Jun 01, 2024NewsroomAI-as-a-Service / Data Breach Artificial Intelligence (AI) company Hugging Face on Friday disclosed that it detected unauthorized access to its Spaces platform earlier this week. "We have suspicions that a subset of Spaces' secrets could have been accessed without authorization," it said in an advisory. Spaces offers a way for users to create, host, and … [Read more...] about AI Company Hugging Face Detects Unauthorized Access to Its Spaces Platform
access
Accelerating SaaS security certifications to maximize market access
The regulatory landscape for Software-as-a-Service (SaaS) offerings is rapidly changing worldwide as governments seek to address concerns around privacy, security, and data sovereignty. While the European Union’s Cybersecurity Certification Scheme for Cloud Services (EUCS) has set a high standard for data protection, Asian countries are also stepping up their regulatory … [Read more...] about Accelerating SaaS security certifications to maximize market access
Using Elastic as a global data mesh: Unify data access with security, governance, and policy
Data mesh vs. data fabricWe should probably start with what it’s not. A “data mesh” is not the same as a “data fabric.” A data fabric allows data flowing in from across the enterprise (from the edge, the network, the applications, the appliances . . . literally everywhere) to be confidently received and persisted, making it available for delivery to any consumers who might want … [Read more...] about Using Elastic as a global data mesh: Unify data access with security, governance, and policy
Aembit Strengthens Security for Workload-to-Workload Access
The rise of distributed cloud services and the omnipresence of APIs has caused cloud-native application architecture to become highly fragmented. Enforcing secure access is a critical step in strengthening security as IT environments become more complex — but for many organizations, ensuring secure access across this evolving architecture is a constant challenge. Existing … [Read more...] about Aembit Strengthens Security for Workload-to-Workload Access
Malware Using Google MultiLogin Exploit to Maintain Access Despite Password Reset
Jan 03, 2024NewsroomMalware / Data Theft Information stealing malware are actively taking advantage of an undocumented Google OAuth endpoint named MultiLogin to hijack user sessions and allow continuous access to Google services even after a password reset. According to CloudSEK, the critical exploit facilitates session persistence and cookie generation, enabling threat … [Read more...] about Malware Using Google MultiLogin Exploit to Maintain Access Despite Password Reset
Non-Human Access is the Path of Least Resistance: A 2023 Recap
Dec 12, 2023The Hacker NewsCybersecurity / GenAI Security 2023 has seen its fair share of cyber attacks, however there's one attack vector that proves to be more prominent than others - non-human access. With 11 high-profile attacks in 13 months and an ever-growing ungoverned attack surface, non-human identities are the new perimeter, and 2023 is only the beginning. Why … [Read more...] about Non-Human Access is the Path of Least Resistance: A 2023 Recap
5 Holiday Tips to Secure Your Organization from Access Brokers
The holiday season brings a shift in how people and businesses operate: Some companies may partially shut down, leaving only a skeleton crew to manage their IT environments, while others head into their busiest time of year. This seasonal change in staffing and business operations, combined with the general holiday distraction, often creates risk and makes organizations more … [Read more...] about 5 Holiday Tips to Secure Your Organization from Access Brokers
New OS Tool Tells You Who Has Access to What Data
Ensuring sensitive data remains confidential, protected from unauthorized access, and compliant with data privacy regulations is paramount. Data breaches result in financial and reputational damage but also lead to legal consequences. Therefore, robust data access security measures are essential to safeguard an organization's assets, maintain customer trust, and meet regulatory … [Read more...] about New OS Tool Tells You Who Has Access to What Data
5 Reasons Why Access Management is the Key to Securing the Modern Workplace
The way we work has undergone a dramatic transformation in recent years. We now operate within digital ecosystems, where remote work and the reliance on a multitude of digital tools is the norm rather than the exception. This shift – as you likely know from your own life – has led to superhuman levels of productivity that we wouldn't ever want to give up. But moving fast comes … [Read more...] about 5 Reasons Why Access Management is the Key to Securing the Modern Workplace
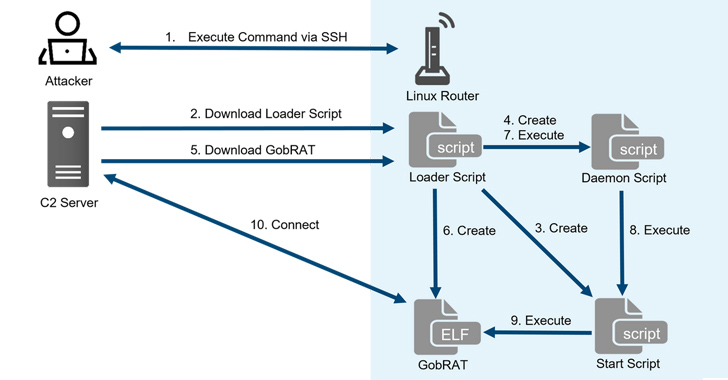
New GobRAT Remote Access Trojan Targeting Linux Routers in Japan
May 29, 2023Ravie LakshmananLinux / Network Security Linux routers in Japan are the target of a new Golang remote access trojan (RAT) called GobRAT. "Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT," the JPCERT Coordination Center (JPCERT/CC) said in a report … [Read more...] about New GobRAT Remote Access Trojan Targeting Linux Routers in Japan