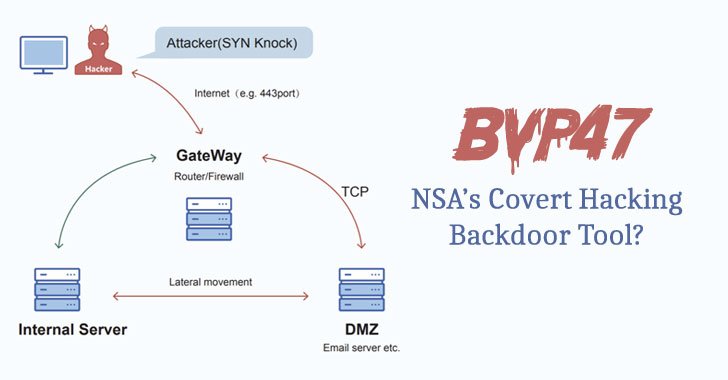
Researchers from China's Pangu Lab have disclosed details of a "top-tier" backdoor put to use by the Equation Group, an advanced persistent threat (APT) with alleged ties to the cyber-warfare intelligence-gathering unit of the U.S. National Security Agency (NSA). Dubbed "Bvp47" owing to numerous references to the string "Bvp" and the numerical value "0x47" used in the … [Read more...] about Chinese Experts Uncover Details of Equation Group’s Bvp47 Covert Hacking Tool
tool
Experts Detail Logging Tool of DanderSpritz Framework Used by Equation Group Hackers
Cybersecurity researchers have offered a detailed glimpse into a system called DoubleFeature that's dedicated to logging the different stages of post-exploitation stemming from the deployment of DanderSpritz, a full-featured malware framework used by the Equation Group. DanderSpritz came to light on April 14, 2017, when a hacking group known as the Shadow Brokers leaked the … [Read more...] about Experts Detail Logging Tool of DanderSpritz Framework Used by Equation Group Hackers
CrowdStrike Launches Free Targeted Log4j Search Tool
The recently discovered Log4j vulnerability has serious potential to expose organizations across the globe to a new wave of cybersecurity risks as threat actors look to exploit this latest vulnerability to execute their malicious payloads using remote code execution (RCE). An immediate challenge that every organization faces is simply trying to understand exactly where you have … [Read more...] about CrowdStrike Launches Free Targeted Log4j Search Tool
Here’s a New Free Tool to Discover Unprotected Cloud Storage Instances
The IDC cloud security survey 2021 states that as many as 98% of companies were victims of a cloud data breach within the past 18 months. Fostered by the pandemic, small and large organizations from all over the world are migrating their data and infrastructure into a public cloud, while often underestimating novel and cloud-specific security or privacy issues. Nearly every … [Read more...] about Here’s a New Free Tool to Discover Unprotected Cloud Storage Instances
New ‘unc0ver’ Tool Can Jailbreak All iPhone Models Running iOS 11.0
A popular jailbreaking tool called "unc0ver" has been updated to support iOS 14.3 and earlier releases, thereby making it possible to unlock almost every single iPhone model using a vulnerability that Apple in January disclosed was actively exploited in the wild. The latest release, dubbed unc0ver v6.0.0, was released on Sunday, according to its lead developer Pwn20wnd, … [Read more...] about New ‘unc0ver’ Tool Can Jailbreak All iPhone Models Running iOS 11.0
Chinese Hackers Had Access to a U.S. Hacking Tool Years Before It Was Leaked Online
On August 13, 2016, a hacking unit calling itself "The Shadow Brokers" announced that it had stolen malware tools and exploits used by the Equation Group, a sophisticated threat actor believed to be affiliated to the Tailored Access Operations (TAO) unit of the U.S. National Security Agency (NSA). Although the group has since signed off following the unprecedented disclosures, … [Read more...] about Chinese Hackers Had Access to a U.S. Hacking Tool Years Before It Was Leaked Online
Getting more value from your endpoint security tool #5: Querying Tips for Vulnerability & Compliance
Thank you for tuning in to the fifth and final installment of this blog series. As I stated in my previous blog posts on orbital advanced search, my father was an automobile mechanic. More specifically, he was a “brakes and front-end mechanic”. On several occasions, Pops would point out the wear on a set of tires and would tell me that either the car was out of alignment, … [Read more...] about Getting more value from your endpoint security tool #5: Querying Tips for Vulnerability & Compliance
Getting more value from your endpoint security tool #4: Querying Tips for IT Operations
As the son of a retired automotive mechanic, the lessons my father taught me are still just as important today. As I mentioned in my previous post about Orbital Advanced Search, “Pops” was always teaching me something. This time it was to always clean the tools after every job, maintain the tools that need oil, etc., and to always keep your tools organized neatly in the … [Read more...] about Getting more value from your endpoint security tool #4: Querying Tips for IT Operations
Getting more value from your endpoint security tool #3: Querying Tips for Incident Investigation
Have you ever looked around the house for a specific tool to complete a task? And, after looking high and low, even scouring through that bottomless “junk drawer,” you were unsuccessful locating it. Then, you decide to just use what you have readily available. You know, using that flathead screwdriver as a chisel or a prybar, which inevitably breaks because you did not use the … [Read more...] about Getting more value from your endpoint security tool #3: Querying Tips for Incident Investigation
New 4CAN tool helps identify vulnerabilities in on-board car computers
Threat Research Modern automobiles contain hundreds of sensors and mechanics that communicate via computers to understand their surrounding environment. Those components provide real-time information to drivers, connect the vehicle to a global network, and in some cases use that telemetry to automatically drive the vehicle. Like any computer, … [Read more...] about New 4CAN tool helps identify vulnerabilities in on-board car computers