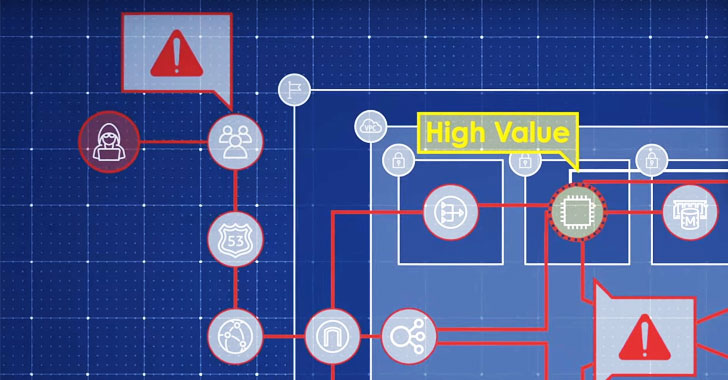
Today there are plenty of cybersecurity tools on the market. It is now more important than ever that the tools you decide to use work well together. If they don't, you will not get the complete picture, and you won't be able to analyze the entire system from a holistic perspective. This means that you won't be able to do the right mitigations to improve your security posture. … [Read more...] about Improve Your Cyber Security Posture by Combining State of the Art Security Tools
State
Data Breach Exposes 1.6 Million Jobless Claims Filed in the Washington State
The Office of the Washington State Auditor (SAO) on Monday said it's investigating a security incident that resulted in the compromise of personal information of more than 1.6 million people who filed for unemployment claims in the state in 2020. The SAO blamed the breach on a software vulnerability in Accellion's File Transfer Appliance (FTA) service, which allows … [Read more...] about Data Breach Exposes 1.6 Million Jobless Claims Filed in the Washington State
The State of Exploit Development: Part 2
In Part 1 of this two-part blog series, we addressed binary exploitation on Windows systems, including some legacy and contemporary mitigations that exploit writers and adversaries must deal with in today’s cyber landscape. In Part 2, we will walk through more of the many mitigations Microsoft has put in place. Modern Mitigation #1: Page Table Randomization As explained in Part … [Read more...] about The State of Exploit Development: Part 2
The State of Exploit Development: Part 1
Memory corruption exploits have historically been one of the strongest accessories in a good red teamer’s toolkit. They present an easy win for offensive security engineers, as well as adversaries, by allowing the attacker to execute payloads without relying on any user interaction. Fortunately for defenders, but unfortunately for researchers and adversaries, these types of … [Read more...] about The State of Exploit Development: Part 1