When Tahir Ali became CTO and CISO at Montage Health in 2021, he inherited a unique set of cybersecurity challenges. For one, the healthcare sector was getting bombarded with attacks, including distributed denial of service (DDoS), phishing and social engineering attacks. At the same time, the California-based nonprofit healthcare system was integrating more networked medical … [Read more...] about Montage Health Consolidates Its Cybersecurity Strategy with CrowdStrike
cybersecurity
Demystifying a Common Cybersecurity Myth
Mar 13, 2024The Hacker NewsApp Security / Cyber Security One of the most common misconceptions in file upload cybersecurity is that certain tools are "enough" on their own—this is simply not the case. In our latest whitepaper OPSWAT CEO and Founder, Benny Czarny, takes a comprehensive look at what it takes to prevent malware threats in today's ever-evolving file upload … [Read more...] about Demystifying a Common Cybersecurity Myth
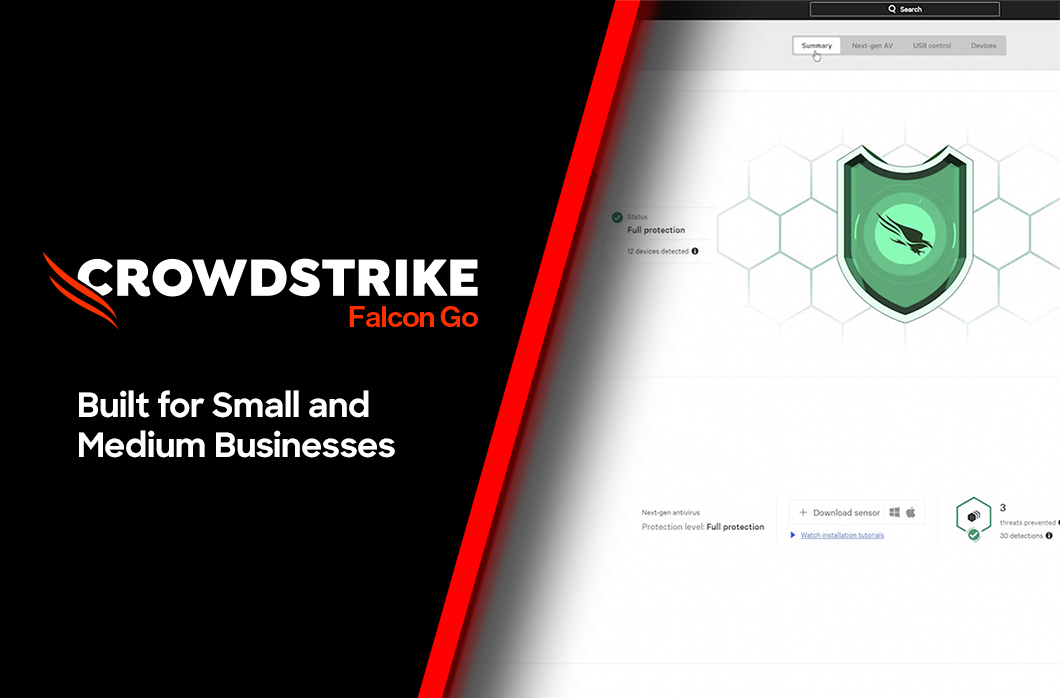
CrowdStrike Brings AI-Powered Cybersecurity to SMBs
Cyber risks for small and medium-sized businesses (SMBs) have never been higher. SMBs face a barrage of attacks, including ransomware, malware and variations of phishing/vishing. This is one reason why the Cybersecurity and Infrastructure Security Agency (CISA) states “thousands of SMBs have been harmed by ransomware attacks, with small businesses three times more likely to be … [Read more...] about CrowdStrike Brings AI-Powered Cybersecurity to SMBs
The Importance of Continuous Security Monitoring for a Robust Cybersecurity Strategy
Nov 14, 2023The Hacker NewsPen Testing / Vulnerability Management In 2023, the global average cost of a data breach reached $4.45 million. Beyond the immediate financial loss, there are long-term consequences like diminished customer trust, weakened brand value, and derailed business operations. In a world where the frequency and cost of data breaches are skyrocketing, … [Read more...] about The Importance of Continuous Security Monitoring for a Robust Cybersecurity Strategy
Empowering cyber resilience through the US Tribal Cybersecurity Grant Program (TCGP)
"Enhanced logging" isn't just a buzzword in cybersecurity; it's essential. Elastic®, a leader in this area, provides unmatched log monitoring solutions and comprehensive insights based on log data. By leveraging Elastic for log management, Tribal governments gain:Comprehensive management of large log data setsQuick insights across varied log typesSpeedy access to critical … [Read more...] about Empowering cyber resilience through the US Tribal Cybersecurity Grant Program (TCGP)
3 Recommendations for a Next-Gen Cybersecurity Framework
Cyberattacks evolve daily, and defenders are forced to adapt at the same rate. Cybersecurity best practices, however, are updated and codified much less frequently. There is broad experimentation in the field, and it takes some time for authoritative working groups to sort out which new practices and controls are practical and consistently effective for a large cross-section of … [Read more...] about 3 Recommendations for a Next-Gen Cybersecurity Framework
Elastic wins CyberSecurity Breakthrough Award for Cloud Platform of the Year 2023
Elastic Security for Cloud also includes cloud-native vulnerability management capabilities. This continuously uncovers vulnerabilities in AWS EC2 with zero resource utilization on workloads. Elastic identifies, reports, and guides remediation of these vulnerabilities to help you identify and respond to potential risk.Elastic Security for Cloud is also supported by Elastic … [Read more...] about Elastic wins CyberSecurity Breakthrough Award for Cloud Platform of the Year 2023
Essential Guide to Cybersecurity Compliance
SOC 2, ISO, HIPAA, Cyber Essentials – all the security frameworks and certifications today are an acronym soup that can make even a compliance expert's head spin. If you're embarking on your compliance journey, read on to discover the differences between standards, which is best for your business, and how vulnerability management can aid compliance. What is cybersecurity … [Read more...] about Essential Guide to Cybersecurity Compliance
CISOs Tout SaaS Cybersecurity Confidence, But 79% Admit to SaaS Incidents, New Report Finds
A new State of SaaS Security Posture Management Report from SaaS cybersecurity provider AppOmni indicates that Cybersecurity, IT, and business leaders alike recognize SaaS cybersecurity as an increasingly important part of the cyber threat landscape. And at first glance, respondents appear generally optimistic about their SaaS cybersecurity. Over 600 IT, cybersecurity, and … [Read more...] about CISOs Tout SaaS Cybersecurity Confidence, But 79% Admit to SaaS Incidents, New Report Finds
Video Series Spotlights Cybersecurity Leaders
You don’t have a malware problem — you have an adversary problem. CrowdStrike has relentlessly focused on finding and stopping the humans behind cyberattacks. Today, we’re launching a new series that highlights the people who fight back against these threats every day. We’re excited to announce the launch of the Protectors Spotlight, a new series of short videos celebrating the … [Read more...] about Video Series Spotlights Cybersecurity Leaders