Oct 03, 2023The Hacker NewsAPI Security / Data Security APIs, also known as application programming interfaces, serve as the backbone of modern software applications, enabling seamless communication and data exchange between different systems and platforms. They provide developers with an interface to interact with external services, allowing them to integrate various … [Read more...] about API Security Trends 2023 – Have Organizations Improved their Security Posture?
software vulnerability
Scattered Spider Getting SaaS-y in the Cloud
LUCR-3 overlaps with groups such as Scattered Spider, Oktapus, UNC3944, and STORM-0875 and is a financially motivated attacker that leverages the Identity Provider (IDP) as initial access into an environment with the goal of stealing Intellectual Property (IP) for extortion. LUCR-3 targets Fortune 2000 companies across various sectors, including but not limited to Software, … [Read more...] about Scattered Spider Getting SaaS-y in the Cloud
FBI Warns of Rising Trend of Dual Ransomware Attacks Targeting U.S. Companies
Sep 30, 2023THNRansomware / Cyber Threat The U.S. Federal Bureau of Investigation (FBI) is warning of a new trend of dual ransomware attacks targeting the same victims, at least since July 2023. "During these attacks, cyber threat actors deployed two different ransomware variants against victim companies from the following variants: AvosLocker, Diamond, Hive, Karakurt, … [Read more...] about FBI Warns of Rising Trend of Dual Ransomware Attacks Targeting U.S. Companies
Iranian APT Group OilRig Using New Menorah Malware for Covert Operations
Sep 30, 2023THNCyber Espionage / Malware Sophisticated cyber actors backed by Iran known as OilRig have been linked to a spear-phishing campaign that infects victims with a new strain of malware called Menorah. "The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another file or … [Read more...] about Iranian APT Group OilRig Using New Menorah Malware for Covert Operations
Lazarus Group Impersonates Recruiter from Meta to Target Spanish Aerospace Firm
Sep 29, 2023THNCyber Espionage / Malware The North Korea-linked Lazarus Group has been linked to a cyber espionage attack targeting an unnamed aerospace company in Spain in which employees of the firm were approached by the threat actor posing as a recruiter for Meta. "Employees of the targeted company were contacted by a fake recruiter via LinkedIn and tricked into opening a … [Read more...] about Lazarus Group Impersonates Recruiter from Meta to Target Spanish Aerospace Firm
The Dark Side of Browser Isolation – and the Next Generation Browser Security Technologies
Sep 28, 2023The Hacker NewsBrowser Security / Cybersecurity The landscape of browser security has undergone significant changes over the past decade. While Browser Isolation was once considered the gold standard for protecting against browser exploits and malware downloads, it has become increasingly inadequate and insecure in today's SaaS-centric world. The limitations of … [Read more...] about The Dark Side of Browser Isolation – and the Next Generation Browser Security Technologies
New Survey Uncovers How Companies Are Confronting Data Security Challenges Head-On
Data security is in the headlines often, and it's almost never for a positive reason. Major breaches, new ways to hack into an organization's supposedly secure data, and other threats make the news because well, it's scary — and expensive. Data breaches, ransomware and malware attacks, and other cybercrime might be pricey to prevent, but they are even more costly when they … [Read more...] about New Survey Uncovers How Companies Are Confronting Data Security Challenges Head-On
Essential Guide to Cybersecurity Compliance
SOC 2, ISO, HIPAA, Cyber Essentials – all the security frameworks and certifications today are an acronym soup that can make even a compliance expert's head spin. If you're embarking on your compliance journey, read on to discover the differences between standards, which is best for your business, and how vulnerability management can aid compliance. What is cybersecurity … [Read more...] about Essential Guide to Cybersecurity Compliance
Ukrainian Military Targeted in Phishing Campaign Leveraging Drone Manuals
Sep 25, 2023THNCyber Attack / Phishing Ukrainian military entities are the target of a phishing campaign that leverages drone manuals as lures to deliver a Go-based open-source post-exploitation toolkit called Merlin. "Since drones or Unmanned Aerial Vehicles (UAVs) have been an integral tool used by the Ukrainian military, malware-laced lure files themed as UAVs service … [Read more...] about Ukrainian Military Targeted in Phishing Campaign Leveraging Drone Manuals
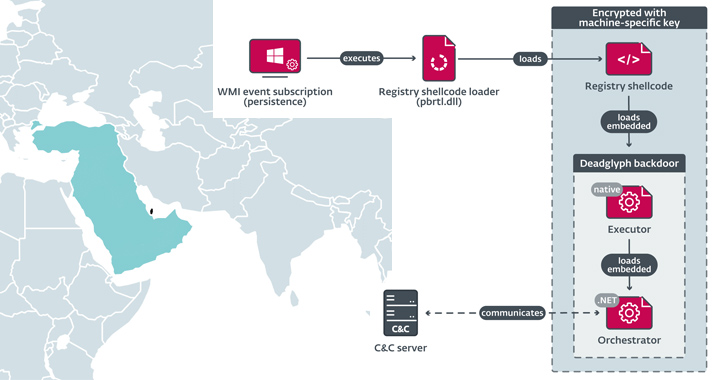
New Advanced Backdoor with Distinctive Malware Tactics
Sep 23, 2023THNCyber Espionage / Malware Cybersecurity researchers have discovered a previously undocumented advanced backdoor dubbed Deadglyph employed by a threat actor known as Stealth Falcon as part of a cyber espionage campaign. "Deadglyph's architecture is unusual as it consists of cooperating components – one a native x64 binary, the other a .NET assembly," ESET said … [Read more...] about New Advanced Backdoor with Distinctive Malware Tactics