Cybercriminals around the world keep honing their schemes to steal accounts in WhatsApp, Telegram, and other popular messaging apps – and any of us could fall for their scams. Only by becoming a victim of such an attack can you fully appreciate how vital a tool instant messaging has become, and how diverse the damage from hacking a WhatsApp or Telegram account may be. But … [Read more...] about Protecting WhatsApp and Telegram accounts from hacking and hijacking in 2025
Protecting
Protecting California’s workforce: EDD’s cybersecurity evolution after COVID-19
Enhancing cybersecurity resilience and operational efficiency with ElasticThe Employment Development Department (EDD) of California plays a vital role in administering essential services, including unemployment insurance, disability insurance, paid family leave, tax collection, and job matching. The onset of COVID-19 and subsequent surge in cyber threats prompted a significant … [Read more...] about Protecting California’s workforce: EDD’s cybersecurity evolution after COVID-19
Protecting Tomorrow’s World: Shaping the Cyber-Physical Future
The lines between digital and physical realms increasingly blur. While this opens countless opportunities for businesses, it also brings numerous challenges. In our recent webinar, Shaping the Cyber-Physical Future: Trends, Challenges, and Opportunities for 2025, we explored the different factors shaping the cyber-physical future. In an insightful conversation with industry … [Read more...] about Protecting Tomorrow’s World: Shaping the Cyber-Physical Future
Protecting Against regreSSHion with Secure Workload
On July 1, 2024, the Qualys Threat Research Unit (TRU) disclosed an unauthenticated, remote code execution vulnerability that affects the OpenSSH server (sshd) in glibc-based Linux systems. [For more information visit Qualys Security Advisory and our Cisco Security Advisory on regreSSHion (July 2024).] Now we have seen how CVE-2024-6387 has taken the internet by storm, making … [Read more...] about Protecting Against regreSSHion with Secure Workload
Protecting Employees’ Sensitive Data on the Web
Organizations are increasingly concerned about high-profile employees’ information being exposed on the deep and dark web. The CrowdStrike Counter Adversary Operations team is often asked to find fake social media accounts and personally identifiable information (PII) that might be exposed. Impersonations and leaked PII can unravel lives and ruin the reputations of individuals … [Read more...] about Protecting Employees’ Sensitive Data on the Web
Protecting Your Microsoft IIS Servers Against Malware Attacks
Microsoft Internet Information Services (IIS) is a web server software package designed for Windows Server. Organizations commonly use Microsoft IIS servers to host websites, files, and other content on the web. Threat actors increasingly target these Internet-facing resources as low-hanging fruit for finding and exploiting vulnerabilities that facilitate access to IT … [Read more...] about Protecting Your Microsoft IIS Servers Against Malware Attacks
Defense-in-depth Principles for Protecting Cloud Workloads
Migrating to the cloud has allowed many organizations to reduce costs, innovate faster and deliver business results more effectively. However, as businesses expand their cloud investments, they must adapt their security strategies to stay one step ahead of threats that target their expanded environment. Managing, securing and having visibility across endpoints, networks and … [Read more...] about Defense-in-depth Principles for Protecting Cloud Workloads
Protecting against Log4j with Secure Firewall & Secure IPS
The Apache Log4j vulnerability (CVE-2021-44228) has taken the Internet by storm in the past few days. This blog details quick ways Secure Firewall Threat Defense (FTD) and Secure IPS users can protect against attacks leveraging this vulnerability while patching their infrastructure. Talos first released updated Snort rules on Friday, December 10. For customers inspecting … [Read more...] about Protecting against Log4j with Secure Firewall & Secure IPS
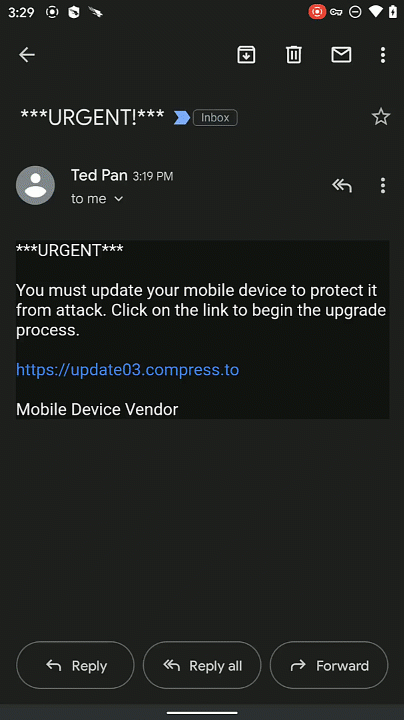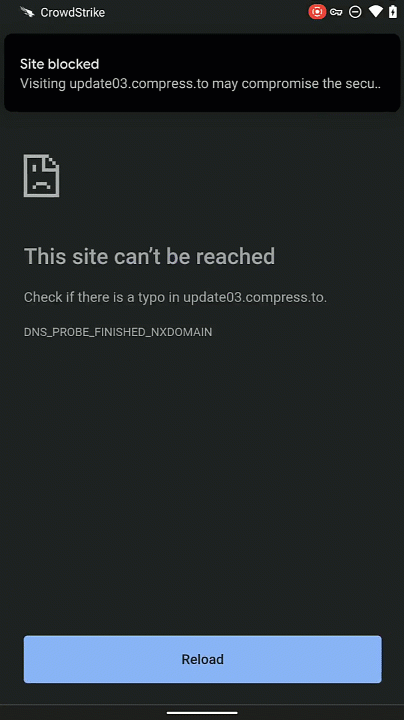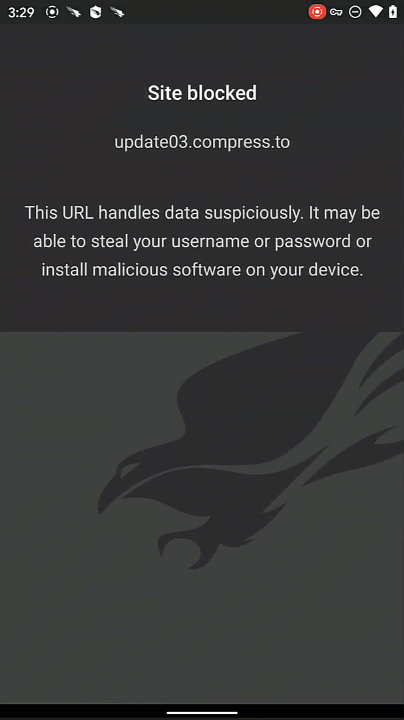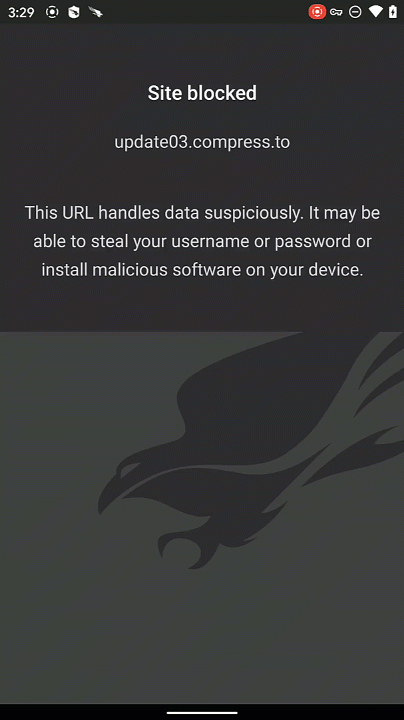
Protecting Users from Malicious Sites with Falcon for Mobile
Introduction Today, mobile devices are ubiquitous within enterprise environments. But with their proliferation, it provides adversaries with yet another attack surface with which they can target users and cause a breach. From phishing attacks to malicious apps, mobile users tend to let their guard down and potentially click on obfuscated links to malicious sites. Falcon for … [Read more...] about Protecting Users from Malicious Sites with Falcon for Mobile
Is your internet service provider protecting you online?
Security is more critical today than it has ever been. We are constantly bombarded with buzzwords and acronyms. You hear cyber this and that, malware, SIG, DDOS, MFA, the list goes on… They are all very important, but we rarely hear the words “service provider security infrastructure.” It’s fair to say the world has come a long way since the early ‘90s, and with that, so have … [Read more...] about Is your internet service provider protecting you online?