With each new version of the Android operating system, new features are added to protect users from malware. For example, Android 13 introduced Restricted Settings. In this post, we’ll discuss what this feature involves, what it’s designed to protect against, and how effectively it does its job (spoiler: not very well). What are Restricted Settings? How do Restricted Settings … [Read more...] about Restricted Settings in Android 13 and 14
Restricted
New Zoom Screen-Sharing Bug Lets Other Users Access Restricted Apps
A newly discovered glitch in Zoom's screen sharing feature can accidentally leak sensitive information to other attendees in a call, according to the latest findings. Tracked as CVE-2021-28133, the unpatched security vulnerability makes it possible to reveal contents of applications that are not shared, but only briefly, thereby making it harder to exploit it in the wild. It's … [Read more...] about New Zoom Screen-Sharing Bug Lets Other Users Access Restricted Apps
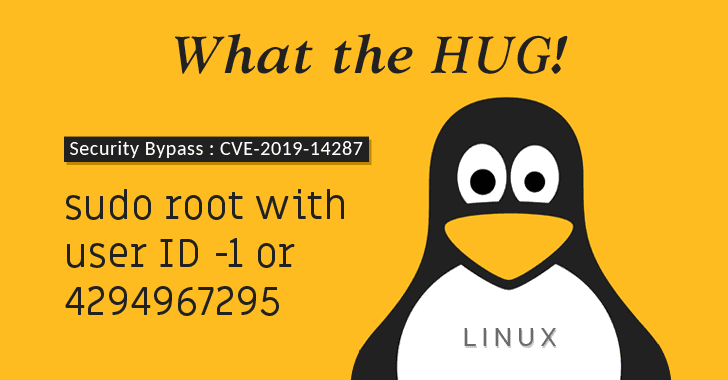
Sudo Flaw Lets Linux Users Run Commands As Root Even When They’re Restricted
Attention Linux Users!A new vulnerability has been discovered in Sudo—one of the most important, powerful, and commonly used utilities that comes as a core command installed on almost every UNIX and Linux-based operating system.The vulnerability in question is a sudo security policy bypass issue that could allow a malicious user or a program to execute arbitrary commands as … [Read more...] about Sudo Flaw Lets Linux Users Run Commands As Root Even When They’re Restricted