Though 2024 may be behind us, many of the security threats and vulnerabilities that organizations faced last year remain. The CrowdStrike Professional Services Red Team tracks them all in its efforts to defend organizations against adversaries. The three most common exploitation paths we encountered were: Unsecured Credentials: Weak or exposed credentials remain one … [Read more...] about Top 3 Trends in Red Team Exploitation Paths
Paths
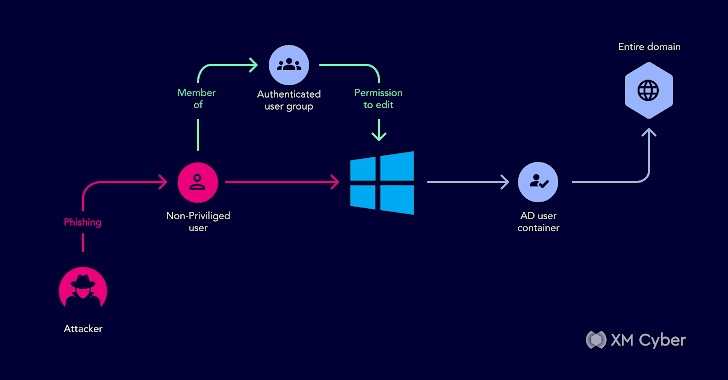
Understanding Active Directory Attack Paths to Improve Security
Introduced in 1999, Microsoft Active Directory is the default identity and access management service in Windows networks, responsible for assigning and enforcing security policies for all network endpoints. With it, users can access various resources across networks. As things tend to do, times, they are a'changin' – and a few years back, Microsoft introduced Azure Active … [Read more...] about Understanding Active Directory Attack Paths to Improve Security