The threat landscape is full of moving targets. Over time, popular tools, tactics, and procedures change. Malicious techniques fall out of fashion, only to come roaring back months, if not years, later. All the while, security practitioners monitor network traffic and adapt their defenses to protect their users and networks. Keeping on top of these trends is one of the most … [Read more...] about How to Monitor Network Traffic: Findings from the Cisco Cyber Threat Trends Report
Traffic
Secure your Elastic Cloud deployment with AWS PrivateLink traffic filter
Traffic filters consist of rule(s) that specify the source of traffic, such as IP/CIDR or AWS VPC endpoint, and rule sets, which are a set of traffic filter rules. Rule sets are then associated with the deployment and can restrict access to the deployment based on those rules.By default, customers connect to deployment over the public internet. Customers can assign multiple … [Read more...] about Secure your Elastic Cloud deployment with AWS PrivateLink traffic filter
How to Prevent ChatGPT From Stealing Your Content & Traffic
ChatGPT and similar large language models (LLMs) have added further complexity to the ever-growing online threat landscape. Cybercriminals no longer need advanced coding skills to execute fraud and other damaging attacks against online businesses and customers, thanks to bots-as-a-service, residential proxies, CAPTCHA farms, and other easily accessible tools. Now, the latest … [Read more...] about How to Prevent ChatGPT From Stealing Your Content & Traffic
New ‘Letscall’ Malware Employs Voice Traffic Routing
Jul 07, 2023Swati KhandelwalMobile Security / Malware Researchers have issued a warning about an emerging and advanced form of voice phishing (vishing) known as "Letscall." This technique is currently targeting individuals in South Korea. The criminals behind "Letscall" employ a multi-step attack to deceive victims into downloading malicious apps from a counterfeit Google … [Read more...] about New ‘Letscall’ Malware Employs Voice Traffic Routing
MOVEit mayhem 3: “Disable HTTP and HTTPS traffic immediately”
Yet more MOVEit mayhem! “Disable HTTP and HTTPS traffic to MOVEit Transfer,” says Progress Software, and the timeframe for doing so is “immediately”, no ifs, no buts. Progress Software is the maker of file-sharing software MOVEit Transfer, and the hosted MOVEit Cloud alternative that’s based on it, and this is its third warning in three weeks about hackable vulnerabilities in … [Read more...] about MOVEit mayhem 3: “Disable HTTP and HTTPS traffic immediately”
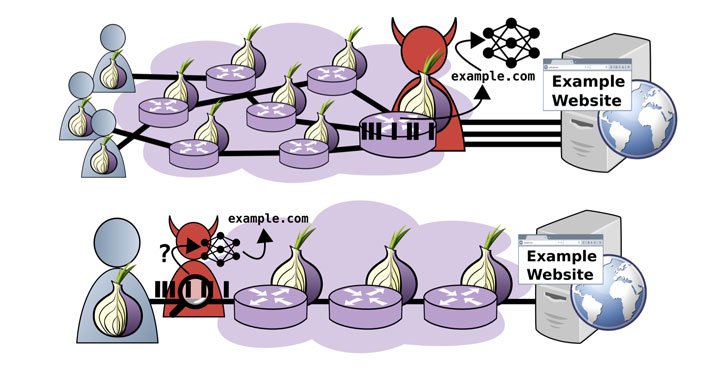
Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
A new analysis of website fingerprinting (WF) attacks aimed at the Tor web browser has revealed that it's possible for an adversary to glean a website frequented by a victim, but only in scenarios where the threat actor is interested in a specific subset of the websites visited by users. "While attacks can exceed 95% accuracy when monitoring a small set of five popular … [Read more...] about Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
3 reasons why Cisco Stealthwatch is the Michael Jordan of Network Traffic Analysis tools
The Last Dance, a 10-part docuseries about the historic career of NBA legend, Michael Jordan, came to an end recently. I was glued to my TV watching, and re-watching, these captivating hour-long episodes. It was chock full of uncut, never before seen footage that had sports fans around the world hooked. As a millennial who did not get the privilege of living through the … [Read more...] about 3 reasons why Cisco Stealthwatch is the Michael Jordan of Network Traffic Analysis tools
Threats in encrypted traffic – Cisco Blog
There was a time when the web was open. Quite literally—communications taking place on the early web were not masked in any significant fashion. This meant that it was fairly trivial for a bad actor to intercept and read the data being transmitted between networked devices. This was especially troublesome when it came to sensitive data, such as password authentication or credit … [Read more...] about Threats in encrypted traffic – Cisco Blog
Kazakhstan Begins Intercepting HTTPS Internet Traffic Of All Citizens Forcefully
If you are in Kazakhstan and unable to access the Internet service without installing a certificate, you're not alone.The Kazakhstan government has once again issued an advisory to all major local Internet Service Providers (ISPs) asking them to make it mandatory for all their customers to install government-issued root certificates on their devices in order to regain access to … [Read more...] about Kazakhstan Begins Intercepting HTTPS Internet Traffic Of All Citizens Forcefully