It’s Partner Summit week and, for me, it’s an important reminder that no one company, not even Cisco, can do it alone. Our partners provide diverse perspectives, expertise, and solutions offerings. Each partner plays a key part in delivering the outcomes and experiences our customers need, want, and expect. So, when we say, “Let’s Own It”, it’s a rally cry for Cisco and our … [Read more...] about A World of Secure, Resilient Organizations
organizations
State-Sponsored Hackers Likely Exploited MS Exchange 0-Days Against ~10 Organizations
Microsoft on Friday disclosed that a single activity group in August 2022 achieved initial access and breached Exchange servers by chaining the two newly disclosed zero-day flaws in a limited set of attacks aimed at less than 10 organizations globally. "These attacks installed the Chopper web shell to facilitate hands-on-keyboard access, which the attackers used to perform … [Read more...] about State-Sponsored Hackers Likely Exploited MS Exchange 0-Days Against ~10 Organizations
How IT leaders build more proactive organizations using observability
In the lingua franca of modern IT architecture, latency is the perfect metaphor for an unresponsive business. If an organization’s latency is problematic, operations teams are always a step behind — reacting to events rather than anticipating them. But it doesn’t have to stay that way. For instance, Wells Fargo, a multinational financial services company headquartered in San … [Read more...] about How IT leaders build more proactive organizations using observability
How GRC protects the value of organizations — A simple guide to data quality and integrity
Contemporary organizations understand the importance of data and its impact on improving interactions with customers, offering quality products or services, and building loyalty. Data is fundamental to business success. It allows companies to make the right decisions at the right time and deliver the high-quality, personalized products and services that customers expect. There … [Read more...] about How GRC protects the value of organizations — A simple guide to data quality and integrity
Iranian Hackers Exploiting Unpatched Log4j 2 Bugs to Target Israeli Organizations
Iranian state-sponsored actors are leaving no stone unturned to exploit unpatched systems running Log4j to target Israeli entities, indicating the vulnerability's long tail for remediation. Microsoft attributed the latest set of activities to the umbrella threat group tracked as MuddyWater (aka Cobalt Ulster, Mercury, Seedworm, or Static Kitten), which is linked to the Iranian … [Read more...] about Iranian Hackers Exploiting Unpatched Log4j 2 Bugs to Target Israeli Organizations
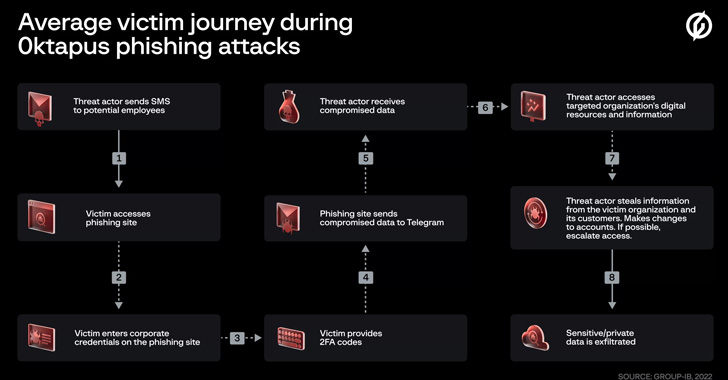
Okta Hackers Behind Twilio and Cloudflare Breach Hit Over 130 Organizations
The threat actor behind the attacks on Twilio and Cloudflare earlier this month has been linked to a broader phishing campaign aimed at 136 organizations that resulted in a cumulative compromise of 9,931 accounts. The activity has been condemned 0ktapus by Group-IB because the initial goal of the attacks was to "obtain Okta identity credentials and two-factor authentication … [Read more...] about Okta Hackers Behind Twilio and Cloudflare Breach Hit Over 130 Organizations
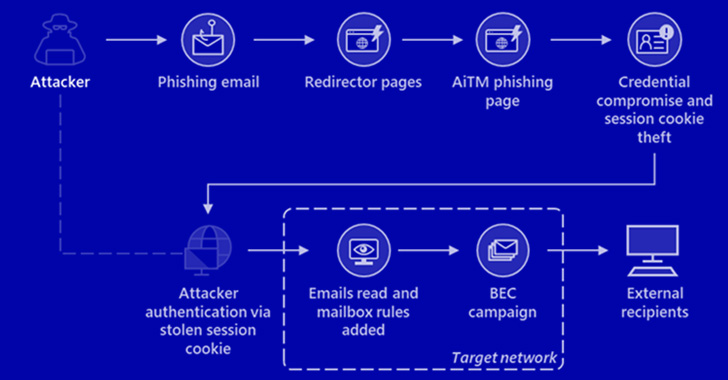
Microsoft Warns of Large-Scale AiTM Phishing Attacks Against Over 10,000 Organizations
Microsoft on Tuesday disclosed that a large-scale phishing campaign targeted over 10,000 organizations since September 2021 by hijacking Office 365's authentication process even on accounts secured with multi-factor authentication (MFA). "The attackers then used the stolen credentials and session cookies to access affected users' mailboxes and perform follow-on business email … [Read more...] about Microsoft Warns of Large-Scale AiTM Phishing Attacks Against Over 10,000 Organizations
North Korean Maui Ransomware Actively Targeting U.S. Healthcare Organizations
In a new joint cybersecurity advisory, U.S. cybersecurity and intelligence agencies have warned about the use of Maui ransomware by North Korean government-backed hackers to target the healthcare sector since at least May 2021. "North Korean state-sponsored cyber actors used Maui ransomware in these incidents to encrypt servers responsible for healthcare services—including … [Read more...] about North Korean Maui Ransomware Actively Targeting U.S. Healthcare Organizations
How Cisco Duo Is Simplifying Secure Access for Organizations Around the World
At Cisco Duo, we continually strive to enhance our products to make it easy for security practitioners to apply access policies based on the principles of zero trust. This blog highlights how Duo is achieving that goal by simplifying user and administrator experience and supporting data sovereignty requirements for customers around the world. Read on to get an overview of what … [Read more...] about How Cisco Duo Is Simplifying Secure Access for Organizations Around the World
Indian Govt Orders Organizations to Report Security Breaches Within 6 Hours to CERT-In
India's computer and emergency response team, CERT-In, on Thursday published new guidelines that require service providers, intermediaries, data centers, and government entities to compulsorily report cybersecurity incidents, including data breaches, within six hours. "Any service provider, intermediary, data center, body corporate and Government organization shall mandatorily … [Read more...] about Indian Govt Orders Organizations to Report Security Breaches Within 6 Hours to CERT-In