X How to Contain an Infected System Hi, there. My name’s Peter Ingebrigtsen. And today, we’ve logged into the falcon.crowdstrike.com, or the Falcon User Interface. And what we’re going to do is take a look at some of our systems and recognize that some of them are either currently under attack or recently been under attack, and may have been compromised. And we’d like to … [Read more...] about How to manage USB devices
Devices
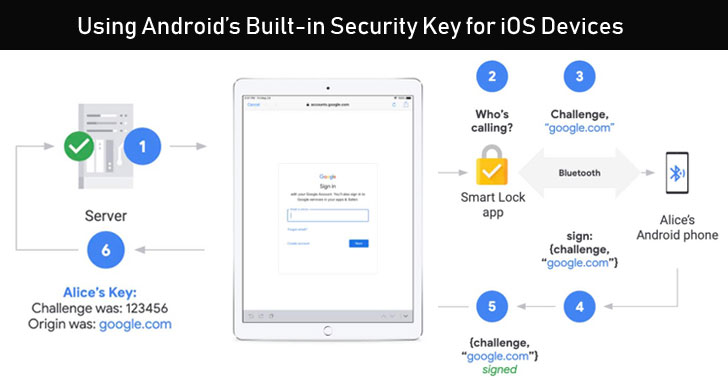
Android’s Built-in Security Key Now Works With iOS Devices For Secure Login
In April this year, a software update from Google overnight turned all Android phones, running Android 7.0 Nougat and up, into a FIDO-certified hardware security key as part of a push to encourage two-step verification.The feature made it possible for users to confirm their identity when logging into a Google account more effortless and secure, without separately managing and … [Read more...] about Android’s Built-in Security Key Now Works With iOS Devices For Secure Login