ALPHA SPIDER is the adversary behind the development and operation of the Alphv ransomware as a service (RaaS). Over the last year, ALPHA SPIDER affiliates have been leveraging a variety of novel techniques as part of their ransomware operations. CrowdStrike Services has observed techniques such as the usage of NTFS Alternate Data Streams for hiding a reverse SSH tool, … [Read more...] about The Anatomy of an ALPHA SPIDER Ransomware Attack
attack
KeyTrap attack can take out a DNS server
A group of researchers representing several German universities and institutes have discovered a vulnerability in DNSSEC, a set of extensions to the DNS protocol designed to improve its security, and primarily to counter DNS spoofing. An attack they dubbed KeyTrap, which exploits the vulnerability, can disable a DNS server by sending it a single malicious data packet. Read on … [Read more...] about KeyTrap attack can take out a DNS server
Exposed Docker APIs Under Attack in ‘Commando Cat’ Cryptojacking Campaign
Feb 01, 2024NewsroomCryptojacking / Linux Security Exposed Docker API endpoints over the internet are under assault from a sophisticated cryptojacking campaign called Commando Cat. "The campaign deploys a benign container generated using the Commando project," Cado security researchers Nate Bill and Matt Muir said in a new report published today. "The attacker escapes this … [Read more...] about Exposed Docker APIs Under Attack in ‘Commando Cat’ Cryptojacking Campaign
Getting off the Attack Surface Hamster Wheel: Identity Can Help
IT professionals have developed a sophisticated understanding of the enterprise attack surface – what it is, how to quantify it and how to manage it. The process is simple: begin by thoroughly assessing the attack surface, encompassing the entire IT environment. Identify all potential entry and exit points where unauthorized access could occur. Strengthen these vulnerable … [Read more...] about Getting off the Attack Surface Hamster Wheel: Identity Can Help
New BLUFFS Bluetooth Attack Expose Devices to Adversary-in-the-Middle Attacks
Dec 04, 2023NewsroomEncryption / Technology New research has unearthed multiple novel attacks that break Bluetooth Classic's forward secrecy and future secrecy guarantees, resulting in adversary-in-the-middle (AitM) scenarios between two already connected peers. The issues, collectively named BLUFFS, impact Bluetooth Core Specification 4.2 through 5.4. They are tracked under … [Read more...] about New BLUFFS Bluetooth Attack Expose Devices to Adversary-in-the-Middle Attacks
Iranian Hackers Exploit PLCs in Attack on Water Authority in U.S.
Nov 29, 2023NewsroomCyber Attack / Hacking The U.S. Cybersecurity and Infrastructure Security Agency (CISA) revealed that it's responding to a cyber attack that involved the active exploitation of Unitronics programmable logic controllers (PLCs) to target the Municipal Water Authority of Aliquippa in western Pennsylvania. The attack has been attributed to an Iranian-backed … [Read more...] about Iranian Hackers Exploit PLCs in Attack on Water Authority in U.S.
New ‘HrServ.dll’ Web Shell Detected in APT Attack Targeting Afghan Government
Nov 25, 2023NewsroomCyber Attack / Threat Intelligence An unspecified government entity in Afghanistan was targeted by a previously undocumented web shell called HrServ in what's suspected to be an advanced persistent threat (APT) attack. The web shell, a dynamic-link library (DLL) named "hrserv.dll," exhibits "sophisticated features such as custom encoding methods for client … [Read more...] about New ‘HrServ.dll’ Web Shell Detected in APT Attack Targeting Afghan Government
Critical GitHub Vulnerability Exposes 4,000+ Repositories to Repojacking Attack
Sep 12, 2023THNSoftware Security / Vulnerability A new vulnerability disclosed in GitHub could have exposed thousands of repositories at risk of repojacking attacks, new findings show. The flaw "could allow an attacker to exploit a race condition within GitHub's repository creation and username renaming operations," Checkmarx security researcher Elad Rapoport said in a … [Read more...] about Critical GitHub Vulnerability Exposes 4,000+ Repositories to Repojacking Attack
Employee Falls Victim to SIM Swapping Attack
Aug 26, 2023THNData Breach / SIM Swapping Risk and financial advisory solutions provider Kroll on Friday disclosed that one of its employees fell victim to a "highly sophisticated" SIM swapping attack. The incident, which took place on August 19, 2023, targeted the employee's T-Mobile account, the company said. "Specifically, T-Mobile, without any authority from or contact … [Read more...] about Employee Falls Victim to SIM Swapping Attack
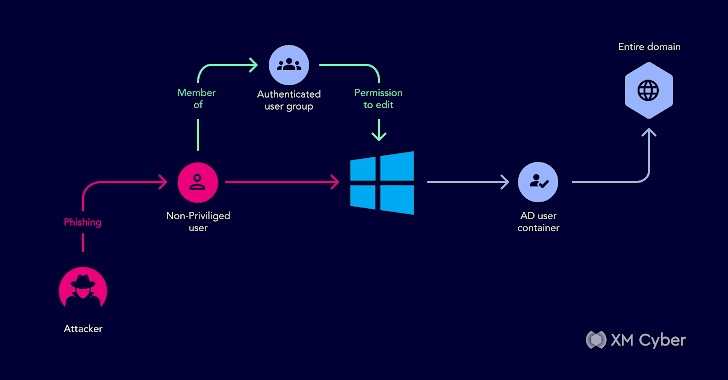
Understanding Active Directory Attack Paths to Improve Security
Introduced in 1999, Microsoft Active Directory is the default identity and access management service in Windows networks, responsible for assigning and enforcing security policies for all network endpoints. With it, users can access various resources across networks. As things tend to do, times, they are a'changin' – and a few years back, Microsoft introduced Azure Active … [Read more...] about Understanding Active Directory Attack Paths to Improve Security