Feb 20, 2023Ravie LakshmananMobile Security / Zero Day Samsung has announced a new feature called Message Guard that comes with safeguards to protect users from malware and spyware via what's referred to as zero-click attacks. The South Korean chaebol said the solution "preemptively" secures users' devices by "limiting exposure to invisible threats disguised as image … [Read more...] about Samsung Introduces New Feature to Protect Users from Zero-Click Malware Attacks
Malware
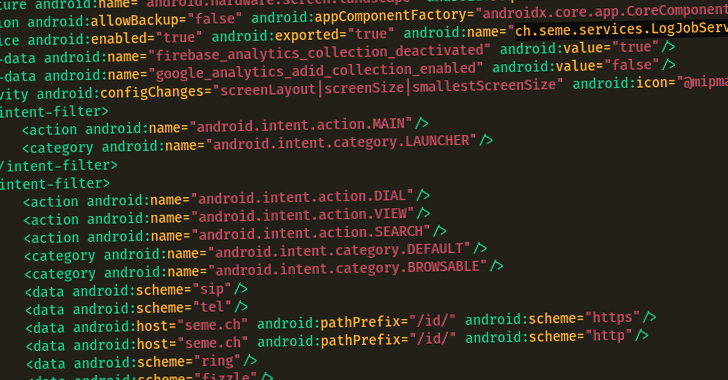
Experts Warn of RambleOn Android Malware Targeting South Korean Journalists
Feb 17, 2023Ravie LakshmananMobile Security / Cyber Threat Suspected North Korean nation-state actors targeted a journalist in South Korea with a malware-laced Android app as part of a social engineering campaign. The findings come from South Korea-based non-profit Interlab, which coined the new malware RambleOn. The malicious functionalities include the "ability to read and … [Read more...] about Experts Warn of RambleOn Android Malware Targeting South Korean Journalists
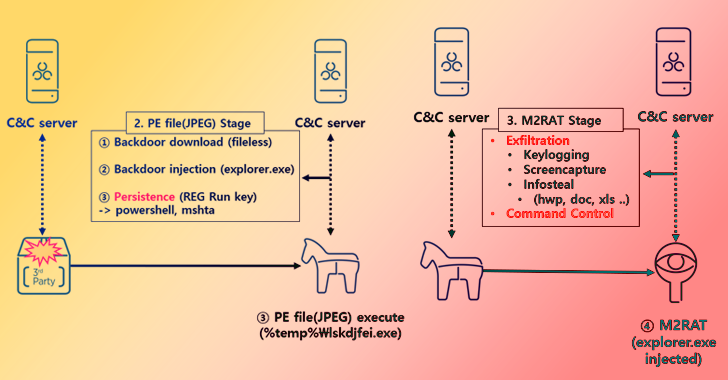
North Korea’s APT37 Targeting Southern Counterpart with New M2RAT Malware
Feb 15, 2023Ravie LakshmananThreat Intelligence / Malware The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting continued evolution of the group's features and tactics. APT37, also tracked under the monikers Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is … [Read more...] about North Korea’s APT37 Targeting Southern Counterpart with New M2RAT Malware
GuLoader Malware Using Malicious NSIS Executables to Target E-Commerce Industry
Feb 06, 2023Ravie LakshmananCyber Attack / Endpoint Security E-commerce industries in South Korea and the U.S. are at the receiving end of an ongoing GuLoader malware campaign, cybersecurity firm Trellix disclosed late last month. The malspam activity is notable for transitioning away from malware-laced Microsoft Word documents to NSIS executable files for loading the … [Read more...] about GuLoader Malware Using Malicious NSIS Executables to Target E-Commerce Industry
FormBook Malware Spreads via Malvertising Using MalVirt Loader to Evade Detection
Feb 06, 2023Ravie LakshmananMalvertising / Data Safety An ongoing malvertising campaign is being used to distribute virtualized .NET loaders that are designed to deploy the FormBook information-stealing malware. "The loaders, dubbed MalVirt, use obfuscated virtualization for anti-analysis and evasion along with the Windows Process Explorer driver for terminating processes," … [Read more...] about FormBook Malware Spreads via Malvertising Using MalVirt Loader to Evade Detection
Stealthy HeadCrab Malware Compromised Over 1,200 Redis Servers
Feb 02, 2023Ravie LakshmananDatabase Security / Cryptocurrency At least 1,200 Redis database servers worldwide have been corralled into a botnet using an "elusive and severe threat" dubbed HeadCrab since early September 2021. "This advanced threat actor utilizes a state-of-the-art, custom-made malware that is undetectable by agentless and traditional anti-virus solutions to … [Read more...] about Stealthy HeadCrab Malware Compromised Over 1,200 Redis Servers
Gootkit Malware Continues to Evolve with New Components and Obfuscations
Jan 29, 2023Ravie LakshmananCyber Threat / Malware The threat actors associated with the Gootkit malware have made "notable changes" to their toolset, adding new components and obfuscations to their infection chains. Google-owned Mandiant is monitoring the activity cluster under the moniker UNC2565, noting that the usage of the malware is "exclusive to this group." Gootkit, … [Read more...] about Gootkit Malware Continues to Evolve with New Components and Obfuscations
Roaming Mantis Spreading Mobile Malware That Hijacks Wi-Fi Routers’ DNS Settings
Jan 20, 2023Ravie LakshmananNetwork Security / Mobile Hacking Threat actors associated with the Roaming Mantis attack campaign have been observed delivering an updated variant of their patent mobile malware known as Wroba to infiltrate Wi-Fi routers and undertake Domain Name System (DNS) hijacking. Kaspersky, which carried out an analysis of the malicious artifact, said the … [Read more...] about Roaming Mantis Spreading Mobile Malware That Hijacks Wi-Fi Routers’ DNS Settings
Chinese Hackers Exploited Recent Fortinet Flaw as 0-Day to Drop Malware
Jan 20, 2023Ravie LakshmananFirewall / Network Security A suspected China-nexus threat actor exploited a recently patched vulnerability in Fortinet FortiOS SSL-VPN as a zero-day in attacks targeting a European government entity and a managed service provider (MSP) located in Africa. Telemetry evidence gathered by Google-owned Mandiant indicates that the exploitation occurred … [Read more...] about Chinese Hackers Exploited Recent Fortinet Flaw as 0-Day to Drop Malware
Researchers Uncover 3 PyPI Packages Spreading Malware to Developer Systems
Jan 17, 2023Ravie LakshmananSoftware Security / Supply Chain A threat actor by the name Lolip0p has uploaded three rogue packages to the Python Package Index (PyPI) repository that are designed to drop malware on compromised developer systems. The packages – named colorslib (versions 4.6.11 and 4.6.12), httpslib (versions 4.6.9 and 4.6.11), and libhttps (version 4.6.12) – by … [Read more...] about Researchers Uncover 3 PyPI Packages Spreading Malware to Developer Systems