Imagine getting paid for access to just a tiny portion of your Internet bandwidth at work. Sounds pretty sweet, doesn’t it? The computer is on all the time anyway, and you have unlimited Internet access, so why not? It’s not even your own resources, just corporate equipment and bandwidth. That all sounds simple, but you don’t have to look too closely to see that when you agree … [Read more...] about The danger of proxyware in corporate networks
networks
Israeli Researcher Cracked Over 3500 Wi-Fi Networks in Tel Aviv City
Over 70% of Wi-Fi networks from a sample size of 5,000 were hacked with "relative ease" in the Israeli city of Tel Aviv, highlighting how unsecure Wi-Fi passwords can become a gateway for serious threats to individuals, small businesses, and enterprises alike. CyberArk security researcher Ido Hoorvitch, who used a Wi-Fi sniffing equipment costing about $50 to collect 5,000 … [Read more...] about Israeli Researcher Cracked Over 3500 Wi-Fi Networks in Tel Aviv City
Extending Zero Trust Security to Industrial Networks
Recent cyber attacks on industrial organizations and critical infrastructures have made it clear: operational and IT networks are inseparably linked. With digitization, data needs to seamlessly flow between enterprise IT and industrial OT networks for the business to function. This tighter integration between IT, OT, and Cloud domains has increased the attack surface of both – … [Read more...] about Extending Zero Trust Security to Industrial Networks
New 5G Flaw Exposes Priority Networks to Location Tracking and Other Attacks
New research into 5G architecture has uncovered a security flaw in its network slicing and virtualized network functions that could be exploited to allow data access and denial of service attacks between different network slices on a mobile operator's 5G network. AdaptiveMobile shared its findings with the GSM Association (GSMA) on February 4, 2021, following which the … [Read more...] about New 5G Flaw Exposes Priority Networks to Location Tracking and Other Attacks
Securing industrial networks: What is ISA/IEC 62443?
Cyber attacks targeting industrial networks increased by 2000% from 2018 to 2019. Attacks on operational technology (OT) can interrupt production and revenue, expose proprietary information, or taint product quality. They can even put employees in harm’s way or damage the environment. Attacks on critical infrastructure—water, power, and transportation—can inflict devastating … [Read more...] about Securing industrial networks: What is ISA/IEC 62443?
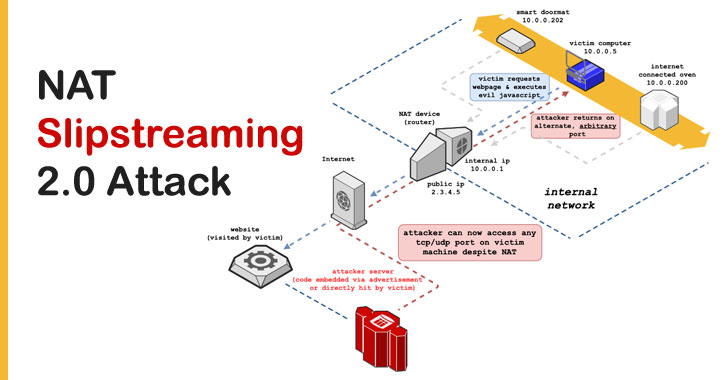
New Attack Could Let Remote Hackers Target Devices On Internal Networks
A newly devised variant of the NAT Slipstreaming attack can be leveraged to compromise and expose any device in an internal network, according to the latest research. Detailed by enterprise IoT security firm Armis, the new attack (CVE-2020-16043 and CVE-2021-23961) builds on the previously disclosed technique to bypass routers and firewalls and reach any unmanaged device within … [Read more...] about New Attack Could Let Remote Hackers Target Devices On Internal Networks
Unify security policy across hybrid networks with Cisco Defense Orchestrator
Manage a consistent posture from your physical network to the cloud all from a single pane of glass Our Applications are rapidly changing, driven in large part by the rapid adoption of public cloud services. As such, public clouds have become critical extensions of our physical environments. They provide a level of flexibility and scalability that wasn’t possible previously. … [Read more...] about Unify security policy across hybrid networks with Cisco Defense Orchestrator
Threat Spotlight: Valak Slithers Its Way Into Manufacturing and Transportation Networks
Cisco Blogs / Security / Threat Research / Threat Spotlight: Valak Slithers Its Way Into Manufacturing and Transportation Networks By Nick Biasini, Edmund Brumaghin and Mariano Graziano. Threat summary Attackers are actively distributing the Valak malware family around the globe, with enterprises, in particular, being targeted. These campaigns make use of existing … [Read more...] about Threat Spotlight: Valak Slithers Its Way Into Manufacturing and Transportation Networks
Choosing the right security analytics solution as networks expand: competitive considerations and customer validation
May you live in interesting times… We’re currently witnessing a fundamental shift towards a more remote workforce amidst the tumultuous world events of 2020. This recent development made me recall the tongue-in-cheek, 19th century adage – “May you live in interesting times”. This old proverb served as a curse disguised as a fortuitous blessing, as the concept of “interesting … [Read more...] about Choosing the right security analytics solution as networks expand: competitive considerations and customer validation