In September 2024, a team of researchers from both the University of Florida and Texas Tech University presented a paper detailing a rather sophisticated method for intercepting text entered by users of the Apple Vision Pro mixed reality (MR) headset. The researchers dubbed this method GAZEploit. In this post, we’ll explore how the attack works, the extent of the threat to … [Read more...] about How to snoop on what an Apple Vision Pro user is typing
user
Protect Against Adversary-in-the-Middle with Cisco’s User Protection Suite
In the blog, Understanding & Defending Against Adversary-in-the-Middle (AiTM) Attacks, we reviewed the basics of an AiTM attack and how Duo can protect against it. To recap, in an AiTM attack, the attacker sits in between the user and the real web page and steals a user’s valid session cookies. This means that they can bypass traditional authentication controls. Talos, … [Read more...] about Protect Against Adversary-in-the-Middle with Cisco’s User Protection Suite
User Protection Suite Secures Against Talos Top Ransomware Attack Trends
In Cisco Talos’ first episode of Talos Threat Perspective (TTP) episode, two Talos Threat Intelligence experts, Nick Biasini and James Nutland, discuss new research on the most prominent ransomware groups. They also pick three key topics and trends to focus on: initial access, differences among the groups, and the vulnerabilities they most heavily target. In their research, … [Read more...] about User Protection Suite Secures Against Talos Top Ransomware Attack Trends
Stopping Supply Chain Attacks with Cisco’s User Protection Suite
The Dinner Party Supply Chain Attack A supply chain attack occurs when a bad actor gains access to an organization’s people and data by compromising a vendor or business partner. Let’s think of this type of attack as if it was a dinner party. You invite your close friends over and hire a catering company that you know and trust to cook the meal. However, neither you nor the … [Read more...] about Stopping Supply Chain Attacks with Cisco’s User Protection Suite
Examining the Growing Threat and User Perspectives
Jul 25, 2023The Hacker NewsEndpoint Security / macOS As the number of people using macOS keeps going up, so does the desire of hackers to take advantage of flaws in Apple's operating system. What Are the Rising Threats to macOS? There is a common misconception among macOS fans that Apple devices are immune to hacking and malware infection. However, users have been facing … [Read more...] about Examining the Growing Threat and User Perspectives
A User Guide for OpenSearch Dashboards
Over the last decade, log management has been largely dominated by the ELK Stack – a once-open source tool set that collects, processes, stores and analyzes log data. The ‘k’ in the ELK Stack represents Kibana, which is the component engineers use to query and visualize their log data stored in Elasticsearch. Sadly, in January 2021, Elastic decided to close source the ELK … [Read more...] about A User Guide for OpenSearch Dashboards
User Sign-Ups and Package Uploads Temporarily Halted
May 21, 2023Ravie LakshmananSoftware Security / Malware The maintainers of Python Package Index (PyPI), the official third-party software repository for the Python programming language, have temporarily disabled the ability for users to sign up and upload new packages until further notice. "The volume of malicious users and malicious projects being created on the index in the … [Read more...] about User Sign-Ups and Package Uploads Temporarily Halted
Twitter Denies Hacking Claims, Assures Leaked User Data Not from its System
Jan 12, 2023Ravie LakshmananData Security / Privacy Twitter on Wednesday said that its investigation found "no evidence" that users' data sold online was obtained by exploiting any security vulnerabilities in its systems. "Based on information and intel analyzed to investigate the issue, there is no evidence that the data being sold online was obtained by exploiting a … [Read more...] about Twitter Denies Hacking Claims, Assures Leaked User Data Not from its System
France Fines Microsoft €60 Million for Using Advertising Cookies Without User Consent
Dec 23, 2022Ravie LakshmananPrivacy / Data Security France's privacy watchdog has imposed a €60 million ($63.88 million) fine against Microsoft's Ireland subsidiary for dropping advertising cookies in users' computers without their explicit consent in violation of data protection laws in the European Union. The Commission nationale de l'informatique et des libertés (CNIL) … [Read more...] about France Fines Microsoft €60 Million for Using Advertising Cookies Without User Consent
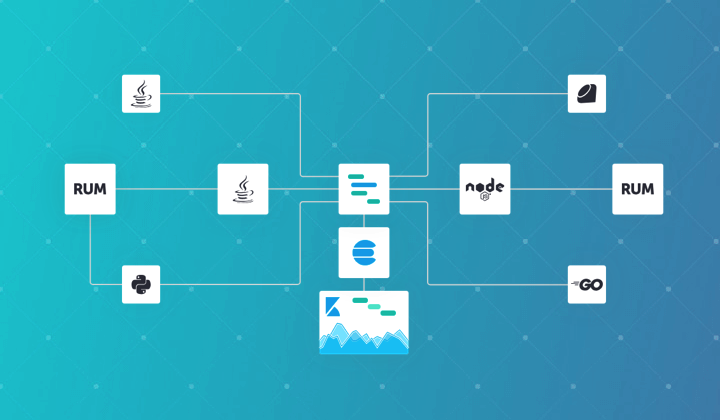
Performing Real User Monitoring (RUM) with Elastic APM
Sorry if I lured you into the mood of having a sip of a wonderful cocktail made with rum and you realized that the RUM I’m talking about is not the rum you are craving. But, be assured that Elastic RUM is equally wonderful! Let’s take a sip! I do want to warn you that it will take a bit of time to go through the amount of detail I will cover in this blog.What is RUM?Elastic … [Read more...] about Performing Real User Monitoring (RUM) with Elastic APM