Movies and TV shows have been a huge source of comfort for many in these COVID times, and the number of new shows on Netflix, Amazon Prime, and the like has skyrocketed. But when searching for the latest megahit, don’t neglect basic security measures or you might find that someone else is enjoying it at your expense — or worse, that the money in your bank account has … [Read more...] about Phishing attacks on users of streaming services
attacks
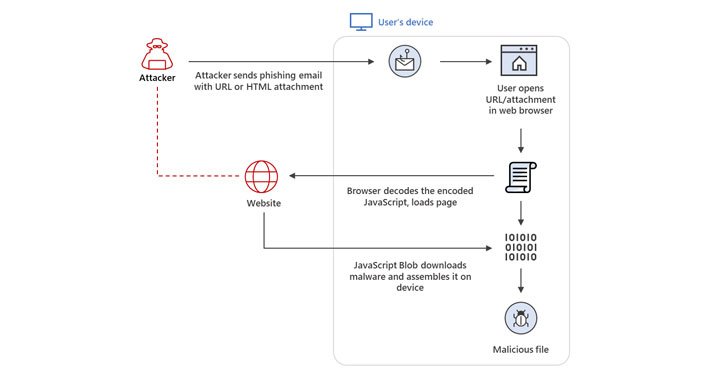
Hackers Increasingly Using HTML Smuggling in Malware and Phishing Attacks
Threat actors are increasingly banking on the technique of HTML smuggling in phishing campaigns as a means to gain initial access and deploy an array of threats, including banking malware, remote administration trojans (RATs), and ransomware payloads. Microsoft 365 Defender Threat Intelligence Team, in a new report published Thursday, disclosed that it identified infiltrations … [Read more...] about Hackers Increasingly Using HTML Smuggling in Malware and Phishing Attacks
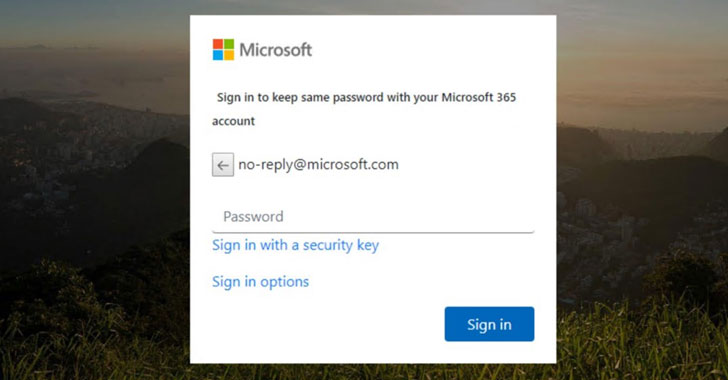
Microsoft Warns of TodayZoo Phishing Kit Used in Extensive Credential Stealing Attacks
Microsoft on Thursday disclosed an "extensive series of credential phishing campaigns" that takes advantage of a custom phishing kit that stitched together components from at least five different widely circulated ones with the goal of siphoning user login information. The tech giant's Microsoft 365 Defender Threat Intelligence Team, which detected the first instances of the … [Read more...] about Microsoft Warns of TodayZoo Phishing Kit Used in Extensive Credential Stealing Attacks
“Left of Boom” Cybersecurity: Proactive Cybersecurity in a Time of Increasing Threats and Attacks
“Left of Boom” The allied military forces engaged in operations in Iraq and Afghanistan nearly 20 years ago were confronted with the challenge of Improvised Explosive Devices (IEDs), which were roadside bombs that detonated remotely and inflicted casualties and damage to military personnel and materiel. Major research efforts on how to detect these IEDs and detonate them … [Read more...] about “Left of Boom” Cybersecurity: Proactive Cybersecurity in a Time of Increasing Threats and Attacks
New Patch Released for Actively Exploited 0-Day Apache Path Traversal to RCE Attacks
The Apache Software Foundation on Thursday released additional security updates for its HTTP Server product to remediate what it says is an "incomplete fix" for an actively exploited path traversal and remote code execution flaw that it patched earlier this week. CVE-2021-42013, as the new vulnerability is identified as, builds upon CVE-2021-41773, a flaw that impacted Apache … [Read more...] about New Patch Released for Actively Exploited 0-Day Apache Path Traversal to RCE Attacks
Ban attacks on Instagram users
If you run a popular blog and promote your business through Instagram, an account ban simply isn’t in the plan. For responsible users, the idea of being banned for, say, displaying suicidal content or trying to impersonate someone else might seem like a bad dream or a cruel joke, but it’s quite real for victims of the new wave of so-called ban attacks. Here’s how these attacks … [Read more...] about Ban attacks on Instagram users
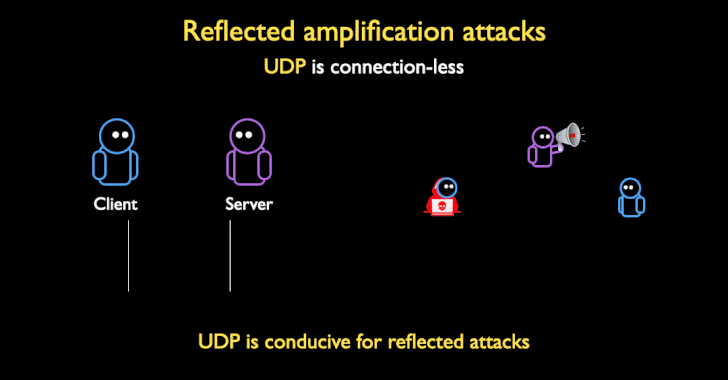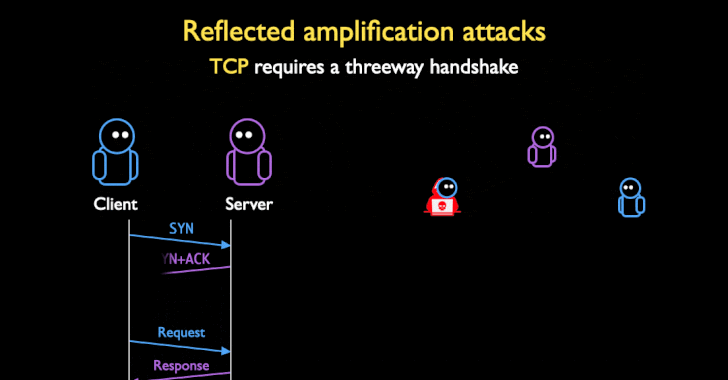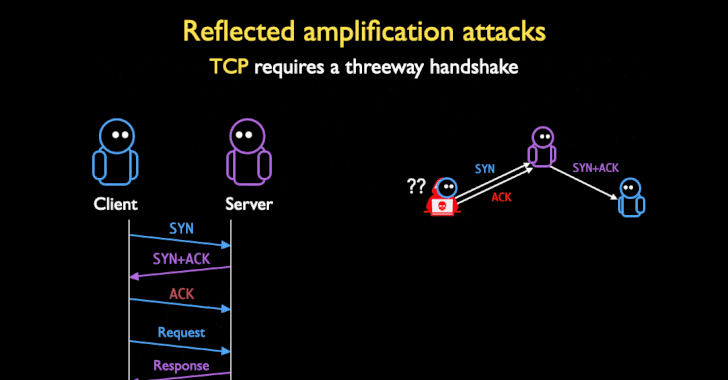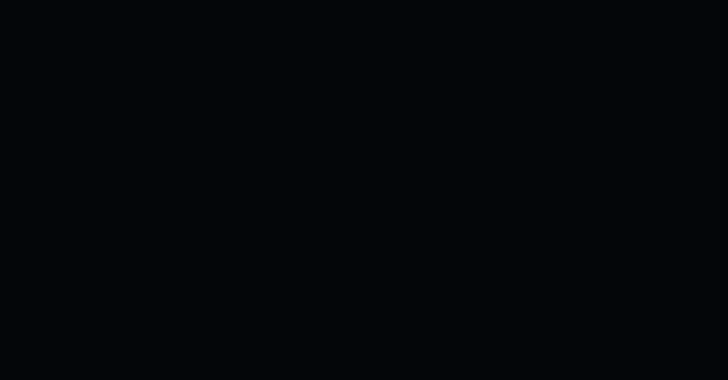
Attackers Can Weaponize Firewalls and Middleboxes for Amplified DDoS Attacks
Weaknesses in the implementation of TCP protocol in middleboxes and censorship infrastructure could be weaponized as a vector to stage reflected denial of service (DoS) amplification attacks, surpassing many of the existing UDP-based amplification factors to date. Detailed by a group of academics from the University of Maryland and the University of Colorado Boulder at the … [Read more...] about Attackers Can Weaponize Firewalls and Middleboxes for Amplified DDoS Attacks
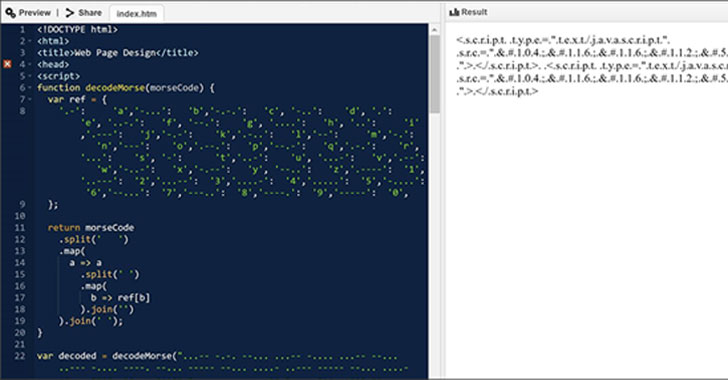
Hackers Spotted Using Morse Code in Phishing Attacks to Evade Detection
Microsoft has disclosed details of an evasive year-long social engineering campaign wherein the operators kept changing their obfuscation and encryption mechanisms every 37 days on average, including relying on Morse code, in an attempt to cover their tracks and surreptitiously harvest user credentials. The phishing attacks take the form of invoice-themed lures mimicking … [Read more...] about Hackers Spotted Using Morse Code in Phishing Attacks to Evade Detection
Healthcare organizations are a focus of ransomware attacks
The adoption of electronic health records (EHRs) and even faster adoption of wireless medical devices and telemedicine has made patient information more accessible by more people. Over the past year and a half that’s been tremendously beneficial. The shift to remote care and the widespread adoption of EHR solutions by health systems have shaped digital transformation in … [Read more...] about Healthcare organizations are a focus of ransomware attacks
Experts Believe Chinese Hackers Are Behind Several Attacks Targeting Israel
A Chinese cyber espionage group has been linked to a string of intrusion activities targeting Israeli government institutions, IT providers, and telecommunications companies at least since 2019. FireEye's Mandiant threat intelligence arm attributed the campaign to an operator it tracks as "UNC215", a Chinese espionage operation that's believed to have singled out organizations … [Read more...] about Experts Believe Chinese Hackers Are Behind Several Attacks Targeting Israel