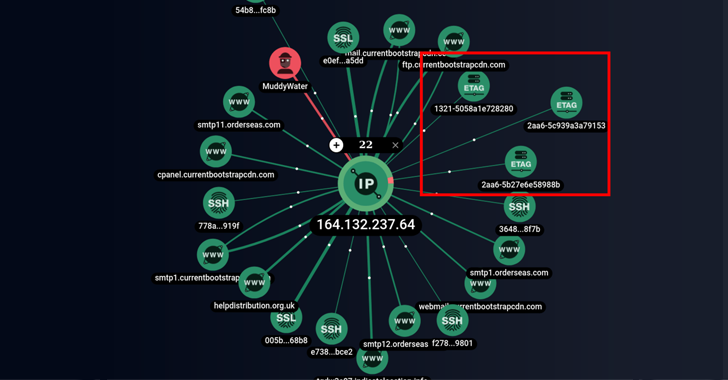
Apr 18, 2023Ravie LakshmananCyber Threat / Malware The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote administration tools to commandeer targeted systems. While the nation-state group has previously employed ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has revealed the adversary's … [Read more...] about Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access
access
Smart & Frictionless Zero Trust Access
Providing secure access and a frictionless user experience are typically competing initiatives, but they don’t have to be! Read on to learn why. In our world today, context changes quickly. We work from home, coffee shops and the office. We use multiple devices to do work. And on the flip side, attackers are becoming increasingly savvy, getting around security controls, such … [Read more...] about Smart & Frictionless Zero Trust Access
New TikTok Privacy Policy Confirms Chinese Staff Can Access European Users’ Data
Popular short-form video-sharing service TikTok is revising its privacy policy for European users to make it explicitly clear that user data can be accessed by some employees from across the world, including China. The ByteDance-owned platform, which currently stores European user data in the U.S. and Singapore, said the revision is part of its ongoing data governance efforts … [Read more...] about New TikTok Privacy Policy Confirms Chinese Staff Can Access European Users’ Data
Researchers Detail Azure SFX Flaw That Could’ve Allowed Attackers to Gain Admin Access
Cybersecurity researchers have shared more details about a now-patched security flaw in Azure Service Fabric Explorer (SFX) that could potentially enable an attacker to gain administrator privileges on the cluster. The vulnerability, tracked as CVE-2022-35829, carries a CVSS severity rating of 6.2 and was addressed by Microsoft as part of its Patch Tuesday updates last … [Read more...] about Researchers Detail Azure SFX Flaw That Could’ve Allowed Attackers to Gain Admin Access
Hackers Had Access to LastPass’s Development Systems for Four Days
Password management solution LastPass shared more details pertaining to the security incident last month, disclosing that the threat actor had access to its systems for a four-day period in August 2022. "There is no evidence of any threat actor activity beyond the established timeline," LastPass CEO Karim Toubba said in an update shared on September 15, adding, "there is no … [Read more...] about Hackers Had Access to LastPass’s Development Systems for Four Days
How Cisco Duo Is Simplifying Secure Access for Organizations Around the World
At Cisco Duo, we continually strive to enhance our products to make it easy for security practitioners to apply access policies based on the principles of zero trust. This blog highlights how Duo is achieving that goal by simplifying user and administrator experience and supporting data sovereignty requirements for customers around the world. Read on to get an overview of what … [Read more...] about How Cisco Duo Is Simplifying Secure Access for Organizations Around the World
Get Lifetime Access to 2022 Cybersecurity Certification Prep Courses @ 95% Off
Ever thought about working full-time in cybersecurity? With millions of unfilled jobs around, now is a great time to get into the industry. Of course, there are many different roles in this field. But all of them require the same handful of professional certifications. The 2022 Ultimate Advanced CyberSecurity Professional Certification Bundle helps you collect the full house, … [Read more...] about Get Lifetime Access to 2022 Cybersecurity Certification Prep Courses @ 95% Off
Detect Credential Access with Elastic Security
Within our Elastic Security research group, a strong area of focus is implementing detection mechanisms for capabilities we understand adversaries are currently exploiting within environments. We’ll often wait to see the impact that bringing these capabilities to market will have from a detection standpoint. This allows our researchers to explore different detection strategies … [Read more...] about Detect Credential Access with Elastic Security
T-Mobile Admits Lapsus$ Hackers Gained Access to its Internal Tools and Source Code
Telecom company T-Mobile on Friday confirmed that it was the victim of a security breach in March after the LAPSUS$ mercenary gang managed to gain access to its networks. The acknowledgment came after investigative journalist Brian Krebs shared internal chats belonging to the core members of the group indicating that LAPSUS$ breached the company several times in March prior to … [Read more...] about T-Mobile Admits Lapsus$ Hackers Gained Access to its Internal Tools and Source Code
Get Lifetime Access to This 60-Hour Java Programming Training Bundle @ 97% Discount
Java is a very versatile programming language. From Android apps to Oracle databases, it can be used to power a wide range of software and systems. As with most technical skills, the best way to learn Java is through building your own projects. But you can definitely speed things up with high-quality training. The Complete 2022 Java Coder Bundle provides plenty of that — nine … [Read more...] about Get Lifetime Access to This 60-Hour Java Programming Training Bundle @ 97% Discount