Dec 14, 2024Ravie LakshmananMalware / Cyber Threat Thai government officials have emerged as the target of a new campaign that leverages a technique called DLL side-loading to deliver a previously undocumented backdoor dubbed Yokai. "The target of the threat actors were Thailand officials based on the nature of the lures," Nikhil Hegde, senior engineer for Netskope's Security … [Read more...] about Thai Officials Targeted in Yokai Backdoor Campaign Using DLL Side-Loading Techniques
techniques
Defending against popular cyberattack techniques in 2024
Recent reports by Kaspersky experts on the statistics of Managed Detection and Response (MDR) and Incident Response (IR) services for 2023 reveal that most observed cyberattacks employ a handful of techniques that are repeated time and again. These techniques are seen both in attacks that are fully executed and cause damage, as well as in incidents that are stopped in their … [Read more...] about Defending against popular cyberattack techniques in 2024
HijackLoader Expands Techniques to Improve Defense Evasion
HijackLoader continues to become increasingly popular among adversaries for deploying additional payloads and tooling A recent HijackLoader variant employs sophisticated techniques to enhance its complexity and defense evasion CrowdStrike detects this new HijackLoader variant using machine learning and behavior-based detection capabilities CrowdStrike researchers have … [Read more...] about HijackLoader Expands Techniques to Improve Defense Evasion
Researchers Unveal GuLoader Malware’s Latest Anti-Analysis Techniques
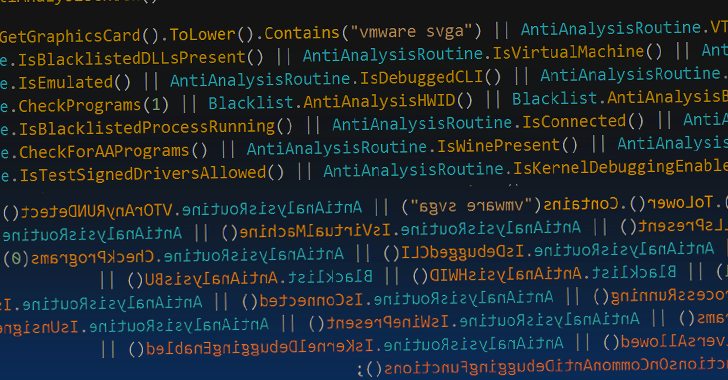
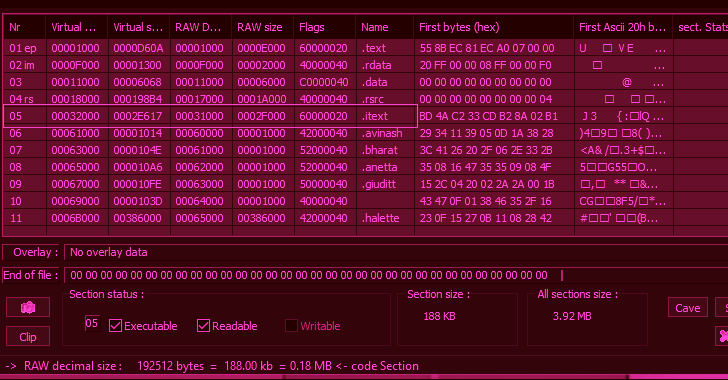
Dec 09, 2023NewsroomMalware / Cyberattack Threat hunters have unmasked the latest tricks adopted by a malware strain called GuLoader in an effort to make analysis more challenging. "While GuLoader's core functionality hasn't changed drastically over the past few years, these constant updates in their obfuscation techniques make analyzing GuLoader a time-consuming and … [Read more...] about Researchers Unveal GuLoader Malware’s Latest Anti-Analysis Techniques
Typhon Reborn Stealer Malware Resurfaces with Advanced Evasion Techniques
Apr 05, 2023Ravie LakshmananCyber Threat / Dark Web The threat actor behind the information-stealing malware known as Typhon Reborn has resurfaced with an updated version (V2) that packs in improved capabilities to evade detection and resist analysis. The new version is offered for sale on the criminal underground for $59 per month, $360 per year, or alternatively, for $540 … [Read more...] about Typhon Reborn Stealer Malware Resurfaces with Advanced Evasion Techniques
DLL Side-Loading: How To Combat Threat Actor Evasion Techniques
Threat actors constantly evolve their tactics and techniques to circumvent security solutions. Working at the cutting-edge of detection engineering, CrowdStrike rapidly tracks and observes these evolutions in tactics to deliver timely, effective detections that protect customers. In this blog, we explore DLL side-loading and learn how CrowdStrike has expanded protections with … [Read more...] about DLL Side-Loading: How To Combat Threat Actor Evasion Techniques
Parallax RAT Targeting Cryptocurrency Firms with Sophisticated Injection Techniques
Mar 01, 2023Ravie LakshmananCryptocurrency / Cyber Attack Cryptocurrency companies are being targeted as part of a new campaign that delivers a remote access trojan called Parallax RAT. The malware "uses injection techniques to hide within legitimate processes, making it difficult to detect," Uptycs said in a new report. "Once it has been successfully injected, attackers can … [Read more...] about Parallax RAT Targeting Cryptocurrency Firms with Sophisticated Injection Techniques
DLL Side-Loading: How to Combat Threat Actor Evasion Techniques
Threat actors constantly evolve their tactics and techniques to circumvent security solutions. Working at the cutting-edge of detection engineering, CrowdStrike rapidly tracks and observes these evolutions in tactics to deliver timely, effective detections that protect customers. In this blog, we explore DLL side-loading and learn how CrowdStrike has expanded protections with … [Read more...] about DLL Side-Loading: How to Combat Threat Actor Evasion Techniques
The Anatomy of Wiper Malware, Part 4: Helper Techniques
This is the fourth blog post in a four-part series. Read Part 1 | Part 2 | Part 3. In Part 3, CrowdStrike’s Endpoint Protection Content Research Team covered the finer points of Input/Output Control (IOCTL) usage by various wipers. The fourth and final part of the wiper series covers some of the rarely used “helper” techniques implemented by wipers, which achieve secondary … [Read more...] about The Anatomy of Wiper Malware, Part 4: Helper Techniques
The Anatomy of Wiper Malware, Part 1: Common Techniques
This blog post is the first in a four-part series in which CrowdStrike’s Endpoint Protection Content Research Team will dive into various wipers discovered by the security community over the past 10 years. Our goal is to review in depth the various techniques employed by wipers that target the Windows operating system. Background A wiper is a type of malware with a single … [Read more...] about The Anatomy of Wiper Malware, Part 1: Common Techniques