the KDE software framework that could allow maliciously crafted .desktop and .directory files to silently run arbitrary code … [Read more...] about KDE Linux Desktops Could Get Hacked Without Even Opening Malicious Files