This blog was originally published oct. 28, 2021 on humio.com. Humio is a CrowdStrike Company. Definition of MTTR Mean time to repair (MTTR) is a key performance indicator (KPI) that represents the average time required to restore a system to functionality after an incident. MTTR is used along with other incident metrics to assess the performance of DevOps and ITOps, gauge the … [Read more...] about Mean Time to Repair (MTTR) Explained
Time
“Left of Boom” Cybersecurity: Proactive Cybersecurity in a Time of Increasing Threats and Attacks
“Left of Boom” The allied military forces engaged in operations in Iraq and Afghanistan nearly 20 years ago were confronted with the challenge of Improvised Explosive Devices (IEDs), which were roadside bombs that detonated remotely and inflicted casualties and damage to military personnel and materiel. Major research efforts on how to detect these IEDs and detonate them … [Read more...] about “Left of Boom” Cybersecurity: Proactive Cybersecurity in a Time of Increasing Threats and Attacks
Save time with Dynamic Attributes for Cisco Secure Firewall
With cloud comes complexity As organizations accelerate their transition to hybrid cloud, multicloud, and other dynamic environments, static security controls are no longer adequate. The shift of applications and the associated security controls within dynamic cloud environments create challenges for firewall teams to keep up with security requirements. Workloads spin up and … [Read more...] about Save time with Dynamic Attributes for Cisco Secure Firewall
Time to Refresh: Leapfrogging Security with Cisco SecureX
What is the first thing that comes to your mind when you hear the words “tech refresh?” For example, do you think about an antiquated technology that is not integrated needing a fresh lease of life? Or is it just getting new technology to solve a problem that the predecessor failed at solving? Or is it part of a much larger attempt to transform security to become an enabler … [Read more...] about Time to Refresh: Leapfrogging Security with Cisco SecureX
#CiscoChat Live: Recapture Your Time and Get More Out of Secure Remote Working
How do you feel when you hear phrases like, “the pandemic”, “remote working”, “the new (or next) normal”? Fatigued? You are not alone. Most of us are experiencing online fatigue as a result of working from home for months now. Worse, we’re physically and mentally fatigued by the shift to the “always on” mode with remote working. It doesn’t take much if you think about it. Just … [Read more...] about #CiscoChat Live: Recapture Your Time and Get More Out of Secure Remote Working
Are you ready to place a call for simplified cybersecurity? It’s time to stop switchboarding.
My grandfather was born in the 1930s. In the early 2000s, he used to recollect childhood memories of his experience with the telephone while growing up in India. Since the 1990s, advances in this industry have made communication a piece of cake. He would often tell us stories about day trips for the sole purpose of making a phone call, the community experience of the party … [Read more...] about Are you ready to place a call for simplified cybersecurity? It’s time to stop switchboarding.
Several High-Profile Accounts Hacked in the Biggest Twitter Hack of All Time
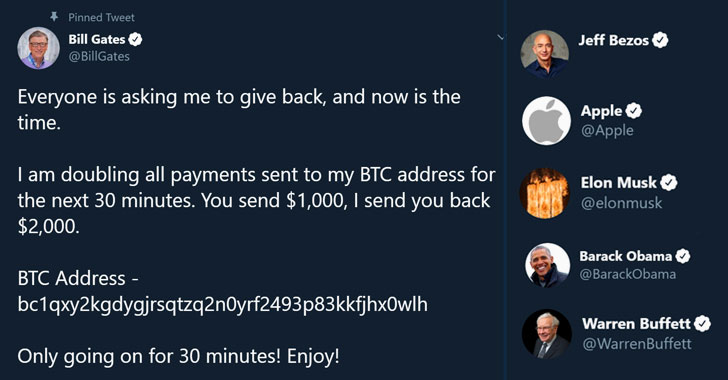
Social media platform Twitter, earlier today on Wednesday, was on fire after it suffered one of the biggest cyberattacks in its history.A number of high-profile Twitter accounts, including those of US presidential candidate Joe Biden, Amazon CEO Jeff Bezos, Bill Gates, Elon Musk, Uber, and Apple, were breached simultaneously in what's a far-reaching hacking campaign carried out … [Read more...] about Several High-Profile Accounts Hacked in the Biggest Twitter Hack of All Time
CrowdStrike’s Real Time Response Enables System Recovery
Introduction Cyberattacks including ransomware have increased as work environments have changed, and organizations have shifted to supporting more remote personnel. With threats increasing against these remote systems, the ability to block attacks and respond rapidly in the event of a compromise is even more challenging. Do security teams have the visibility and context they … [Read more...] about CrowdStrike’s Real Time Response Enables System Recovery
CrowdStrike’s Real Time Response Expands Protections
Introduction Sinkholes can be used by both bad actors and system administrators alike. Bad actors can redirect systems to malicious domains and security admins can stop systems from reaching those domains. If remote employees are not using the corporate VPN, do security teams have the ability to manipulate system redirects and sinkhole malicious … [Read more...] about CrowdStrike’s Real Time Response Expands Protections
CrowdStrike’s Real Time Response Enables Remote Remediation
Introduction Remote systems can be easy targets for attackers. When these systems are compromised, responders need to work quickly to understand the attack and take action to remediate. The responders need remote system visibility and access since users can’t walk a laptop over to IT. Do responders have the visibility and context they need to understand the threat? Can they … [Read more...] about CrowdStrike’s Real Time Response Enables Remote Remediation