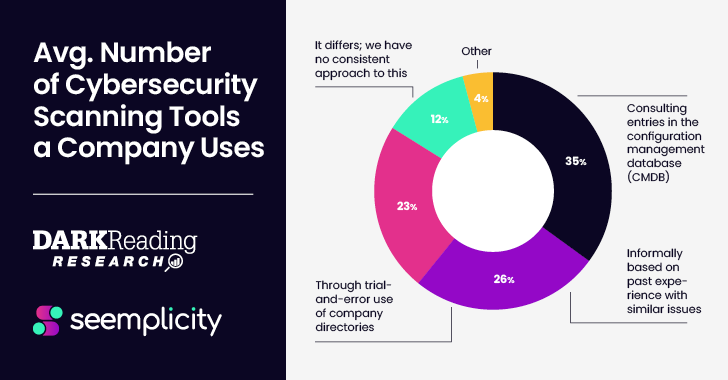
Aug 29, 2023The Hacker NewsRemedial Operations Ask any security professional and they'll tell you that remediating risks from various siloed security scanning tools requires a tedious and labor-intensive series of steps focused on deduplication, prioritization, and routing of issues to an appropriate "fixer" somewhere in the organization. This burden on already … [Read more...] about Survey Provides Takeaways for Security Pros to Operationalize their Remediation Life Cycle
Remediation
How Attack Surface Management Prioritizes Vulnerability Remediation
As the business environment becomes increasingly connected, organizations' attack surfaces continue to expand, making it challenging to map and secure both known and unknown assets. In particular, unknown assets present security challenges related to shadow IT, misconfigurations, ineffective scan coverage, among others. Given attack surface sprawl and evolving threats, many … [Read more...] about How Attack Surface Management Prioritizes Vulnerability Remediation
Kenna.VM Premier: Accelerate Vulnerability Management with Cisco Talos Intel and Remediation Analytics
New level unlocked. The next step for Kenna.VM users who are maturing their risk-based vulnerability management program is Kenna.VM Premier—and it’s live. The Cisco Kenna team is excited to release a new tier of the Kenna Security platform designed specifically for customers or prospects that have reached a point of maturity in which they can and want to do more with their … [Read more...] about Kenna.VM Premier: Accelerate Vulnerability Management with Cisco Talos Intel and Remediation Analytics
How the CrowdStrike Falcon Platform Automates Vulnerability Remediation
Adversaries are becoming more adept and sophisticated in their attacks. Taking advantage of vulnerabilities present in major software is often an attractive entry point for establishing a campaign within an enterprise environment. The CrowdStrike 2022 Global Threat Report highlights how adversaries continue to shift tradecraft and weaponize vulnerabilities to evade detection … [Read more...] about How the CrowdStrike Falcon Platform Automates Vulnerability Remediation
Automating Remote Remediation of TrickBot: Part 2
This is Part Two in a two-part blog series covering the CrowdStrike® Falcon Complete™ team’s ability to remotely remediate “TrickBot,” a modular trojan that is particularly devastating when paired with “Ryuk” ransomware. This deep dive analyzes an automated methodology that leverages the Falcon Real Time Response (RTR) API in addition to PowerShell and Python scripting in order … [Read more...] about Automating Remote Remediation of TrickBot: Part 2
Automating Remote Remediation of TrickBot: Part 1
The combination of commodity banking malware and ransomware is nothing new in the threat landscape. Adversaries continue to develop new tactics that enhance their capabilities to quickly spread malware infections across an environment, seize control of systems and hold organizations hostage pending a ransom payment. The adversary tracked as WIZARD SPIDER has used “big game … [Read more...] about Automating Remote Remediation of TrickBot: Part 1
CrowdStrike’s Real Time Response Enables Remote Remediation
Introduction Remote systems can be easy targets for attackers. When these systems are compromised, responders need to work quickly to understand the attack and take action to remediate. The responders need remote system visibility and access since users can’t walk a laptop over to IT. Do responders have the visibility and context they need to understand the threat? Can they … [Read more...] about CrowdStrike’s Real Time Response Enables Remote Remediation