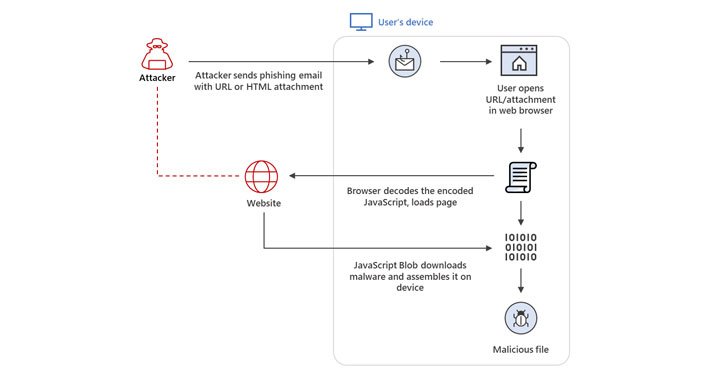
Threat actors are increasingly banking on the technique of HTML smuggling in phishing campaigns as a means to gain initial access and deploy an array of threats, including banking malware, remote administration trojans (RATs), and ransomware payloads. Microsoft 365 Defender Threat Intelligence Team, in a new report published Thursday, disclosed that it identified infiltrations … [Read more...] about Hackers Increasingly Using HTML Smuggling in Malware and Phishing Attacks
Malware
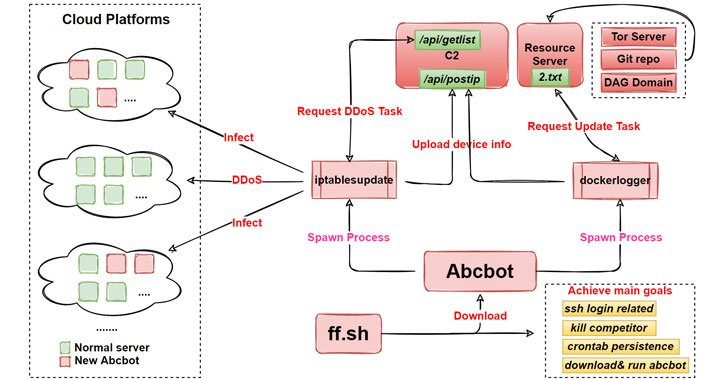
Abcbot — A New Evolving Wormable Botnet Malware Targeting Linux
Researchers from Qihoo 360's Netlab security team have released details of a new evolving botnet called "Abcbot" that has been observed in the wild with worm-like propagation features to infect Linux systems and launch distributed denial-of-service (DDoS) attacks against targets. While the earliest version of the botnet dates back to July 2021, new variants observed as recently … [Read more...] about Abcbot — A New Evolving Wormable Botnet Malware Targeting Linux
Automated Deobfuscation of Ploutus ATM Malware
One of the most tedious tasks in malware analysis is to get rid of the obfuscated code. Nowadays, almost every malware uses obfuscation to hinder the analysis and try to evade detection. In some cases, the obfuscation is not complex and is trivial to remove. An example of a trivial technique is the encryption of the strings with a hardcoded key. In other cases, the obfuscation … [Read more...] about Automated Deobfuscation of Ploutus ATM Malware
Researchers Discover PhoneSpy Malware Spying on South Korean Citizens
An ongoing mobile spyware campaign has been uncovered snooping on South Korean residents using a family of 23 malicious Android apps to siphon sensitive information and gain remote control of the devices. "With more than a thousand South Korean victims, the malicious group behind this invasive campaign has had access to all the data, communications, and services on their … [Read more...] about Researchers Discover PhoneSpy Malware Spying on South Korean Citizens
Malware on Discord and how to protect oneself
In the six years since the launch of Discord’s chat and VoIP service, the platform has become a popular tool for building communities of interest, especially among gamers. However, just like any other platform that hosts user-generated content, Discord can be exploited. Discord’s extensive customization options also open the door to attacks on ordinary users, both on and off … [Read more...] about Malware on Discord and how to protect oneself
This New Android Malware Can Gain Root Access to Your Smartphones
An unidentified threat actor has been linked to a new Android malware strain that features the ability to root smartphones and take complete control over infected smartphones while simultaneously taking steps to evade detection. The malware has been named "AbstractEmu" owing to its use of code abstraction and anti-emulation checks to avoid running while under analysis. Notably, … [Read more...] about This New Android Malware Can Gain Root Access to Your Smartphones
Popular NPM Package Hijacked to Publish Crypto-mining Malware
The U.S. Cybersecurity and Infrastructure Security Agency on Friday warned of crypto-mining and password-stealing malware embedded in "UAParser.js," a popular JavaScript NPM library with over 6 million weekly downloads, days after the NPM repository moved to get rid of three rogue packages that were found to mimic the same library. The supply-chain attack targeting the … [Read more...] about Popular NPM Package Hijacked to Publish Crypto-mining Malware
Attackers Behind Trickbot Expanding Malware Distribution Channels
The operators behind the pernicious TrickBot malware have resurfaced with new tricks that aim to increase its foothold by expanding its distribution channels, ultimately leading to the deployment of ransomware such as Conti. The threat actor, tracked under the monikers ITG23 and Wizard Spider, has been found to partner with other cybercrime gangs known Hive0105, Hive0106 (aka … [Read more...] about Attackers Behind Trickbot Expanding Malware Distribution Channels
Researchers Warn of FontOnLake Rootkit Malware Targeting Linux Systems
Cybersecurity researchers have detailed a new campaign that likely targets entities in Southeast Asia with a previously unrecognized Linux malware that's engineered to enable remote access to its operators, in addition to amassing credentials and function as a proxy server. The malware family, dubbed "FontOnLake" by Slovak cybersecurity firm ESET, is said to feature … [Read more...] about Researchers Warn of FontOnLake Rootkit Malware Targeting Linux Systems
New Malware Targets Windows Subsystem for Linux to Evade Detection
A number of malicious samples have been created for the Windows Subsystem for Linux (WSL) with the goal of compromising Windows machines, highlighting a sneaky method that allows the operators to stay under the radar and thwart detection by popular anti-malware engines. The "distinct tradecraft" marks the first instance where a threat actor has been found abusing WSL to install … [Read more...] about New Malware Targets Windows Subsystem for Linux to Evade Detection