The cyberattack aimed at Viasat that temporarily knocked KA-SAT modems offline on February 24, 2022, the same day Russian military forces invaded Ukraine, is believed to have been the consequence of wiper malware, according to the latest research from SentinelOne. The findings come as the U.S. telecom company disclosed that it was the target of a multifaceted and deliberate" … [Read more...] about Russian Wiper Malware Likely Behind Recent Cyberattack on Viasat KA-SAT Modems
Malware
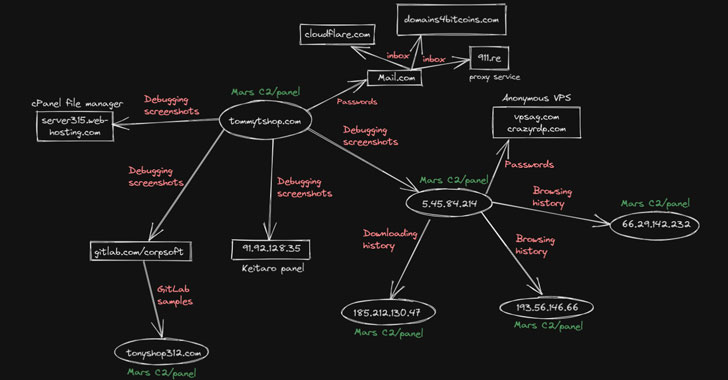
Researchers Expose Mars Stealer Malware Campaign Using Google Ads to Spread
A nascent information stealer called Mars has been observed in campaigns that take advantage of cracked versions of the malware to steal information stored in web browsers and cryptocurrency wallets. "Mars Stealer is being distributed via social engineering techniques, malspam campaigns, malicious software cracks, and keygens," Morphisec malware researcher Arnold Osipov said in … [Read more...] about Researchers Expose Mars Stealer Malware Campaign Using Google Ads to Spread
New Malware Loader ‘Verblecon’ Infects Hacked PCs with Cryptocurrency Miners
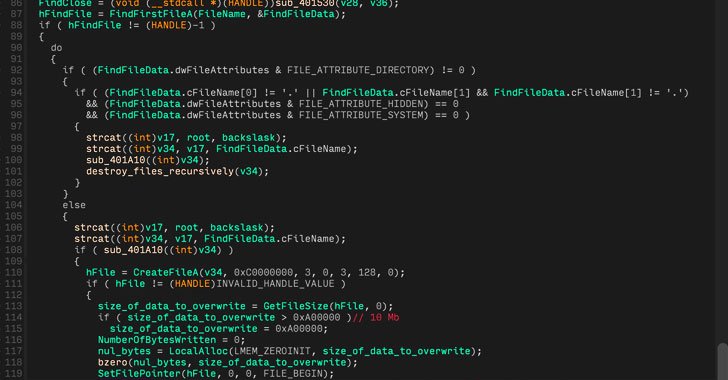
An unidentified threat actor has been observed employing a "complex and powerful" malware loader with the ultimate objective of deploying cryptocurrency miners on compromised systems and potentially facilitating the theft of Discord tokens. "The evidence found on victim networks appears to indicate that the goal of the attacker was to install cryptocurrency mining software on … [Read more...] about New Malware Loader ‘Verblecon’ Infects Hacked PCs with Cryptocurrency Miners
Hackers Hijack Email Reply Chains on Unpatched Exchange Servers to Spread Malware
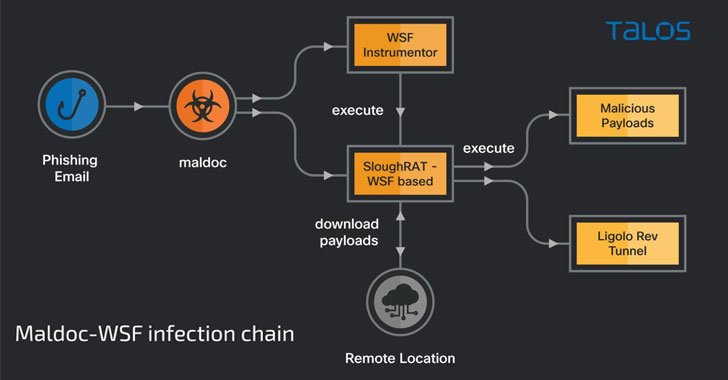
A new email phishing campaign has been spotted leveraging the tactic of conversation hijacking to deliver the IcedID info-stealing malware onto infected machines by making use of unpatched and publicly-exposed Microsoft Exchange servers. "The emails use a social engineering technique of conversation hijacking (also known as thread hijacking)," Israeli company Intezer said in a … [Read more...] about Hackers Hijack Email Reply Chains on Unpatched Exchange Servers to Spread Malware
Chinese ‘Mustang Panda’ Hackers Spotted Deploying New ‘Hodur’ Malware
A China-based advanced persistent threat (APT) known as Mustang Panda has been linked to an ongoing cyberespionage campaign using a previously undocumented variant of the PlugX remote access trojan on infected machines. Slovak cybersecurity firm ESET dubbed the new version Hodur, owing to its resemblance to another PlugX (aka Korplug) variant called THOR that came to light in … [Read more...] about Chinese ‘Mustang Panda’ Hackers Spotted Deploying New ‘Hodur’ Malware
Yet Another Data Wiping Malware Targeting Ukrainian Networks
Two weeks after details emerged about a second data wiper strain delivered in attacks against Ukraine, yet another destructive malware has been detected amid Russia's continuing military invasion of the country. Slovak cybersecurity company ESET dubbed the third wiper "CaddyWiper," which it said it first observed on March 14 around 9:38 a.m. UTC. Metadata associated with the … [Read more...] about Yet Another Data Wiping Malware Targeting Ukrainian Networks
Iranian Hackers Targeting Turkey and Arabian Peninsula in New Malware Campaign
The Iranian state-sponsored threat actor known as MuddyWater has been attributed to a new swarm of attacks targeting Turkey and the Arabian Peninsula with the goal of deploying remote access trojans (RATs) on compromised systems. "The MuddyWater supergroup is highly motivated and can use unauthorized access to conduct espionage, intellectual property theft, and deploy … [Read more...] about Iranian Hackers Targeting Turkey and Arabian Peninsula in New Malware Campaign
TeaBot Android Banking Malware Spreads Again Through Google Play Store Apps
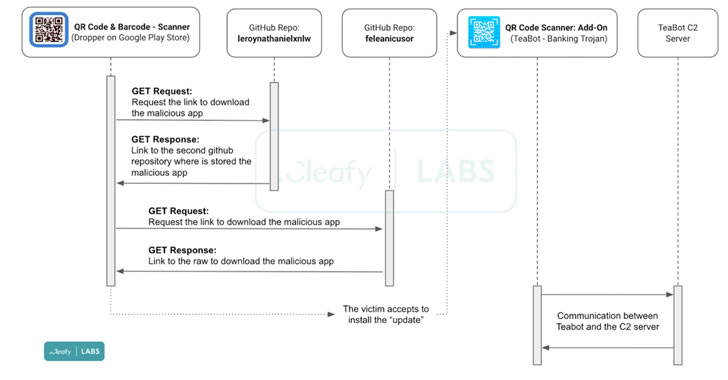
An Android banking trojan designed to steal credentials and SMS messages has been observed once again sneaking past Google Play Store protections to target users of more than 400 banking and financial apps, including those from Russia, China, and the U.S. "TeaBot RAT capabilities are achieved via the device screen's live streaming (requested on-demand) plus the abuse of … [Read more...] about TeaBot Android Banking Malware Spreads Again Through Google Play Store Apps
Microsoft Finds FoxBlade Malware Hit Ukraine Hours Before Russian Invasion
Update: It's worth noting that the malware Microsoft tracks as FoxBlade is the same as the data wiper that's been denominated HermeticWiper (aka KillDisk). Microsoft on Monday disclosed that it detected a new round of offensive and destructive cyberattacks directed against Ukraine's digital infrastructure hours before Russia launched its first missile strikes last week. The … [Read more...] about Microsoft Finds FoxBlade Malware Hit Ukraine Hours Before Russian Invasion
Social Media Hijacking Malware Spreading Through Gaming Apps on Microsoft Store
A new malware capable of controlling social media accounts is being distributed through Microsoft's official app store in the form of trojanized gaming apps, infecting more than 5,000 Windows machines in Sweden, Bulgaria, Russia, Bermuda, and Spain. Israeli cybersecurity company Check Point dubbed the malware "Electron Bot," in reference to a command-and-control (C2) domain … [Read more...] about Social Media Hijacking Malware Spreading Through Gaming Apps on Microsoft Store