Jan 11, 2024NewsroomVulnerability / Cyber Attack Cybersecurity researchers have developed a proof-of-concept (PoC) code that exploits a recently disclosed critical flaw in the Apache OfBiz open-source Enterprise Resource Planning (ERP) system to execute a memory-resident payload. The vulnerability in question is CVE-2023-51467 (CVSS score: 9.8), a bypass for another severe … [Read more...] about New PoC Exploit for Apache OfBiz Vulnerability Poses Risk to ERP Systems
vulnerability
How to hack Android, macOS, iOS, and Linux through a Bluetooth vulnerability
A severe vulnerability has been found in the implementations of the Bluetooth protocol across several popular operating systems: Android, macOS, iOS, iPadOS, and Linux. This bug potentially allows remote hacking of vulnerable devices without any particular actions required on the part the user. Let’s dive into the details. The Bluetooth vulnerability allows you to connect a … [Read more...] about How to hack Android, macOS, iOS, and Linux through a Bluetooth vulnerability
New Spectre-based Vulnerability Impacts Intel, AMD, and Arm CPUs
Dec 09, 2023NewsroomCyber Threat / Hardware Security Researchers from the Vrije Universiteit Amsterdam have disclosed a new side-channel attack called SLAM that could be exploited to leak sensitive information from kernel memory on current and upcoming CPUs from Intel, AMD, and Arm. The attack is an end-to-end exploit for Spectre based on a new feature in Intel CPUs called … [Read more...] about New Spectre-based Vulnerability Impacts Intel, AMD, and Arm CPUs
Vulnerability in crypto wallets created online in the early 2010s
Researchers have discovered several vulnerabilities in the BitcoinJS library that could leave Bitcoin wallets created online a decade ago prone to hacking. The basic issue is that the private keys for these crypto wallets were generated with far greater predictability than the library developers expected. Randstorm vulnerabilities and consequences Let’s start at the beginning. … [Read more...] about Vulnerability in crypto wallets created online in the early 2010s
The Impact of Microsoft’s Vulnerability Problem
Twenty years ago, Microsoft introduced the concept of Patch Tuesday to “reduce the burden on IT administrators by adding a level of increased predictability and manageability.” The goal of Patch Tuesday was to provide needed structure around what was largely an ad hoc process. By consolidating the majority of security updates and required patches into a planned release cycle, … [Read more...] about The Impact of Microsoft’s Vulnerability Problem
Vulnerability in Confluence Data Center and Confluence Server
Recently, CISA, the FBI, and MS-ISAC issued a joint advisory urging all organizations that use Confluence Data Center and Confluence Server to update the software immediately due to a major vulnerability. Here’s what the problem is and why this advisory is on point. CVE-2023-22515 in Confluence Data Center and Confluence Server The vulnerability in question, designated … [Read more...] about Vulnerability in Confluence Data Center and Confluence Server
Critical GitHub Vulnerability Exposes 4,000+ Repositories to Repojacking Attack
Sep 12, 2023THNSoftware Security / Vulnerability A new vulnerability disclosed in GitHub could have exposed thousands of repositories at risk of repojacking attacks, new findings show. The flaw "could allow an attacker to exploit a race condition within GitHub's repository creation and username renaming operations," Checkmarx security researcher Elad Rapoport said in a … [Read more...] about Critical GitHub Vulnerability Exposes 4,000+ Repositories to Repojacking Attack
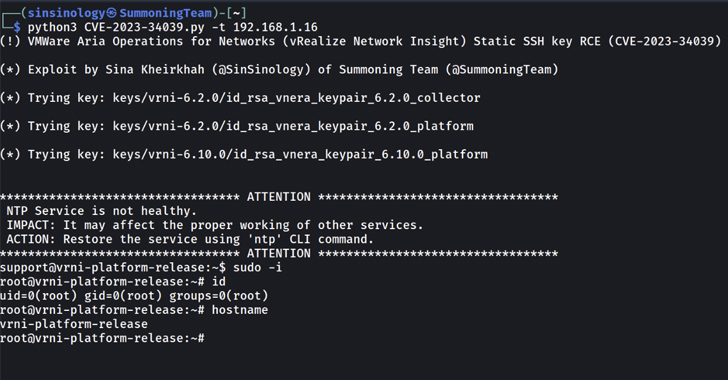
PoC Exploit Released for Critical VMware Aria’s SSH Auth Bypass Vulnerability
Sep 03, 2023THNNetwork Security / Vulnerability Proof-of-concept (PoC) exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks (formerly vRealize Network Insight). The flaw, tracked as CVE-2023-34039, is rated 9.8 out of a maximum of 10 for severity and has been described as a case of authentication … [Read more...] about PoC Exploit Released for Critical VMware Aria’s SSH Auth Bypass Vulnerability
New OpenSSH Vulnerability Exposes Linux Systems to Remote Command Injection
Jul 24, 2023THNLinux / Network Security Details have emerged about a now-patched flaw in OpenSSH that could be potentially exploited to run arbitrary commands remotely on compromised hosts under specific conditions. "This vulnerability allows a remote attacker to potentially execute arbitrary commands on vulnerable OpenSSH's forwarded ssh-agent," Saeed Abbasi, manager of … [Read more...] about New OpenSSH Vulnerability Exposes Linux Systems to Remote Command Injection
nOAuth Microsoft Azure AD Vulnerability
On June 20, 2023, Descope published research detailing how a combination of a flaw in Azure Active Directory and poorly integrated third-party applications — dubbed “nOAuth” — could lead to full account takeover. nOAuth is the latest in a large number of vulnerabilities and architectural weaknesses in Microsoft software and systems like Active Directory that can be exploited … [Read more...] about nOAuth Microsoft Azure AD Vulnerability