Apr 13, 2023Ravie LakshmananMalware / Cyber Attack The Transparent Tribe threat actor has been linked to a set of weaponized Microsoft Office documents in attacks targeting the Indian education sector using a continuously maintained piece of malware called Crimson RAT. While the suspected Pakistan-based threat group is known to target military and government entities in the … [Read more...] about Pakistan-based Transparent Tribe Hackers Targeting Indian Educational Institutions
Hackers
Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise
Apr 08, 2023Ravie LakshmananCyber War / Cyber Threat The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation. That's according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud … [Read more...] about Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise
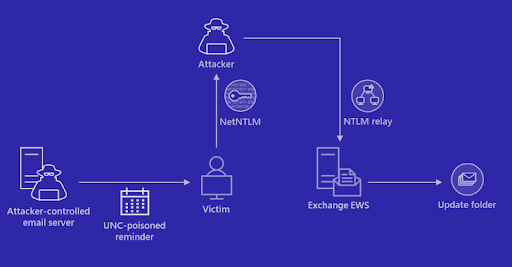
Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers
Mar 25, 2023Ravie LakshmananEnterprise Security / Microsoft Microsoft on Friday shared guidance to help customers discover indicators of compromise (IoCs) associated with a recently patched Outlook vulnerability. Tracked as CVE-2023-23397 (CVSS score: 9.8), the critical flaw relates to a case of privilege escalation that could be exploited to steal NT Lan Manager (NTLM) … [Read more...] about Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers
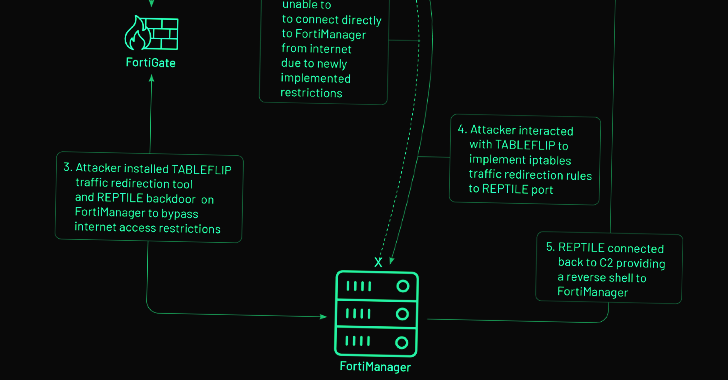
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
Mar 18, 2023Ravie LakshmananNetwork Security / Cyber Espionage The zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors … [Read more...] about Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
North Korean UNC2970 Hackers Expands Operations with New Malware Families
Mar 10, 2023Ravie LakshmananCyber Attack / Malware A North Korean espionage group tracked as UNC2970 has been observed employing previously undocumented malware families as part of a spear-phishing campaign targeting U.S. and European media and technology organizations since June 2022. Google-owned Mandiant said the threat cluster shares "multiple overlaps" with a … [Read more...] about North Korean UNC2970 Hackers Expands Operations with New Malware Families
Dutch Police Arrest 3 Hackers Involved in Massive Data Theft and Extortion Scheme
Feb 27, 2023Ravie Lakshmanan The Dutch police announced the arrest of three individuals in connection with a "large-scale" criminal operation involving data theft, extortion, and money laundering. The suspects include two 21-year-old men from Zandvoort and Rotterdam and an 18-year-old man without a permanent residence. The arrests were made on January 23, 2023. It's estimated … [Read more...] about Dutch Police Arrest 3 Hackers Involved in Massive Data Theft and Extortion Scheme
Chinese Tonto Team Hackers’ Second Attempt to Target Cybersecurity Firm Group-IB Fails
Feb 13, 2023Ravie LakshmananCyber Threat Intelligence The advanced persistent threat (APT) actor known as Tonto Team carried out an unsuccessful attack on cybersecurity company Group-IB in June 2022. The Singapore-headquartered firm said that it detected and blocked malicious phishing emails originating from the group targeting its employees. It's also the second attack aimed … [Read more...] about Chinese Tonto Team Hackers’ Second Attempt to Target Cybersecurity Firm Group-IB Fails
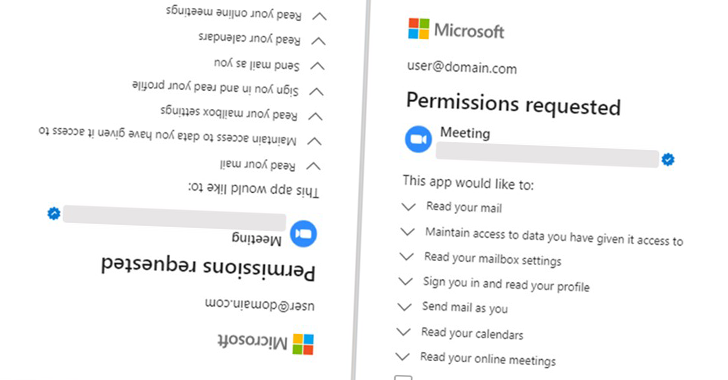
Hackers Abused Microsoft’s “Verified Publisher” OAuth Apps to Breach Corporate Email Accounts
Feb 01, 2023Ravie LakshmananEnterprise Security / Authentication Microsoft on Tuesday said it took steps to disable fake Microsoft Partner Network (MPN) accounts that were used for creating malicious OAuth applications as part of a malicious campaign designed to breach organizations' cloud environments and steal email. "The applications created by these fraudulent actors were … [Read more...] about Hackers Abused Microsoft’s “Verified Publisher” OAuth Apps to Breach Corporate Email Accounts
Chinese Hackers Exploited Recent Fortinet Flaw as 0-Day to Drop Malware
Jan 20, 2023Ravie LakshmananFirewall / Network Security A suspected China-nexus threat actor exploited a recently patched vulnerability in Fortinet FortiOS SSL-VPN as a zero-day in attacks targeting a European government entity and a managed service provider (MSP) located in Africa. Telemetry evidence gathered by Google-owned Mandiant indicates that the exploitation occurred … [Read more...] about Chinese Hackers Exploited Recent Fortinet Flaw as 0-Day to Drop Malware
Russian Turla Hackers Hijack Decade-Old Malware Infrastructure to Deploy New Backdoors
Jan 08, 2023Ravie LakshmananCyberespionage / Threat Analysis The Russian cyberespionage group known as Turla has been observed piggybacking on attack infrastructure used by a decade-old malware to deliver its own reconnaissance and backdoor tools to targets in Ukraine. Google-owned Mandiant, which is tracking the operation under the uncategorized cluster moniker UNC4210, said … [Read more...] about Russian Turla Hackers Hijack Decade-Old Malware Infrastructure to Deploy New Backdoors