,The rapid software development process that exists today requires an expanding and complex infrastructure and application components, and the job of operations and development teams is ever growing and multifaceted. Observability, which helps manage and analyze telemetry data, is the key to ensuring the performance and reliability of your applications and infrastructure. In … [Read more...] about The power of effective log management in software development and operations
Log
Centralized Log Management Best Practices and Tools
What is centralized log management? And why bother?Centralized logging is a critical component of observability into modern infrastructure and applications. Without it, it can be difficult to diagnose problems and understand user journeys—leaving engineers blind to production incidents or interrupted customer experiences. Alternatively, when the right engineers can access the … [Read more...] about Centralized Log Management Best Practices and Tools
Make Compliance a Breeze with Modern Log Management
From manufacturers in Michigan to fintechs in Finland, every business must comply with industry regulations — which are increasingly constraining. At the same time, businesses must protect and account for a growing number of systems, applications and data in order to remain compliant. In other words, compliance is getting harder. Enter log management. While regulations vary by … [Read more...] about Make Compliance a Breeze with Modern Log Management
Make Compliance a Breeze with Modern Log Management
From manufacturers in Michigan to fintechs in Finland, every business must comply with industry regulations — which are increasingly constraining. At the same time, businesses must protect and account for a growing number of systems, applications and data in order to remain compliant. In other words, compliance is getting harder. Enter log management. While regulations vary by … [Read more...] about Make Compliance a Breeze with Modern Log Management
Making the most of your unstructured log data through enterprise log management
As we mentioned before, this is the single most important step for indexing custom logs. Technically these fixes are optional, but doing so allows you to get the most value from your unstructured logs. The log messages themselves are still unstructured and could contain anything — logs of text, numbers, expectations, errors, you name it.If you expand and review one of your log … [Read more...] about Making the most of your unstructured log data through enterprise log management
Product Spotlight: Power Search for Log Restore
We’re excited to announce significant improvements to our Archive+Restore capabilities – which enables low-cost long term log storage in AWS S3 or Azure Blob, while providing access to ingest those logs into Logz.io at any time.The first enhancement is Power Search, which will make it faster to restore logs from archived log data in AWS S3 (and soon for Azure Blob) in our Open … [Read more...] about Product Spotlight: Power Search for Log Restore
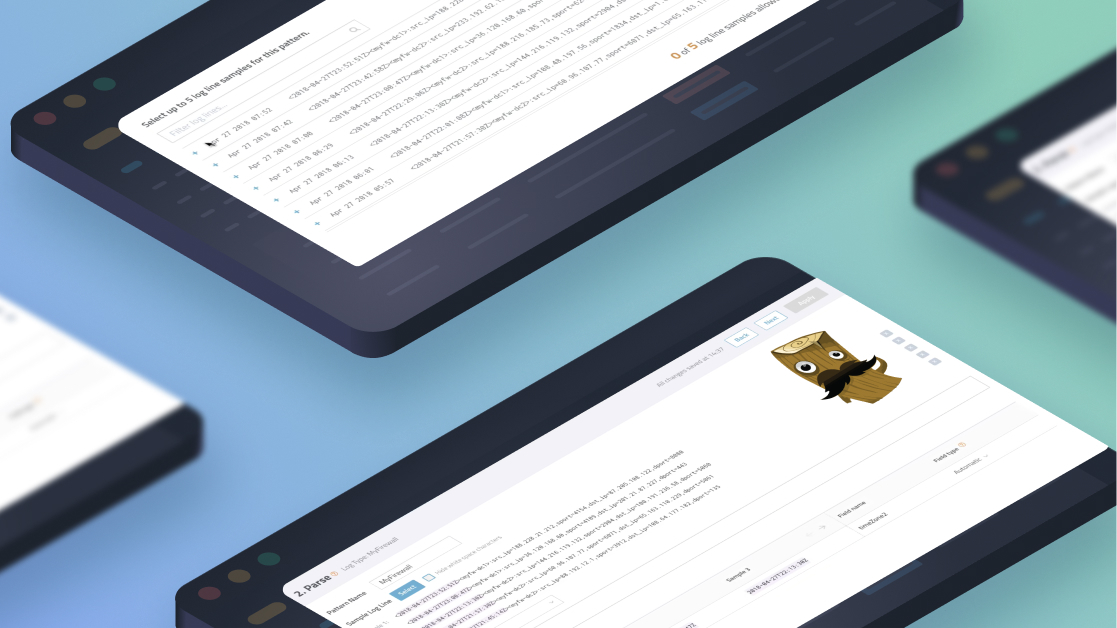
Grok Pattern Examples for Log Parsing
Searching and visualizing logs is next to impossible without log parsing, an underappreciated skill loggers need to read their data. Parsing structures your incoming (unstructured) logs so that there are clear fields and values that the user can search against during investigations, or when setting up dashboards. The most popular log parsing language is Grok. You can use Grok … [Read more...] about Grok Pattern Examples for Log Parsing
Everything You Need To Know About Log Analysis
Log analysis is typically done within a log management system, a software solution that gathers, sorts and stores log data and event logs from a variety of sources. Log management platforms allow the IT team and security professionals to establish a single point from which to access all relevant endpoint, network and application data. Typically, logs are searchable, which means … [Read more...] about Everything You Need To Know About Log Analysis
Product Overview – Cynet Centralized Log Management
For most organizations today, the logs produced by their security tools and environments provide a mixed bag. On the one hand, they can be a trove of valuable data on security breaches, vulnerabilities, attack patterns, and general security insights. On the other, organizations don't have the right means to manage the massive scale of logs and data produced to derive any value … [Read more...] about Product Overview – Cynet Centralized Log Management
ProtonMail Shares Activist’s IP Address With Authorities Despite Its “No Log” Claims
End-to-end encrypted email service provider ProtonMail has drawn criticism after it ceded to a legal request and shared the IP address of anti-gentrification activists with law enforcement authorities, leading to their arrests in France. The Switzerland-based company said it received a "legally binding order from the Swiss Federal Department of Justice" related to a collective … [Read more...] about ProtonMail Shares Activist’s IP Address With Authorities Despite Its “No Log” Claims