In the ever-evolving landscape of cloud security, staying ahead of the curve is paramount. Today, we are announcing an exciting enhancement: CrowdStrike Falcon® Cloud Security now supports Google Kubernetes Engine (GKE) Autopilot. This integration marks an important milestone in our commitment to providing cutting-edge DevSecOps-focused security and solutions for modern cloud … [Read more...] about Secure More GCP Workloads with GKE Autopilot Supported by Falcon Cloud Security
security
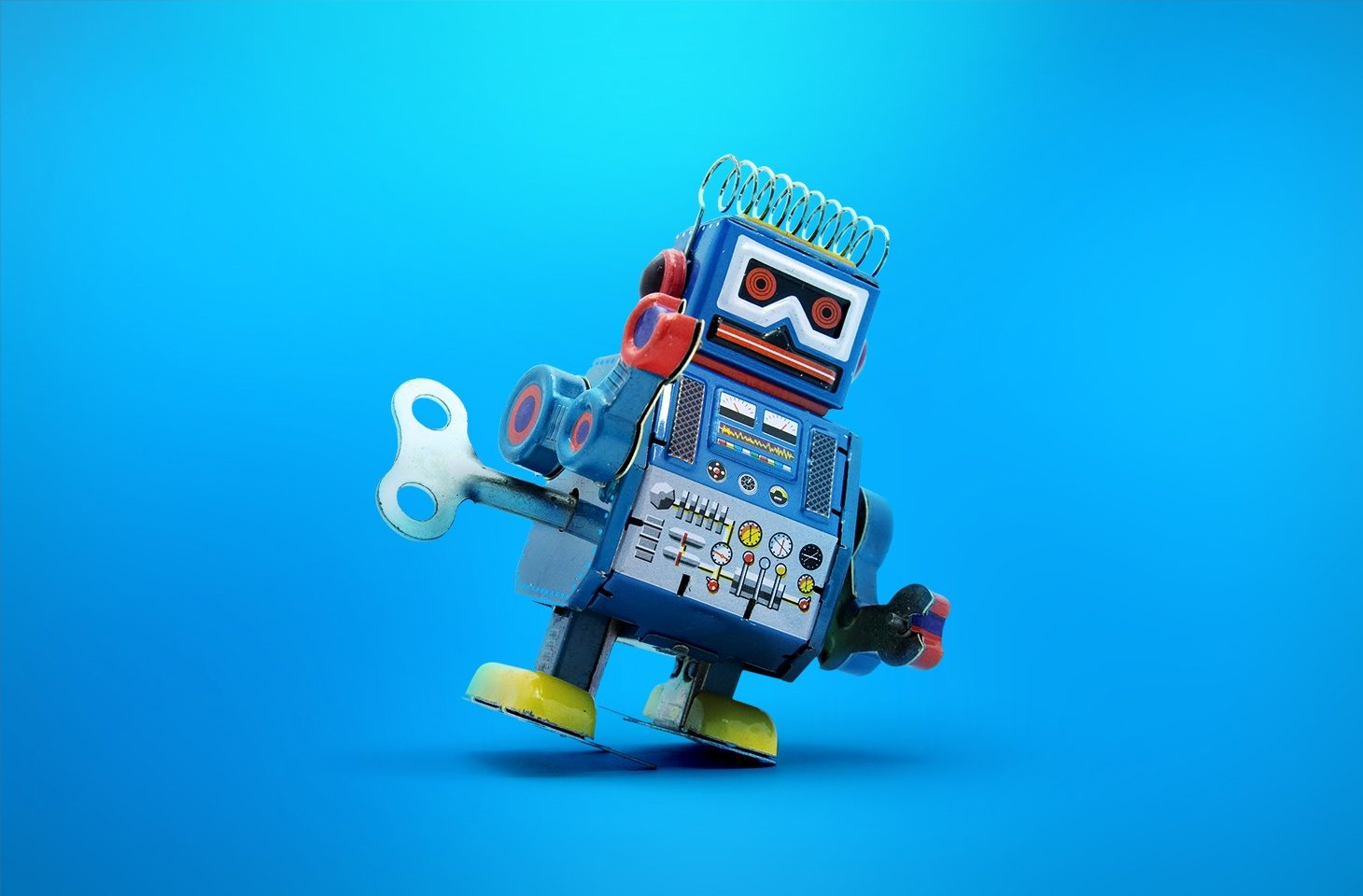
Toy robot security issues | Kaspersky official blog
Kaspersky experts recently studied the security of a popular toy robot model, finding major issues that allowed malicious actors to make a video call to any such robot, hijack the parental account, or, potentially, even upload modified firmware. Read on for the details. What a toy robot can do The toy robot model that we studied is a kind of hybrid between a smartphone/tablet … [Read more...] about Toy robot security issues | Kaspersky official blog
Aembit Strengthens Security for Workload-to-Workload Access
The rise of distributed cloud services and the omnipresence of APIs has caused cloud-native application architecture to become highly fragmented. Enforcing secure access is a critical step in strengthening security as IT environments become more complex — but for many organizations, ensuring secure access across this evolving architecture is a constant challenge. Existing … [Read more...] about Aembit Strengthens Security for Workload-to-Workload Access
Key Findings from the CrowdStrike 2024 State of Application Security Report
As organizations shift their applications and operations to the cloud and increasingly drive revenues through software, cloud-native applications and APIs have emerged among the greatest areas of modern security risk. According to publicly available data, eight of the top 10 data breaches of 2023 were related to application attack surfaces.1 These eight breaches alone exposed … [Read more...] about Key Findings from the CrowdStrike 2024 State of Application Security Report
How Elastic AI Assistant for Security and Amazon Bedrock can empower security analysts for enhanced performance
Elastic Cloud enables users to search, solve, and succeed with one platform, three search-powered solutions, built on a single technology stack. It is designed for any type of data — deployable anywhere — to solve your search, observability, and security challenges. Elastic® users benefit from a unified data analytics platform, which dramatically reduces the cost and complexity … [Read more...] about How Elastic AI Assistant for Security and Amazon Bedrock can empower security analysts for enhanced performance
EMA explores Elastic AI Assistant for Security
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any … [Read more...] about EMA explores Elastic AI Assistant for Security
Three Ways To Supercharge Your Software Supply Chain Security
Jan 04, 2024The Hacker NewsEthical Hacking / Vulnerability Assessment Section four of the "Executive Order on Improving the Nation's Cybersecurity" introduced a lot of people in tech to the concept of a "Software Supply Chain" and securing it. If you make software and ever hope to sell it to one or more federal agencies, you have to pay attention to this. Even if you never … [Read more...] about Three Ways To Supercharge Your Software Supply Chain Security
Top 5 reasons to upgrade Elastic Security
Let’s start with assurances that we’re not here to heap anxiety on anyone’s fear of missing out. That being said, we do want to make sure you’re aware of all the goodness that is available in Elastic Security, especially if you’re on an older version. It can be hard to find time to dig into every new release, to see what new features might be available, or check on ways to … [Read more...] about Top 5 reasons to upgrade Elastic Security
MongoDB Suffers Security Breach, Exposing Customer Data
Dec 17, 2023NewsroomCyber Attack / Data Security MongoDB on Saturday disclosed it's actively investigating a security incident that has led to unauthorized access to "certain" corporate systems, resulting in the exposure of customer account metadata and contact information. The American database software company said it first detected anomalous activity on December 13, 2023, … [Read more...] about MongoDB Suffers Security Breach, Exposing Customer Data
China’s MIIT Introduces Color-Coded Action Plan for Data Security Incidents
Dec 16, 2023NewsroomCyber Security / Incident Response China's Ministry of Industry and Information Technology (MIIT) on Friday unveiled draft proposals detailing its plans to tackle data security events in the country using a color-coded system. The effort is designed to "improve the comprehensive response capacity for data security incidents, to ensure timely and effective … [Read more...] about China’s MIIT Introduces Color-Coded Action Plan for Data Security Incidents