Today’s privacy and security conversations often happen in silos, but key privacy principles from decades ago remind us that they are intertwined, especially in the face of today’s risks. January 28, 2022, marks 15 years since the first Data Protection Day was proclaimed in Europe and 13 years since Data Privacy Day was first recognized by the United States. Since then, dozens … [Read more...] about Data Protection Day: No Privacy without Security
Protection
Cyber Threat Protection — It All Starts with Visibility
Just as animals use their senses to detect danger, cybersecurity depends on sensors to identify signals in the computing environment that may signal danger. The more highly tuned, diverse and coordinated the senses, the more likely one is to detect important signals that indicate danger. This, however, can be a double-edged sword. Too many signals with too little advanced … [Read more...] about Cyber Threat Protection — It All Starts with Visibility
4 Keys to Selecting a Cloud Workload Protection Platform
Security budgets are not infinite. Every dollar spent must produce a return on investment (ROI) in the form of better detection or prevention. Getting the highest ROI for security purchases is a key consideration for any IT leader. But the path to achieving that goal is not always easy to find. It is tempting for CISOs and CIOs to succumb to “shiny toy” syndrome: to buy the … [Read more...] about 4 Keys to Selecting a Cloud Workload Protection Platform
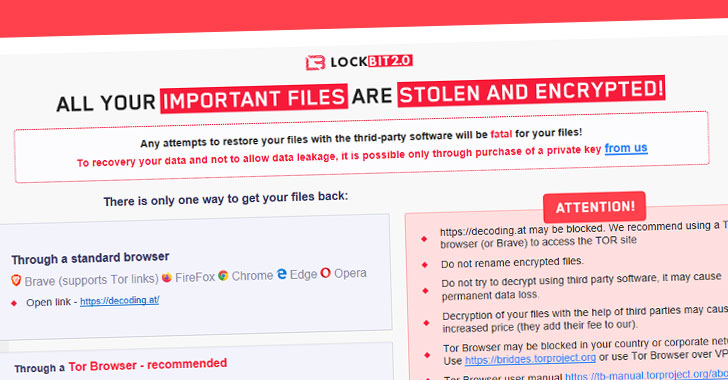
LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
A new ransomware family that emerged last month comes with its own bag of tricks to bypass ransomware protection by leveraging a novel technique called "intermittent encryption." Called LockFile, the operators of the ransomware has been found exploiting recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows servers and deploy file-encrypting malware … [Read more...] about LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
Threat Protection: The REvil Ransomware
The REvil ransomware family has been in the news due to its involvement in high-profile incidents, such as the JBS cyberattack and the Kaseya supply chain attack. Yet this threat carries a much more storied history, with varying functionality from one campaign to the next. The threat actors behind REvil attacks operate under a ransomware-as-a-service model. In this type of … [Read more...] about Threat Protection: The REvil Ransomware
Passwordless Protection: The Next Step in Zero Trust
A Zero Trust Approach With the increasing threat landscape and recent workplace shifts to support remote users, many companies are deploying a Zero Trust security model to mitigate, detect, and respond to cyber risks across their environment. Zero Trust principles help protect against identity and access-based security risks by requiring all users, whether inside or outside the … [Read more...] about Passwordless Protection: The Next Step in Zero Trust
New Study: Reducing Security Incidents and Impact with Endpoint Protection
The way we work has fundamentally changed since the beginning of last year. We are now part of a new, massively remote workforce that is here to stay. Organizations have long struggled with maintaining visibility across an increasingly complex attack surface. Now, with more employees relying on access to resources and applications from outside the office, endpoint protection … [Read more...] about New Study: Reducing Security Incidents and Impact with Endpoint Protection
Can Data Protection Systems Prevent Data At Rest Leakage?
Protection against insider risks works when the process involves controlling the data transfer channels or examining data sources. One approach involves preventing USB flash drives from being copied or sending them over email. The second one concerns preventing leakage or fraud in which an insider accesses files or databases with harmful intentions. What's the best way to … [Read more...] about Can Data Protection Systems Prevent Data At Rest Leakage?
The 2021 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP): Our takeaways
Key Takeaways Going back to my days as one of the co-founders of Immunet Corporation more than a decade ago, the goal was always to deliver the most efficient and dynamic endpoint protection. Long before there was “EDR”, we were already going beyond traditional AV and well into delivering cloud-native detection and response capabilities to defend the endpoint. But we were quick … [Read more...] about The 2021 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP): Our takeaways
How Cyrebro Can Unify Multiple Cybersecurity Defenses to Optimize Protection
Many enterprises rely on more than one security tool to protect their technology assets, devices, and networks. This is particularly true for organizations that use hybrid systems or a combination of cloud and local applications. Likewise, companies whose networks include a multitude of smartphones and IoT devices are likely to deploy multiple security solutions suitable for … [Read more...] about How Cyrebro Can Unify Multiple Cybersecurity Defenses to Optimize Protection