A security researcher known as mr.d0x has published a post detailing a new technique that can be used for phishing and potentially other malicious activities. The technique exploits so-called progressive web apps (PWAs). In this post, we discuss what these applications are, why they can be dangerous, how attackers can use them for their own purposes, and how to [placeholder … [Read more...] about How phishing using progressive web apps (PWAs) works
works
How a man-on-the-side attack works
There are attacks that everyone’s heard of, like distributed denial-of-service (DDoS) attacks; there are those that mostly only professionals know about, such as man-in-the-middle (MitM) attacks; and then there are the rarer, more exotic ones, like man-on-the-side (MotS) attacks. In this post, we talk about the latter in more detail, and discuss how they differ from … [Read more...] about How a man-on-the-side attack works
How a Spook.js attack works
By comparison, a phishing attack makes sense: Click a link, land on a malicious page, enter some details, and an attacker steals them. Try this one on for size, instead: Click a link and an attacker steals your data. That’s right, today we’re talking about malicious pages that exploit a fundamental CPU feature to steal data without requiring a victim to enter anything. And the … [Read more...] about How a Spook.js attack works
AppTrana — Website Security Solution That Actually Works
Data loss and theft continues to rise, and hardly a day goes by without significant data breaches hit the headlines.In January 2019 alone, 1.76 billion records were leaked, and according to IBM's Data Breach study, the average cost of each lost or stolen record has reached about $148.Most of these data leaks are because of malicious attacks, where exploitation of web … [Read more...] about AppTrana — Website Security Solution That Actually Works
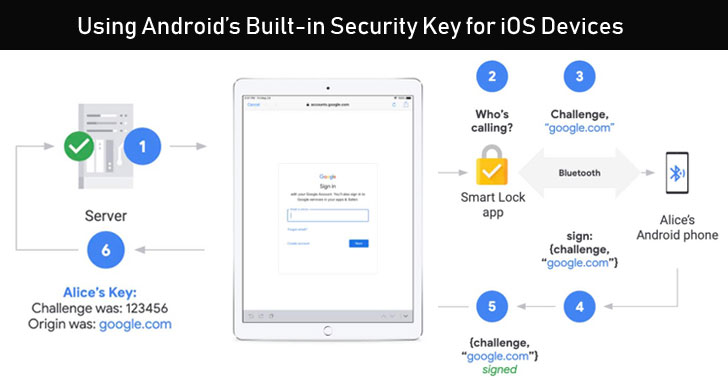
Android’s Built-in Security Key Now Works With iOS Devices For Secure Login
In April this year, a software update from Google overnight turned all Android phones, running Android 7.0 Nougat and up, into a FIDO-certified hardware security key as part of a push to encourage two-step verification.The feature made it possible for users to confirm their identity when logging into a Google account more effortless and secure, without separately managing and … [Read more...] about Android’s Built-in Security Key Now Works With iOS Devices For Secure Login