I have not been inside an office building for 12 months. A sentence I did not imagine writing anytime soon. Last February, everything changed. And when we pause to reflect, we have to consider that, of the many dramatic impacts to our lives, to society, and the world, in the realm of the professional, one of the most impactful changes has been the fact that many of us no longer … [Read more...] about Balancing Safety and Security During a Year of Remote Working
remote
Visualize and validate policy, increase remote worker telemetry, and embrace zero trust with Network Analytics Release 7.3.1
We have heard it before. Securing your organization isn’t getting any easier. The remote workforce is expanding the attack surface. We need context from users and endpoints to control proper access, and IT teams need to ensure our data stores are resilient and always available to gain the telemetry they need to reduce risk. Yes, zero trust is a great approach, but network … [Read more...] about Visualize and validate policy, increase remote worker telemetry, and embrace zero trust with Network Analytics Release 7.3.1
New Attack Could Let Remote Hackers Target Devices On Internal Networks
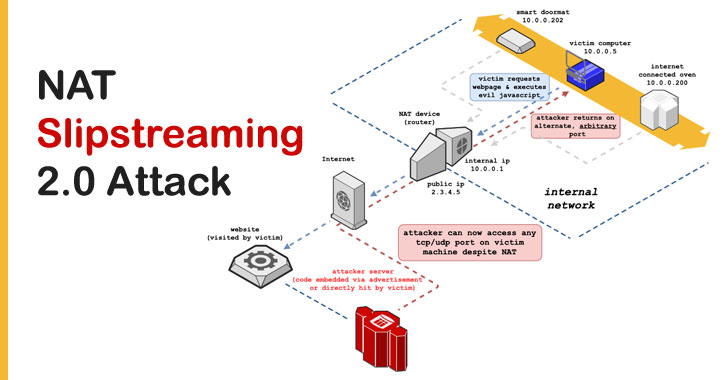
A newly devised variant of the NAT Slipstreaming attack can be leveraged to compromise and expose any device in an internal network, according to the latest research. Detailed by enterprise IoT security firm Armis, the new attack (CVE-2020-16043 and CVE-2021-23961) builds on the previously disclosed technique to bypass routers and firewalls and reach any unmanaged device within … [Read more...] about New Attack Could Let Remote Hackers Target Devices On Internal Networks
#CiscoChat Live: Recapture Your Time and Get More Out of Secure Remote Working
How do you feel when you hear phrases like, “the pandemic”, “remote working”, “the new (or next) normal”? Fatigued? You are not alone. Most of us are experiencing online fatigue as a result of working from home for months now. Worse, we’re physically and mentally fatigued by the shift to the “always on” mode with remote working. It doesn’t take much if you think about it. Just … [Read more...] about #CiscoChat Live: Recapture Your Time and Get More Out of Secure Remote Working
RDP and the remote desktop
There are two sides to the shift to remote work. On one side, you need to ensure that your people have access to equipment that will allow them to perform their day-to-day tasks. On the other, there needs to be a way to connect back to company resources that will help workers complete those tasks. One solution to both of these aspects that has proven useful is remote desktop … [Read more...] about RDP and the remote desktop
Critical Flaws Discovered in Popular Industrial Remote Access Systems
Cybersecurity researchers have found critical security flaws in two popular industrial remote access systems that can be exploited to ban access to industrial production floors, hack into company networks, tamper with data, and even steal sensitive business secrets. The flaws, discovered by Tel Aviv-based OTORIO, were identified in B&R Automation's SiteManager and … [Read more...] about Critical Flaws Discovered in Popular Industrial Remote Access Systems
Offline Protection for Remote Systems
Introduction Remote working has many employees not only working from home but really from anywhere. Services necessary to work remotely such as VPN, cloud-based applications and internet access vary along with the reliability of those services. Inconsistent service availability means employees work both online and offline. As attacks against remote systems continue to surface, … [Read more...] about Offline Protection for Remote Systems
Major Instagram App Bug Could’ve Given Hackers Remote Access to Your Phone
Ever wonder how hackers can hack your smartphone remotely? In a report shared with The Hacker News today, Check Point researchers disclosed details about a critical vulnerability in Instagram's Android app that could have allowed remote attackers to take control over a targeted device just by sending victims a specially crafted image. What's more worrisome is that the flaw not … [Read more...] about Major Instagram App Bug Could’ve Given Hackers Remote Access to Your Phone
Cisco Secure Remote Worker Architecture for Azure
Today companies are investing in empowering their workforce to have a secure connection to the resources hosted in the Cloud. Cisco provides a secure remote worker solution that uses the Cisco AnyConnect Secure Mobility Client, Cisco Duo, Cisco Umbrella, and Cisco Advanced Malware Protection (AMP) for Endpoints. Cisco AnyConnect Secure Mobility Client: Cisco AnyConnect Secure … [Read more...] about Cisco Secure Remote Worker Architecture for Azure
Crossing the Chasm of Remote Access Doesn’t Have to Be Scary
And just like that, everything changed On March 9, 2020, like so many other workers around the globe, I was told to stay home. There was a sudden, collective agreement: going into our place of business was no longer an option. And I was grateful. I was grateful that my company had the technology in place to ensure that I could not only keep working, but we could all thrive … [Read more...] about Crossing the Chasm of Remote Access Doesn’t Have to Be Scary