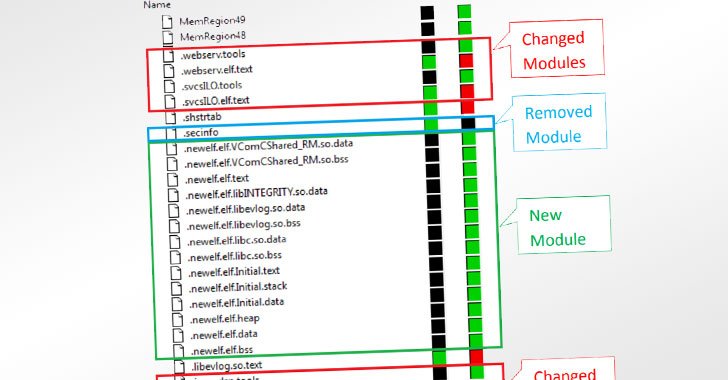
A previously unknown rootkit has been found setting its sights on Hewlett-Packard Enterprise's Integrated Lights-Out (iLO) server management technology to carry out in-the-wild attacks that tamper with the firmware modules and completely wipe data off the infected systems. The discovery, which is the first instance of real-world malware in iLO firmware, was documented by … [Read more...] about New iLOBleed Rootkit Targeting HP Enterprise Servers with Data Wiping Attacks
Servers
Experts Uncover Several C&C Servers Linked to WellMess Malware
Cybersecurity researchers on Friday unmasked new command-and-control (C2) infrastructure belonging to the Russian threat actor tracked as APT29, aka Cozy Bear, that has been spotted actively serving WellMess malware as part of an ongoing attack campaign. More than 30 C2 servers operated by the Russian foreign intelligence have been uncovered, Microsoft-owned cybersecurity … [Read more...] about Experts Uncover Several C&C Servers Linked to WellMess Malware
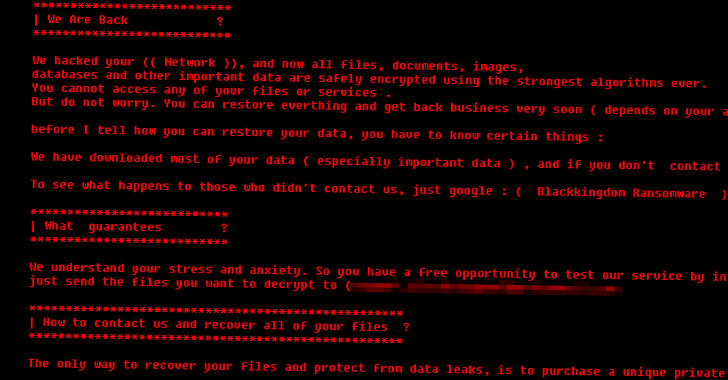
Black Kingdom Ransomware Hunting Unpatched Microsoft Exchange Servers
More than a week after Microsoft released a one-click mitigation tool to mitigate cyberattacks targeting on-premises Exchange servers, the company disclosed that patches have been applied to 92% of all internet-facing servers affected by the ProxyLogon vulnerabilities. The development, a 43% improvement from the previous week, caps off a whirlwind of espionage and malware … [Read more...] about Black Kingdom Ransomware Hunting Unpatched Microsoft Exchange Servers
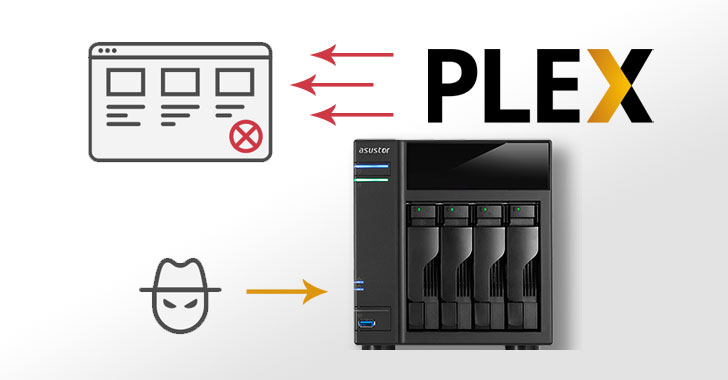
Cybercriminals Now Using Plex Media Servers to Amplify DDoS Attacks
A new distributed denial-of-service attack (DDoS) vector has ensnared Plex Media Server systems to amplify malicious traffic against targets to take them offline. "Plex's startup processes unintentionally expose a Plex UPnP-enabled service registration responder to the general Internet, where it can be abused to generate reflection/amplification DDoS attacks," Netscout … [Read more...] about Cybercriminals Now Using Plex Media Servers to Amplify DDoS Attacks
Wormable Gitpaste-12 Botnet Returns to Target Linux Servers, IoT Devices
A new wormable botnet that spreads via GitHub and Pastebin to install cryptocurrency miners and backdoors on target systems has returned with expanded capabilities to compromise web applications, IP cameras, and routers. Early last month, researchers from Juniper Threat Labs documented a crypto-mining campaign called "Gitpaste-12," which used GitHub to host malicious code … [Read more...] about Wormable Gitpaste-12 Botnet Returns to Target Linux Servers, IoT Devices
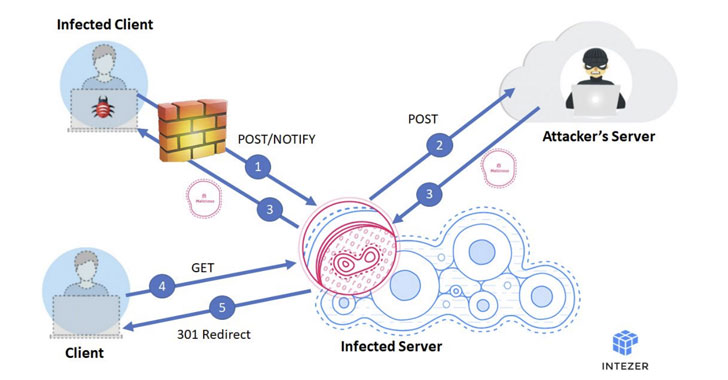
Stantinko Botnet Now Targeting Linux Servers to Hide Behind Proxies
An adware and coin-miner botnet targeting Russia, Ukraine, Belarus, and Kazakhstan at least since 2012 has now set its sights on Linux servers to fly under the radar. According to a new analysis published by Intezer today and shared with The Hacker News, the trojan masquerades as HTTPd, a commonly used program on Linux servers, and is a new version of the malware belonging to a … [Read more...] about Stantinko Botnet Now Targeting Linux Servers to Hide Behind Proxies
Premium-Rate Phone Fraudsters Hack VoIP Servers of 1200 Companies
Cybersecurity researchers today took the wraps off an on-going cyber fraud operation led by hackers in Gaza, West Bank, and Egypt to compromise VoIP servers of more than 1,200 organizations across 60 countries over the past 12 months. According to findings published by Check Point Research, the threat actors — believed to be located in the Palestinian Gaza Strip — have targeted … [Read more...] about Premium-Rate Phone Fraudsters Hack VoIP Servers of 1200 Companies
How to Run Google SERP API Without Constantly Changing Proxy Servers
You've probably run into a major problem when trying to scrape Google search results. Web scraping tools allow you to extract information from a web page. Companies and coders from across the world use them to download Google's SERP data. And they work well – for a little while. After several scrapes, Google's automated security system kicks in. Then it kicks you out. The … [Read more...] about How to Run Google SERP API Without Constantly Changing Proxy Servers
A New Fileless P2P Botnet Malware Targeting SSH Servers Worldwide
Cybersecurity researchers today took the wraps off a sophisticated, multi-functional peer-to-peer (P2P) botnet written in Golang that has been actively targeting SSH servers since January 2020.Called "FritzFrog," the modular, multi-threaded and file-less botnet has breached more than 500 servers to date, infecting well-known universities in the US and Europe, and a railway … [Read more...] about A New Fileless P2P Botnet Malware Targeting SSH Servers Worldwide
17-Year-Old Critical ‘Wormable’ RCE Vulnerability Impacts Windows DNS Servers
Cybersecurity researchers today disclosed a new highly critical "wormable" vulnerability—carrying a severity score of 10 out of 10 on the CVSS scale—affecting Windows Server versions 2003 to 2019.The 17-year-old remote code execution flaw (CVE-2020-1350), dubbed 'SigRed' by Check Point, could allow an unauthenticated, remote attacker to gain domain administrator privileges over … [Read more...] about 17-Year-Old Critical ‘Wormable’ RCE Vulnerability Impacts Windows DNS Servers