Jan 14, 2023Ravie LakshmananDevOps / Data Security DevOps platform CircleCI on Friday disclosed that unidentified threat actors compromised an employee's laptop and leveraged malware to steal their two-factor authentication-backed credentials to breach the company's systems and data last month. The CI/CD service CircleCI said the "sophisticated attack" took place on December … [Read more...] about Malware Attack on CircleCI Engineer’s Laptop Leads to Recent Security Incident
Malware
Kinsing Crypto Malware Hits Kubernetes Clusters via Misconfigured PostgreSQL
Jan 09, 2023Ravie LakshmananKubernetes / Cryptojacking The threat actors behind the Kinsing cryptojacking operation have been spotted exploiting misconfigured and exposed PostgreSQL servers to obtain initial access to Kubernetes environments. A second initial access vector technique entails the use of vulnerable images, Sunders Bruskin, security researcher at Microsoft … [Read more...] about Kinsing Crypto Malware Hits Kubernetes Clusters via Misconfigured PostgreSQL
Russian Turla Hackers Hijack Decade-Old Malware Infrastructure to Deploy New Backdoors
Jan 08, 2023Ravie LakshmananCyberespionage / Threat Analysis The Russian cyberespionage group known as Turla has been observed piggybacking on attack infrastructure used by a decade-old malware to deliver its own reconnaissance and backdoor tools to targets in Ukraine. Google-owned Mandiant, which is tracking the operation under the uncategorized cluster moniker UNC4210, said … [Read more...] about Russian Turla Hackers Hijack Decade-Old Malware Infrastructure to Deploy New Backdoors
New shc-based Linux Malware Targeting Systems with Cryptocurrency Miner
Jan 04, 2023Ravie LakshmananLinux / Cryptocurrency A new Linux malware developed using the shell script compiler (shc) has been observed deploying a cryptocurrency miner on compromised systems. "It is presumed that after successful authentication through a dictionary attack on inadequately managed Linux SSH servers, various malware were installed on the target system," AhnLab … [Read more...] about New shc-based Linux Malware Targeting Systems with Cryptocurrency Miner
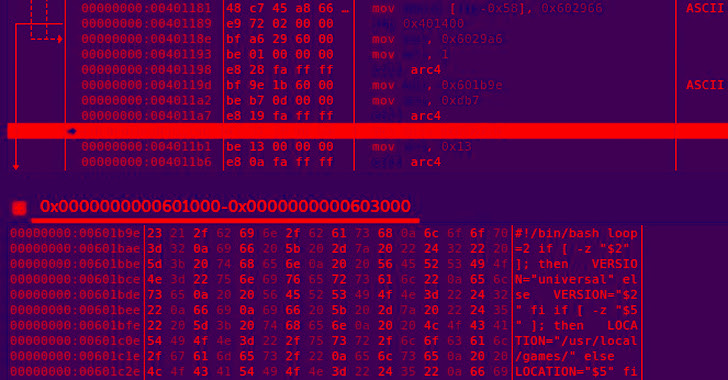
New Linux Malware Exploiting Over Two Dozen CMS Flaws
Jan 02, 2023Ravie LakshmananWeb Security / Linux WordPress sites are being targeted by a previously unknown strain of Linux malware that exploits flaws in over two dozen plugins and themes to compromise vulnerable systems. "If sites use outdated versions of such add-ons, lacking crucial fixes, the targeted web pages are injected with malicious JavaScripts," Russian security … [Read more...] about New Linux Malware Exploiting Over Two Dozen CMS Flaws
Malware Strains Targeting Python and JavaScript Developers Through Official Repositories
Dec 13, 2022Ravie Lakshmanan An active malware campaign is targeting the Python Package Index (PyPI) and npm repositories for Python and JavaScript with typosquatted and fake modules that deploy a ransomware strain, marking the latest security issue to affect software supply chains. The typosquatted Python packages all impersonate the popular requests library: dequests, … [Read more...] about Malware Strains Targeting Python and JavaScript Developers Through Official Repositories
Hack-for-Hire Group Targets Travel and Financial Entities with New Janicab Malware Variant
Dec 10, 2022Ravie LakshmananHack-for-Hire / Threat Intelligence Travel agencies have emerged as the target of a hack-for-hire group dubbed Evilnum as part of a broader campaign aimed at legal and financial investment institutions in the Middle East and Europe. The attacks targeting law firms throughout 2020 and 2021 involved a revamped variant of a malware called Janicab that … [Read more...] about Hack-for-Hire Group Targets Travel and Financial Entities with New Janicab Malware Variant
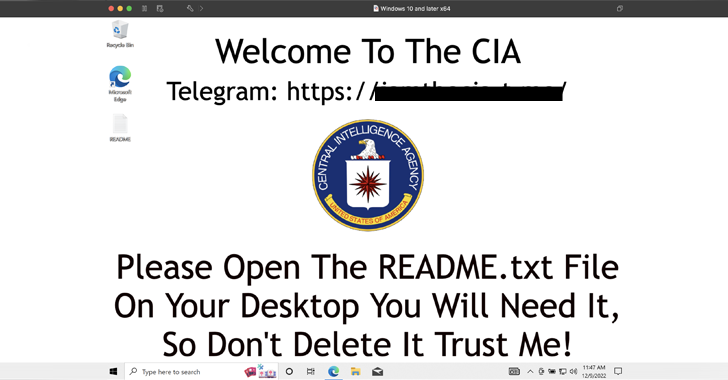
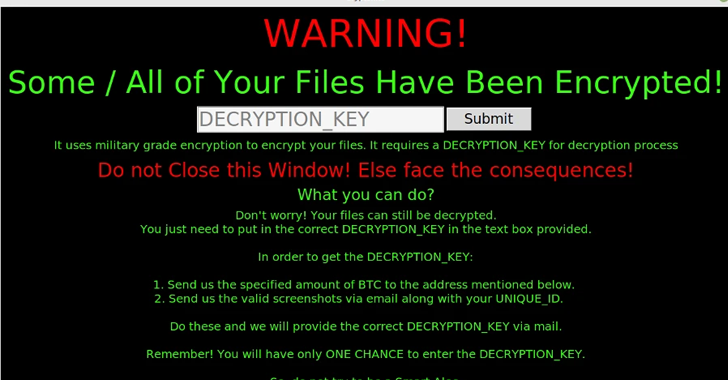
Open Source Ransomware Toolkit Cryptonite Turns Into Accidental Wiper Malware
Dec 06, 2022Ravie LakshmananEndpoint Security / Data Security A version of an open source ransomware toolkit called Cryptonite has been observed in the wild with wiper capabilities due to its "weak architecture and programming." Cryptonite, unlike other ransomware strains, is not available for sale on the cybercriminal underground, and was instead offered for free by an actor … [Read more...] about Open Source Ransomware Toolkit Cryptonite Turns Into Accidental Wiper Malware
Hackers Sign Android Malware Apps with Compromised Platform Certificates
Platform certificates used by Android smartphone vendors like Samsung, LG, and MediaTek have been found to be abused to sign malicious apps. The findings were first discovered and reported by Google reverse engineer Łukasz Siewierski on Thursday. "A platform certificate is the application signing certificate used to sign the 'android' application on the system image," a report … [Read more...] about Hackers Sign Android Malware Apps with Compromised Platform Certificates
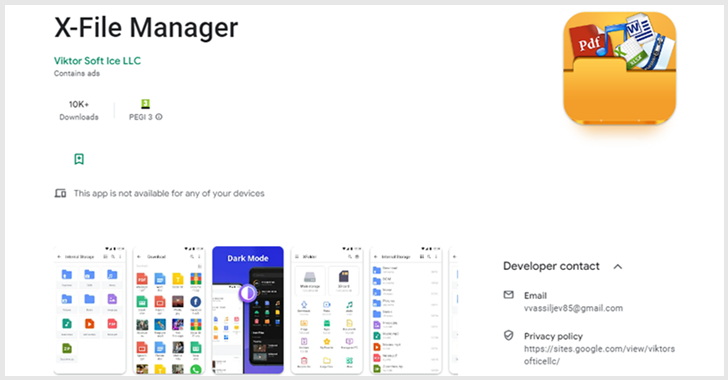
This Android File Manager App Infected Thousands of Devices with SharkBot Malware
The Android banking fraud malware known as SharkBot has reared its head once again on the official Google Play Store, posing as file managers to bypass the app marketplace's restrictions. A majority of the users who downloaded the rogue apps are located in the U.K. and Italy, Romanian cybersecurity company Bitdefender said in an analysis published this week. SharkBot, first … [Read more...] about This Android File Manager App Infected Thousands of Devices with SharkBot Malware