Jan 20, 2025Ravie LakshmananNetwork Security / Vulnerability New research has uncovered security vulnerabilities in multiple tunneling protocols that could allow attackers to perform a wide range of attacks. "Internet hosts that accept tunneling packets without verifying the sender's identity can be hijacked to perform anonymous attacks and provide access to their networks," … [Read more...] about Unsecured Tunneling Protocols Expose 4.2 Million Hosts, Including VPNs and Routers
hosts
Technical Details: Falcon Update for Windows Hosts
What Happened? On July 19, 2024 at 04:09 UTC, as part of ongoing operations, CrowdStrike released a sensor configuration update to Windows systems. Sensor configuration updates are an ongoing part of the protection mechanisms of the Falcon platform. This configuration update triggered a logic error resulting in a system crash and blue screen (BSOD) on impacted systems. The … [Read more...] about Technical Details: Falcon Update for Windows Hosts
Critical Tinyproxy Flaw Opens Over 50,000 Hosts to Remote Code Execution
May 06, 2024NewsroomVulnerability / Server Security More than 50% of the 90,310 hosts have been found exposing a Tinyproxy service on the internet that's vulnerable to a critical unpatched security flaw in the HTTP/HTTPS proxy tool. The issue, tracked as CVE-2023-49606, carries a CVSS score of 9.8 out of a maximum of 10, per Cisco Talos, which described it as a use-after-free … [Read more...] about Critical Tinyproxy Flaw Opens Over 50,000 Hosts to Remote Code Execution
Hackers Abusing GitHub to Evade Detection and Control Compromised Hosts
Dec 19, 2023The Hacker NewsSoftware Security / Threat intelligence Threat actors are increasingly making use of GitHub for malicious purposes through novel methods, including abusing secret Gists and issuing malicious commands via git commit messages. "Malware authors occasionally place their samples in services like Dropbox, Google Drive, OneDrive, and Discord to host second … [Read more...] about Hackers Abusing GitHub to Evade Detection and Control Compromised Hosts
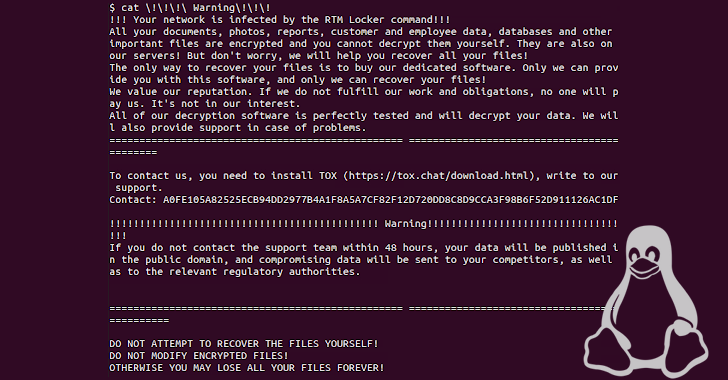
RTM Locker’s First Linux Ransomware Strain Targeting NAS and ESXi Hosts
Apr 27, 2023Ravie LakshmananLinux / Endpoint Security The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system. "Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs … [Read more...] about RTM Locker’s First Linux Ransomware Strain Targeting NAS and ESXi Hosts
How to Edit Hosts file in Mac OS X 10.11 El Capitan
The hosts file is used by your computer to map hostnames to IP addresses. By adding or removing lines to your hosts file you can change where certain domains will point when you access them in a browser or using other software. You can block certain hosts names, like ad-serving/malicious hosts, or used for web development purposes, i.e. to redirect domains to local … [Read more...] about How to Edit Hosts file in Mac OS X 10.11 El Capitan
How to Edit Hosts file in Mac OS X 10.10 Yosemite
The hosts file is used by your computer to map hostnames to IP addresses. By adding or removing lines to your hosts file you can change where certain domains will point when you access them in a browser or using other software. You can block certain hosts names, like ad-serving/malicious hosts, or used for web development purposes, i.e. to redirect domains to local … [Read more...] about How to Edit Hosts file in Mac OS X 10.10 Yosemite
How to Edit Hosts file in Mac OS X 10.9 Mavericks
The hosts file is used by your computer to map hostnames to IP addresses. By adding or removing lines to your hosts file you can change where certain domains will point when you access them in a browser or using other software. You can block certain hosts names, like ad-serving/malicious hosts, or used for web development purposes, i.e. to redirect domains to local … [Read more...] about How to Edit Hosts file in Mac OS X 10.9 Mavericks