Beware: hundreds of thousands of websites are fakes. They’re made to look like the sites of popular online stores, banks, and delivery services, but with just one purpose: to steal your passwords and financial data. Victims are lured to such sites by phishing emails, messenger chats, and even paid ads. But don’t despair: even if you click on a bogus link, it might still be … [Read more...] about How to spot phishing on a hacked WordPress website
spot
Watch Out! Researchers Spot New Microsoft Office Zero-Day Exploit in the Wild
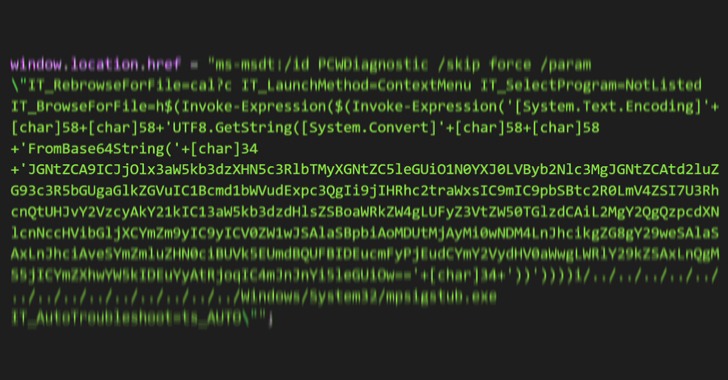
Cybersecurity researchers are calling attention to a zero-day flaw in Microsoft Office that could be abused to achieve arbitrary code execution on affected Windows systems. The vulnerability came to light after an independent cybersecurity research team known as nao_sec uncovered a Word document ("05-2022-0438.doc") that was uploaded to VirusTotal from an IP address in … [Read more...] about Watch Out! Researchers Spot New Microsoft Office Zero-Day Exploit in the Wild
How to Extract Memory Information to Spot Linux Malware
Threat actors go to great lengths to hide the intentions of the malware they produce This blog demonstrates reliable methods for extracting information from popular Linux shells Extracted memory information can help categorize unknown software as malicious or benign and could reveal information to help incident responders Some malware is only ever resident in memory, so memory … [Read more...] about How to Extract Memory Information to Spot Linux Malware