Security researchers have discovered a rare piece of Linux spyware that's currently fully undetected across all major antivirus security software products, and includes rarely seen functionalities with regards to most Linux malware, The Hacker News learned.It's a known fact that there are a very few strains of Linux malware exist in the wild as compared to Windows viruses … [Read more...] about A New Backdoor Implant Spies On Linux Desktop Users
web applications
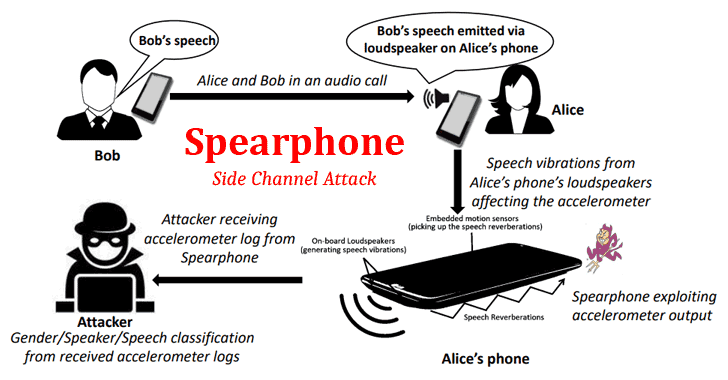
New Attack Lets Android Apps Capture Loudspeaker Data Without Any Permission
Earlier this month, The Hacker News covered a story on research revealing how over 1300 Android apps are collecting sensitive data even when users have explicitly denied the required permissions.The research was primarily focused on how app developers abuse multiple ways around to collect location data, phone identifiers, and MAC addresses of their users by exploiting both … [Read more...] about New Attack Lets Android Apps Capture Loudspeaker Data Without Any Permission
Engage Your Management with the Definitive ‘Security for Management’ Presentation Template
In every organization, there is a person who's directly accountable for cybersecurity. The name of the role varies per the organization's size and maturity – CISO, CIO, and Director of IT are just a few common examples – but the responsibility is similar in all places.They're the person who understands the risk and exposure, knows how prepared the team and most important – what … [Read more...] about Engage Your Management with the Definitive ‘Security for Management’ Presentation Template
Zoom RCE Flaw Also Affects Its Rebranded Versions RingCentral and Zhumu
The same security vulnerabilities that were recently reported in Zoom for macOS also affect two other popular video conferencing software that under the hood, are just a rebranded version of Zoom video conferencing software.Security researchers confirmed The Hacker News that RingCentral, used by over 350,000 businesses, and Zhumu, a Chinese version of Zoom, also runs a hidden … [Read more...] about Zoom RCE Flaw Also Affects Its Rebranded Versions RingCentral and Zhumu
This Flaw Could Have Allowed Hackers to Hack Any Instagram Account Within 10 Minutes
Watch out! Facebook-owned photo-sharing service has recently patched a critical vulnerability that could have allowed hackers to compromise any Instagram account without requiring any interaction from the targeted users.Instagram is growing quickly—and with the most popular social media network in the world after Facebook, the photo-sharing network absolutely dominates when it … [Read more...] about This Flaw Could Have Allowed Hackers to Hack Any Instagram Account Within 10 Minutes
Zoom Video Conferencing for macOS Also Vulnerable to Critical RCE Flaw
The chaos and panic that the disclosure of privacy vulnerability in the highly popular and widely-used Zoom video conferencing software created earlier this week is not over yet.As suspected, it turns out that the core issue—a locally installed web server by the software—was not just allowing any website to turn on your device webcam, but also could allow hackers to take … [Read more...] about Zoom Video Conferencing for macOS Also Vulnerable to Critical RCE Flaw
Facebook to Pay $5 Billion Fine to Settle FTC Privacy Investigation
After months of negotiations, the United States Federal Trade Commission (FTC) has approved a record $5 billion settlement with Facebook over its privacy investigation into the Cambridge Analytica scandal.The settlement will put an end to a wide-ranging probe that began more than a year ago and centers around the violation of a 2011 agreement Facebook made with the FTC that … [Read more...] about Facebook to Pay $5 Billion Fine to Settle FTC Privacy Investigation
Cybersecurity Frameworks — Types, Strategies, Implementation and Benefits
Organizations around the world are wondering how to become immune from cyber attacks which are evolving every day with more sophisticated attack vectors.IT teams are always on the lookout for new ransomware and exploit spreading in the wild, but can all these unforeseen cyber attacks be prevented proactively?That's definitely a 'NO,' which is why there's a reactive approach in … [Read more...] about Cybersecurity Frameworks — Types, Strategies, Implementation and Benefits
Magecart Hackers Infect 17,000 Sites Through Misconfigured Amazon S3 Buckets
Magecart strikes again!Cybersecurity researchers have identified yet another supply-chain attack carried out by payment card hackers against more than 17,000 web domains, which also include websites in the top 2,000 of Alexa rankings.Since Magecart is neither a single group nor a specific malware instead an umbrella term given to all those cyber criminal groups and individuals … [Read more...] about Magecart Hackers Infect 17,000 Sites Through Misconfigured Amazon S3 Buckets
Hackers’ Operating System Kali Linux Released for Raspberry Pi 4
We've got some really exciting news for you...Offensive Security has released an official version of Kali Linux for Raspberry Pi 4—the most powerful version of the compact computer board yet that was released just two weeks ago with the full 4GB of RAM at low cost and easy accessibility.Based on Debian, Kali Linux has always been the number one operating system for ethical … [Read more...] about Hackers’ Operating System Kali Linux Released for Raspberry Pi 4