All of this means that if we want to minimize surprise FPs between model releases, we must ensure DV ordering preservation. XGBoost is flexible because its Newton-Raphson solver requires only the gradient and Hessian of the objective rather than the objective itself. By adding small perturbations to the gradient and to the Hessian, we can replace the standard XGBoost … [Read more...] about CrowdStrike Researchers Develop Custom XGBoost Objective
Custom
Chinese Hackers Breach Juniper Networks Routers With Custom Backdoors and Rootkits
Mar 12, 2025Ravie LakshmananCyber Espionage / Vulnerability The China-nexus cyber espionage group tracked as UNC3886 has been observed targeting end-of-life MX routers from Juniper Networks as part of a campaign designed to deploy custom backdoors, highlighting their ability to focus on internal networking infrastructure. "The backdoors had varying custom capabilities, … [Read more...] about Chinese Hackers Breach Juniper Networks Routers With Custom Backdoors and Rootkits
Connect a custom AWS S3 snapshot repository to Elastic Cloud
In this blog, we will walk through backing up our committed cluster data via Elasticsearch’s snapshots into an AWS S3 bucket. In Elastic Cloud (Enterprise), Elastic provides a built-in backup service under its found-snapshots repository. Elasticsearch also supports custom repositories for both Cloud and on-prem setups, connecting to data stores like AWS S3, GCP, and Azure for … [Read more...] about Connect a custom AWS S3 snapshot repository to Elastic Cloud
Build Custom Apps to Solve Tough Security Challenges
Security teams can easily build custom applications with a unified homepage experience, intuitive visual builder and access to modern low-code and no-code tools. This builder guides them through the building blocks necessary to develop an application before it is released and installed. A new learn page allows app developers to easily access guided documentation and … [Read more...] about Build Custom Apps to Solve Tough Security Challenges
CosmicBeetle Deploys Custom ScRansom Ransomware, Partnering with RansomHub
The threat actor known as CosmicBeetle has debuted a new custom ransomware strain called ScRansom in attacks targeting small- and medium-sized businesses (SMBs) in Europe, Asia, Africa, and South America, while also likely working as an affiliate for RansomHub. "CosmicBeetle replaced its previously deployed ransomware, Scarab, with ScRansom, which is continually improved," ESET … [Read more...] about CosmicBeetle Deploys Custom ScRansom Ransomware, Partnering with RansomHub
Operationalizing our custom “SOC in a Box” at the RSA Conference 2024
Ever had to stand up a Security Operations Center (SOC) in two days? This is the monumental challenge faced by Cisco engineers at various events and conferences around the globe throughout the year. You may ask, “How is it possible to deploy a full-fledged SOC with just two days of preparation?” The key to being able to make the nearly impossible happen is our custom “SOC in a … [Read more...] about Operationalizing our custom “SOC in a Box” at the RSA Conference 2024
Researchers Uncover Powerful Backdoor and Custom Implant in Year-Long Cyber Campaign
May 15, 2023Ravie LakshmananCyber Threat / Malware Government, aviation, education, and telecom sectors located in South and Southeast Asia have come under the radar of a new hacking group as part of a highly-targeted campaign that commenced in mid-2022 and continued into the first quarter of 2023. Symantec, by Broadcom Software, is tracking the activity under its … [Read more...] about Researchers Uncover Powerful Backdoor and Custom Implant in Year-Long Cyber Campaign
Introduction to custom machine learning models and maps
Introduction to custom machine learning models and mapsHow to use text-based datasets to build beautiful dashboards leveraging mapsEnglish简体中文한국어日本語FrançaisDeutschEspañolPortuguêsIn Elasticsearch 8.0, we introduced the ability to run custom machine learning models, such as the ones based on BERT (Bidirectional Encoder Representations from Transformers), to perform natural … [Read more...] about Introduction to custom machine learning models and maps
How Falcon OverWatch Detected SILENT CHOLLIMA’s Custom Tooling
CrowdStrike Falcon OverWatch™ recently released its annual threat hunting report, detailing the interactive intrusion activity observed by hunters over the course of the past year. The tactics, techniques and procedures (TTPs) an adversary uses serve as key indicators to threat hunters of who might be behind an intrusion. OverWatch threat hunters uncovered an intrusion against … [Read more...] about How Falcon OverWatch Detected SILENT CHOLLIMA’s Custom Tooling
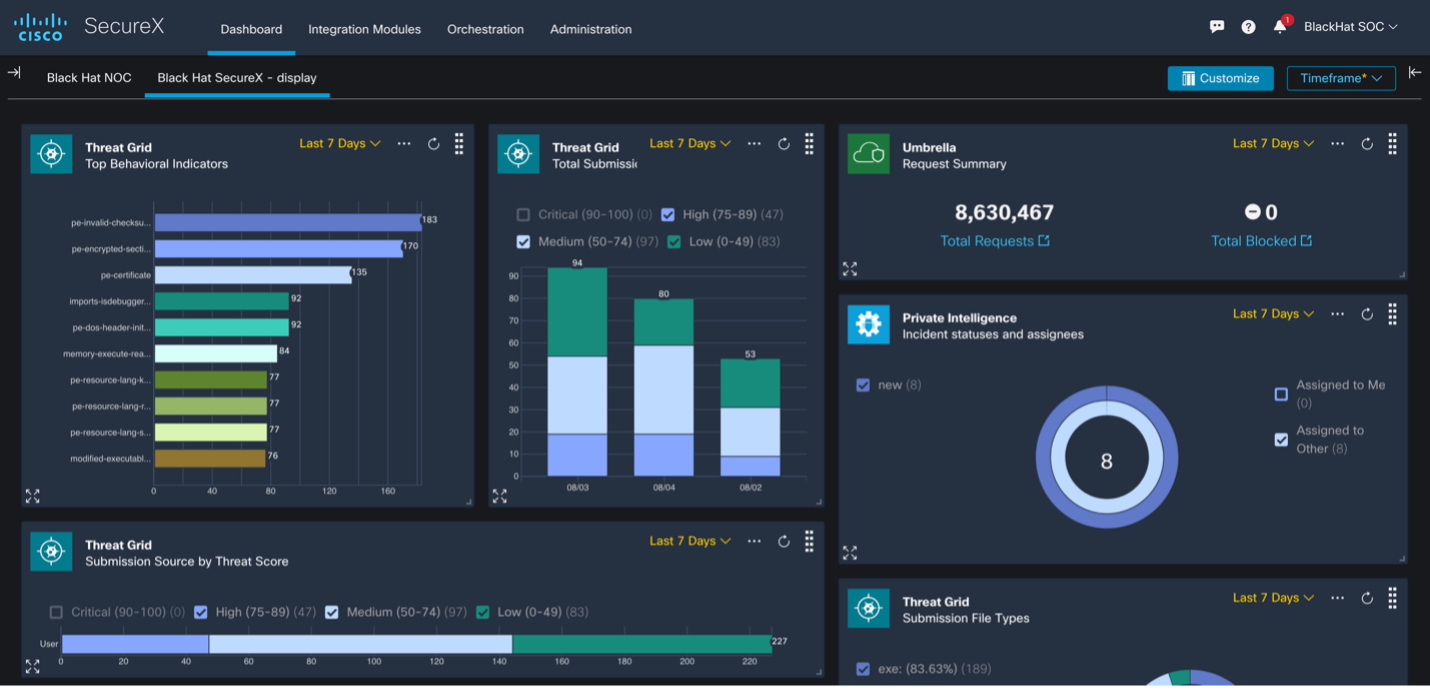
Building a Custom SecureX Orchestration Workflow for Umbrella
Improving efficiency for the Cisco team in the Black Hat USA NOC As a proud partner of the Black Hat USA NOC, Cisco deployed multiple technologies along with the other Black Hat NOC partners to build a stable and secure network for the conference. We used Cisco Secure Malware Analytics to analyze files and monitor any potential PII leaks. We also used Meraki SM to manage over … [Read more...] about Building a Custom SecureX Orchestration Workflow for Umbrella