Jun 05, 2023Ravie LakshmananWebsite Security / Magecart Cybersecurity researchers have unearthed a new ongoing Magecart-style web skimmer campaign that's designed to steal personally identifiable information (PII) and credit card data from e-commerce websites. A noteworthy aspect that sets it apart from other Magecart campaigns is that the hijacked sites further serve as … [Read more...] about Magento, WooCommerce, WordPress, and Shopify Exploited in Web Skimmer Attack
attack
How to Reduce Exposure on the Manufacturing Attack Surface
Digitalization initiatives are connecting once-isolated Operational Technology (OT) environments with their Information Technology (IT) counterparts. This digital transformation of the factory floor has accelerated the connection of machinery to digital systems and data. Computer systems for managing and monitoring digital systems and data have been added to the hardware and … [Read more...] about How to Reduce Exposure on the Manufacturing Attack Surface
How Attack Surface Management Supports Continuous Threat Exposure Management
May 11, 2023The Hacker News According to Forrester, External Attack Surface Management (EASM) emerged as a market category in 2021 and gained popularity in 2022. In a different report, Gartner concluded that vulnerability management vendors are expanding their offerings to include Attack Surface Management (ASM) for a suite of comprehensive offensive security … [Read more...] about How Attack Surface Management Supports Continuous Threat Exposure Management
Taiwanese PC Company MSI Falls Victim to Ransomware Attack
Apr 08, 2023Ravie LakshmananMalware / Cyber Attack Taiwanese PC company MSI (short for Micro-Star International) officially confirmed it was the victim of a cyber attack on its systems. The company said it "promptly" initiated incident response and recovery measures after detecting "network anomalies." It also said it alerted law enforcement agencies of the matter. That said, … [Read more...] about Taiwanese PC Company MSI Falls Victim to Ransomware Attack
3CX Desktop App Supply Chain Attack Leaves Millions at Risk
Mar 30, 2023Ravie LakshmananSupply Chain / Software Security 3CX said it's working on a software update for its desktop app after multiple cybersecurity vendors sounded the alarm on what appears to be an active supply chain attack that's using digitally signed and rigged installers of the popular voice and video conferencing software to target downstream customers. "The … [Read more...] about 3CX Desktop App Supply Chain Attack Leaves Millions at Risk
German and South Korean Agencies Warn of Kimsuky’s Expanding Cyber Attack Tactics
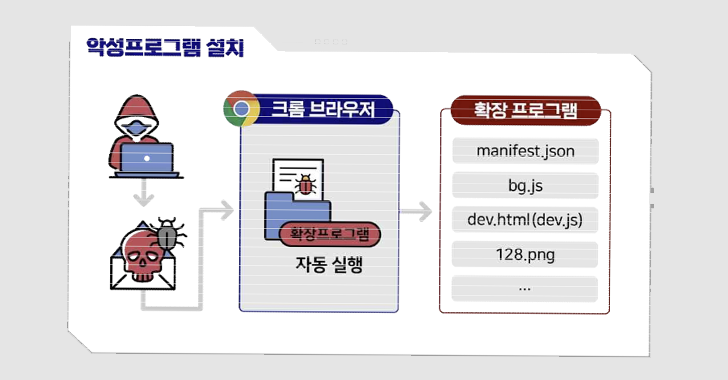
Mar 23, 2023Ravie LakshmananCyber Attack / Browser Security German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes. The joint advisory comes from Germany's domestic intelligence apparatus, the Federal Office for the Protection of the Constitution … [Read more...] about German and South Korean Agencies Warn of Kimsuky’s Expanding Cyber Attack Tactics
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
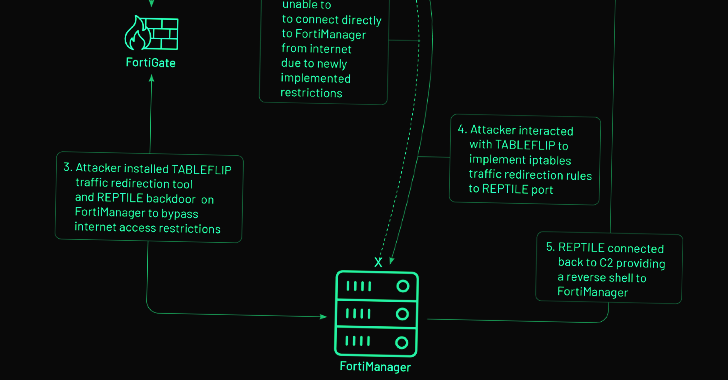
Mar 18, 2023Ravie LakshmananNetwork Security / Cyber Espionage The zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors … [Read more...] about Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
How a man-on-the-side attack works
There are attacks that everyone’s heard of, like distributed denial-of-service (DDoS) attacks; there are those that mostly only professionals know about, such as man-in-the-middle (MitM) attacks; and then there are the rarer, more exotic ones, like man-on-the-side (MotS) attacks. In this post, we talk about the latter in more detail, and discuss how they differ from … [Read more...] about How a man-on-the-side attack works
Massive HTTP DDoS Attack Hits Record High of 71 Million Requests/Second
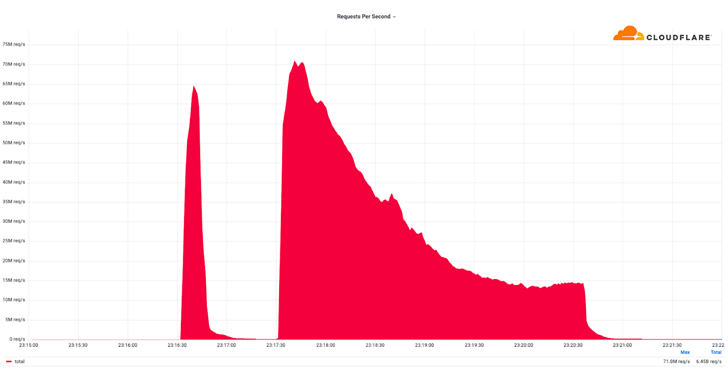
Feb 14, 2023Ravie Lakshmanan Web infrastructure company Cloudflare on Monday disclosed that it thwarted a record-breaking distributed denial-of-service (DDoS) attack that peaked at over 71 million requests per second (RPS). "The majority of attacks peaked in the ballpark of 50-70 million requests per second (RPS) with the largest exceeding 71 million," the company said, … [Read more...] about Massive HTTP DDoS Attack Hits Record High of 71 Million Requests/Second
Malware Attack on CircleCI Engineer’s Laptop Leads to Recent Security Incident
Jan 14, 2023Ravie LakshmananDevOps / Data Security DevOps platform CircleCI on Friday disclosed that unidentified threat actors compromised an employee's laptop and leveraged malware to steal their two-factor authentication-backed credentials to breach the company's systems and data last month. The CI/CD service CircleCI said the "sophisticated attack" took place on December … [Read more...] about Malware Attack on CircleCI Engineer’s Laptop Leads to Recent Security Incident