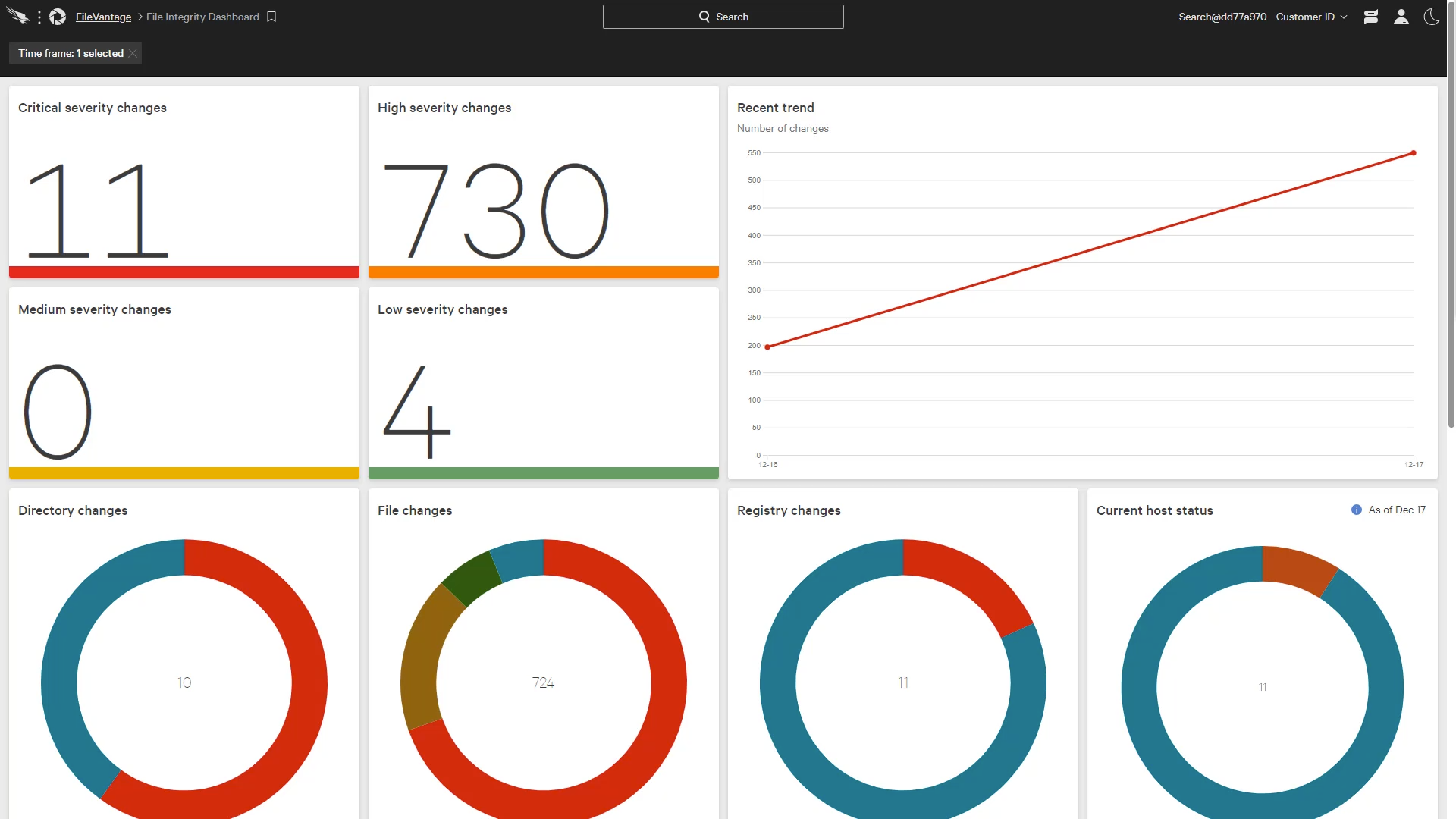
Introduction Due to compliance regulations, many organizations have a need to monitor key assets for changes made to certain files, folders or registry settings. File Integrity Monitoring (FIM) can be a daunting deployment that requires yet another solution in the security stack. As a cloud delivered platform, CrowdStrike leverages a single light-weight agent to address a … [Read more...] about Monitoring File Changes with Falcon FileVantage
Monitoring
Cybercriminals Are Using Legit Cloud Monitoring Tools As Backdoor
A cybercrime group that has previously struck Docker and Kubernetes cloud environments has evolved to repurpose genuine cloud monitoring tools as a backdoor to carry out malicious attacks, according to new research."To our knowledge, this is the first time attackers have been caught using legitimate third party software to target cloud infrastructure," Israeli cybersecurity … [Read more...] about Cybercriminals Are Using Legit Cloud Monitoring Tools As Backdoor