Feb 19, 2025Ravie LakshmananMobile Security / Cyber Espionage Multiple Russia-aligned threat actors have been observed targeting individuals of interest via the privacy-focused messaging app Signal to gain unauthorized access to their accounts. "The most novel and widely used technique underpinning Russian-aligned attempts to compromise Signal accounts is the abuse of the … [Read more...] about Hackers Exploit Signal’s Linked Devices Feature to Hijack Accounts via Malicious QR Codes
Signals
New RAMBO Attack Uses RAM Radio Signals to Steal Data from Air-Gapped Networks
Sep 09, 2024Ravie LakshmananVulnerability / Hardware Security A novel side-channel attack has been found to leverage radio signals emanated by a device's random access memory (RAM) as a data exfiltration mechanism, posing a threat to air-gapped networks. The technique has been codenamed RAMBO by Dr. Mordechai Guri, the head of the Offensive Cyber Research Lab in the … [Read more...] about New RAMBO Attack Uses RAM Radio Signals to Steal Data from Air-Gapped Networks
R.E.D., U.S.E., and the “Four Golden Signals”
In the fast-paced realm of DevOps and Site Reliability Engineering (SRE), success starts with effective monitoring. Understanding the fundamental metrics is crucial for identifying and mitigating issues proactively. In this article, we’ll delve into the leading metrics frameworks — R.E.D., U.S.E., and the “Four Golden Signals” — which will provide you with a solid foundation to … [Read more...] about R.E.D., U.S.E., and the “Four Golden Signals”
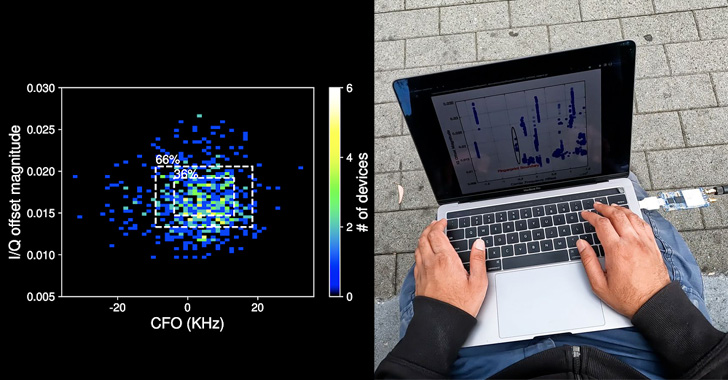
Researchers Find Bluetooth Signals Can be Fingerprinted to Track Smartphones
A new research undertaken by a group of academics from the University of California San Diego has revealed for the first time that Bluetooth signals can be fingerprinted to track smartphones (and therefore, individuals). The identification, at its core, hinges on imperfections in the Bluetooth chipset hardware introduced during the manufacturing process, resulting in a "unique … [Read more...] about Researchers Find Bluetooth Signals Can be Fingerprinted to Track Smartphones
Revisiting the Session: The Potential for Shared Signals
Sometimes in order to move forward effectively, it’s good to take stock of where we’ve been. In this blog, we’ll review a concept that has been foundational to networking and cybersecurity from the beginning: the session. Why focus on the session? As the philosophy of Zero Trust is adopted more broadly in the security industry, it’s important to understand the building blocks … [Read more...] about Revisiting the Session: The Potential for Shared Signals
An Open Security Ecosystem with Shared Signals is the Future of Zero Trust
Zero Trust: as the name implies, is the strategy by which organizations trust nothing implicitly and verify everything continuously. This industry north star is driving different architectures, frameworks, and solutions to reduce an organization’s risk and improve their security posture. Beyond the need to enforce strong authentication and authorization to establish trust of … [Read more...] about An Open Security Ecosystem with Shared Signals is the Future of Zero Trust
Creating Wireless Signals with Ethernet Cable to Steal Data from Air-Gapped Systems
A newly discovered data exfiltration mechanism employs Ethernet cables as a "transmitting antenna" to stealthily siphon highly-sensitive data from air-gapped systems, according to the latest research. "It's interesting that the wires that came to protect the air-gap become the vulnerability of the air gap in this attack," Dr. Mordechai Guri, the head of R&D in the Cyber … [Read more...] about Creating Wireless Signals with Ethernet Cable to Steal Data from Air-Gapped Systems