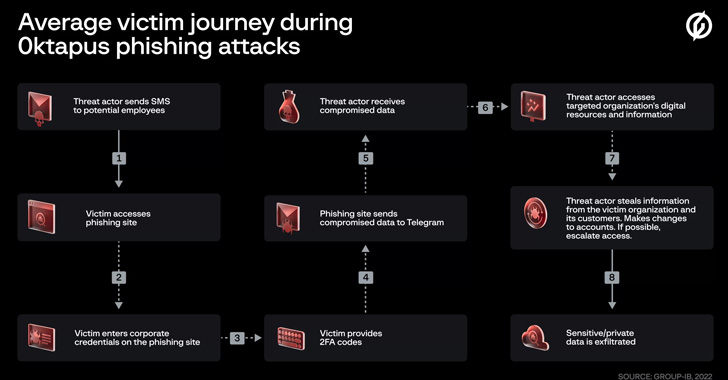
The threat actor behind the attacks on Twilio and Cloudflare earlier this month has been linked to a broader phishing campaign aimed at 136 organizations that resulted in a cumulative compromise of 9,931 accounts. The activity has been condemned 0ktapus by Group-IB because the initial goal of the attacks was to "obtain Okta identity credentials and two-factor authentication … [Read more...] about Okta Hackers Behind Twilio and Cloudflare Breach Hit Over 130 Organizations
information security
Crypto Miners Using Tox P2P Messenger as Command and Control Server
Threat actors have begun to use the Tox peer-to-peer instant messaging service as a command-and-control method, marking a shift from its earlier role as a contact method for ransomware negotiations. The findings from Uptycs, which analyzed an Executable and Linkable Format (ELF) artifact ("72client") that functions as a bot and can run scripts on the compromised host using the … [Read more...] about Crypto Miners Using Tox P2P Messenger as Command and Control Server
Google Uncovers Tool Used by Iranian Hackers to Steal Data from Email Accounts
The Iranian government-backed actor known as Charming Kitten has added a new tool to its malware arsenal that allows it to retrieve user data from Gmail, Yahoo!, and Microsoft Outlook accounts. Dubbed HYPERSCRAPE by Google Threat Analysis Group (TAG), the actively in-development malicious software is said to have been used against less than two dozen accounts in Iran, with the … [Read more...] about Google Uncovers Tool Used by Iranian Hackers to Steal Data from Email Accounts
Researchers Find Counterfeit Phones with Backdoor to Hack WhatsApp Accounts
Budget Android device models that are counterfeit versions associated with popular smartphone brands are harboring multiple trojans designed to target WhatsApp and WhatsApp Business messaging apps. The trojans, which Doctor Web first came across in July 2022, were discovered in the system partition of at least four different smartphones: P48pro, radmi note 8, Note30u, and … [Read more...] about Researchers Find Counterfeit Phones with Backdoor to Hack WhatsApp Accounts
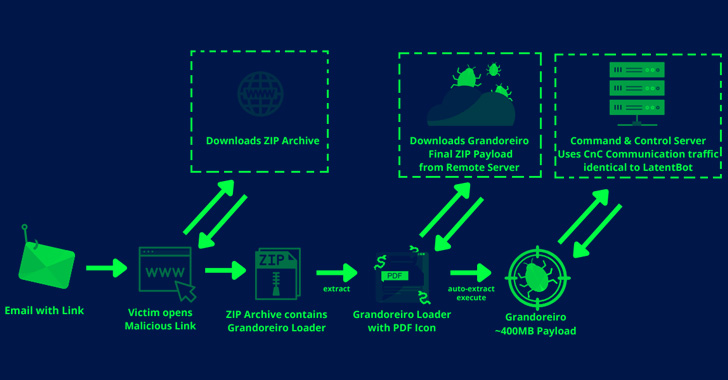
New Grandoreiro Banking Malware Campaign Targeting Spanish Manufacturers
Organizations in the Spanish-speaking nations of Mexico and Spain are in the crosshairs of a new campaign designed to deliver the Grandoreiro banking trojan. "In this campaign, the threat actors impersonate government officials from the Attorney General's Office of Mexico City and from the Public Ministry in the form of spear-phishing emails in order to lure victims to … [Read more...] about New Grandoreiro Banking Malware Campaign Targeting Spanish Manufacturers
Become a Cybersecurity Expert with 18 New Online Courses @ 98% OFF
With more data stored in the cloud than ever before, now is a good time to get into cybersecurity. Many top corporations are looking for new talent, and even junior professionals can earn $80,000 or more. The only barrier to entry is education. How do you learn about security protocols and white hat hacking? Enter the All-In-One 2022 Super-Sized Ethical Hacking Bundle. This … [Read more...] about Become a Cybersecurity Expert with 18 New Online Courses @ 98% OFF
DoNot Team Hackers Updated its Malware Toolkit with Improved Capabilities
The Donot Team threat actor has updated its Jaca Windows malware toolkit with improved capabilities, including a revamped stealer module designed to plunder information from Google Chrome and Mozilla Firefox browsers. The improvements also include a new infection chain that incorporates previously undocumented components to the modular framework, Morphisec researchers Hido … [Read more...] about DoNot Team Hackers Updated its Malware Toolkit with Improved Capabilities
Researchers Detail Evasive DarkTortilla Crypter Used to Deliver Malware
A .NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute a broad array of commodity malware as well as targeted payloads like Cobalt Strike and Metasploit, likely since 2015. "It can also deliver 'add-on packages' such as additional malicious payloads, benign decoy documents, and executables," cybersecurity firm Secureworks said in a … [Read more...] about Researchers Detail Evasive DarkTortilla Crypter Used to Deliver Malware
Cybercriminals Developing BugDrop Malware to Bypass Android Security Features
In a sign that malicious actors continue to find ways to work around Google Play Store security protections, researchers have spotted a previously undocumented Android dropper trojan that's currently in development. "This new malware tries to abuse devices using a novel technique, not seen before in Android malware, to spread the extremely dangerous Xenomorph banking trojan, … [Read more...] about Cybercriminals Developing BugDrop Malware to Bypass Android Security Features
ÆPIC and SQUIP Vulnerabilities Found in Intel and AMD Processors
A group of researchers has revealed details of a new vulnerability affecting Intel CPUs that enables attackers to obtain encryption keys and other secret information from the processors. Dubbed ÆPIC Leak, the weakness is the first-of-its-kind to architecturally disclose sensitive data in a manner that's akin to an "uninitialized memory read in the CPU itself." "In contrast to … [Read more...] about ÆPIC and SQUIP Vulnerabilities Found in Intel and AMD Processors