Observability is critical for effective security implementation. It allows organizations to monitor their systems, applications, and networks in real-time; detect and investigate security incidents; and quickly respond to them. But having multiple tools and solutions for observability can create a fragmented view of the environment, making it difficult to gain a comprehensive … [Read more...] about The importance of a unified observability solution in security implementation
security
Four top tips for blockchain asset security
Cryptocurrencies and other blockchain assets aren’t protected by bank guarantees or other “traditional” financial security measures. Therefore, investors need to take every possible precaution to protect themselves. Here are four key tips for storing cryptocurrencies securely and protecting other cryptoassets. 1. Expect scams The variety of different cryptoassets combined with … [Read more...] about Four top tips for blockchain asset security
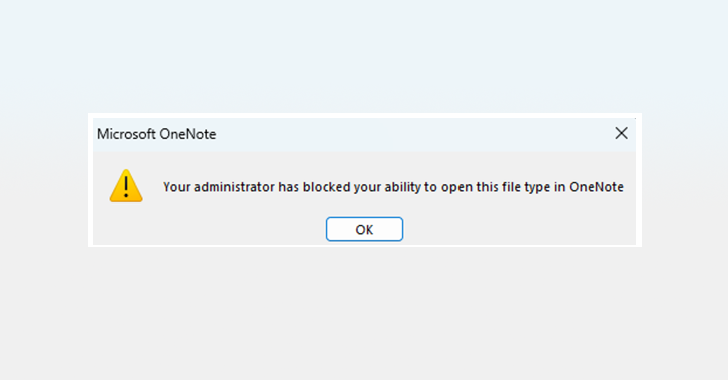
Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions
Microsoft has announced plans to automatically block embedded files with "dangerous extensions" in OneNote following reports that the note-taking service is being increasingly abused for malware delivery. Up until now, users were shown a dialog warning them that opening such attachments could harm their computer and data, but it was possible to dismiss the prompt and open the … [Read more...] about Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions
Evades Macro Security via OneNote Attachments
Mar 20, 2023Ravie LakshmananEndpoint Security / Email Security The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems. Emotet, linked to a threat actor tracked as Gold Crestwood, Mummy Spider, or TA542, continues to be a … [Read more...] about Evades Macro Security via OneNote Attachments
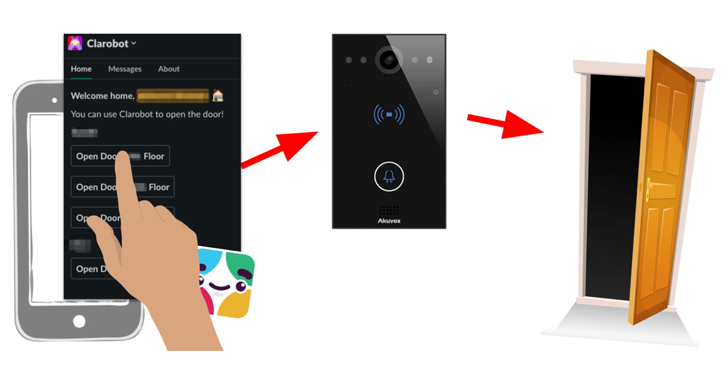
Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom
Mar 13, 2023Ravie LakshmananEnterprise Security / Privacy More than a dozen security flaws have been disclosed in E11, a smart intercom product made by Chinese company Akuvox. "The vulnerabilities could allow attackers to execute code remotely in order to activate and control the device's camera and microphone, steal video and images, or gain a network foothold," Claroty … [Read more...] about Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom
Security and IT Teams No Longer Need To Pay For SaaS-Shadow IT Discovery
Mar 04, 2023The Hacker NewsSaaS Security / Cyber Security This past January, a SaaS Security Posture Management (SSPM) company named Wing Security (Wing) made waves with the launch of its free SaaS-Shadow IT discovery solution. Cloud-based companies were invited to gain insight into their employees' SaaS usage through a completely free, self-service product that operates on a … [Read more...] about Security and IT Teams No Longer Need To Pay For SaaS-Shadow IT Discovery
CrowdStrike Ranked #1 in IDC Endpoint Security Market Shares Report
CrowdStrike maintains endpoint security market leadership with a #1 ranking in IDC’s 2021-2022 report, and has been awarded Best Endpoint Detection and Response and Best Product Development by SE Labs. These recognitions validate CrowdStrike as the industry’s market and innovation leader in endpoint security. We’re honored to share CrowdStrike has been ranked #1 out of 26 … [Read more...] about CrowdStrike Ranked #1 in IDC Endpoint Security Market Shares Report
3 Ways Visualization Improves Cloud Asset Management and Security
Public cloud services and cloud assets are agile and dynamic environments. Close oversight of these assets is a critical component of your asset management and security practices. While it’s important to understand the relationships and potential vulnerabilities of your cloud assets, the practice of managing these systems is complicated by the ever-changing nature of cloud … [Read more...] about 3 Ways Visualization Improves Cloud Asset Management and Security
Google Teams Up with Ecosystem Partners to Enhance Security of SoC Processors
Feb 24, 2023Ravie LakshmananMobile Security / Firmware Google said it's working with ecosystem partners to harden the security of firmware that interacts with Android. While the Android operating system runs on what's called the application processor (AP), it's just one of the many processors of a system-on-chip (SoC) that cater to various tasks like cellular communications … [Read more...] about Google Teams Up with Ecosystem Partners to Enhance Security of SoC Processors
Reddit Suffers Security Breach Exposing Internal Documents and Source Code
Feb 10, 2023Ravie LakshmananData Breach / Source Code Popular social news aggregation platform Reddit has disclosed that it was the victim of a security incident that enabled unidentified threat actors to gain unauthorized access to internal documents, code, and some unspecified business systems. The company blamed it on a "sophisticated and highly-targeted phishing attack" … [Read more...] about Reddit Suffers Security Breach Exposing Internal Documents and Source Code