Summer is just about over. You may have missed it as we kept our distance and curbed many of our travel plans. As the reality of a continued work from home, school from home, and stay at home hit our home; we hit the road to capture a bit of summer, heading into the Pacific North West. While watching the clouds roll above the remote beaches along the Oregon coast, I wondered if … [Read more...] about Tame the wilderness of remote access and answer the call of the mobility
remote
Securing Remote Work: Questions You Should Ask
No one could have anticipated the overnight need to rapidly pivot from working in an office to working remotely. Today, 76% of employees are working from home, needing remote access to corporate systems from all sorts of devices from unknown, potentially unsecure home networks. But with 68% of breaches originating on endpoints and bad actors intensifying pandemic-themed malware … [Read more...] about Securing Remote Work: Questions You Should Ask
Flaws in Samsung Phones Exposed Android Users to Remote Attacks
New research disclosed a string of severe security vulnerabilities in the 'Find My Mobile'—an Android app that comes pre-installed on most Samsung smartphones—that could have allowed remote attackers to track victims' real-time location, monitor phone calls, and messages, and even delete data stored on the phone.Portugal-based cybersecurity services provider Char49 revealed its … [Read more...] about Flaws in Samsung Phones Exposed Android Users to Remote Attacks
New Attack Leverages HTTP/2 for Effective Remote Timing Side-Channel Leaks
Security researchers have outlined a new technique that renders a remote timing-based side-channel attack more effective regardless of the network congestion between the adversary and the target server.Remote timing attacks that work over a network connection are predominantly affected by variations in network transmission time (or jitter), which, in turn, depends on the load … [Read more...] about New Attack Leverages HTTP/2 for Effective Remote Timing Side-Channel Leaks
Actionable Indicators to Protect a Remote Workforce
Introduction As the world continues to adjust to the new reality of employees working from anywhere and at any time, security teams are working overtime to protect users from cybercriminals that use novel themes and lures to mount attacks. Organizations are faced with a dilemma: Security teams are expected to be aware of the latest global techniques and campaigns, but with … [Read more...] about Actionable Indicators to Protect a Remote Workforce
Securing Remote Work: Protecting Endpoints the Right Way
The remote work environment has been around for years. In fact, 56% of employees in the US have a job where some of what they do could be done remotely even before the pandemic. However, no one could have predicted the sudden need to fast-track remote worker access to corporate systems. Overnight, we’ve gone from environments where most of us were confined to an office … [Read more...] about Securing Remote Work: Protecting Endpoints the Right Way
Flexible Policy Management for Remote Systems
Introduction As organizations shift to supporting more remote workers, protection policies for laptops and systems that are no longer behind traditional perimeter defenses need to be updated. Can administrators quickly and easily update policies to ensure continuous protection for these remote systems? Video Protection Without Complexity is More Important … [Read more...] about Flexible Policy Management for Remote Systems
Automating Remote Remediation of TrickBot: Part 2
This is Part Two in a two-part blog series covering the CrowdStrike® Falcon Complete™ team’s ability to remotely remediate “TrickBot,” a modular trojan that is particularly devastating when paired with “Ryuk” ransomware. This deep dive analyzes an automated methodology that leverages the Falcon Real Time Response (RTR) API in addition to PowerShell and Python scripting in order … [Read more...] about Automating Remote Remediation of TrickBot: Part 2
Automating Remote Remediation of TrickBot: Part 1
The combination of commodity banking malware and ransomware is nothing new in the threat landscape. Adversaries continue to develop new tactics that enhance their capabilities to quickly spread malware infections across an environment, seize control of systems and hold organizations hostage pending a ransom payment. The adversary tracked as WIZARD SPIDER has used “big game … [Read more...] about Automating Remote Remediation of TrickBot: Part 1
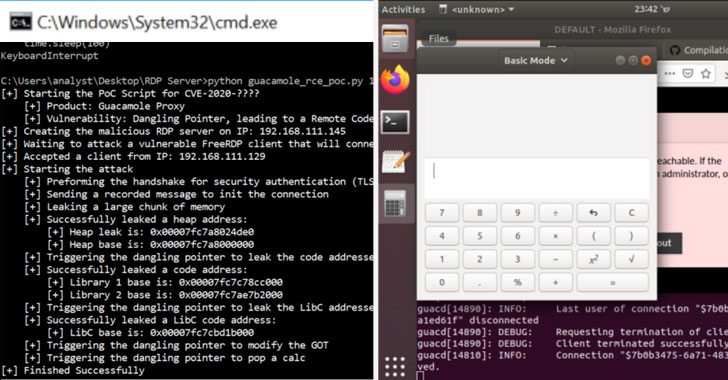
Critical Apache Guacamole Flaws Put Remote Desktops at Risk of Hacking
A new research has uncovered multiple critical reverse RDP vulnerabilities in Apache Guacamole, a popular remote desktop application used by system administrators to access and manage Windows and Linux machines remotely.The reported flaws could potentially let bad actors achieve full control over the Guacamole server, intercept, and control all other connected … [Read more...] about Critical Apache Guacamole Flaws Put Remote Desktops at Risk of Hacking