“Logz.io Observability IQ Assistant helps us to find the root cause of the issues faster, and it reduces a lot of the manual processes that we were doing before.”That’s the assessment of Senior DevOps Engineer and Logz.io user Armin Morattab when discussing the impact of AI on his day-to-day job.He dives deep on AI, observability, and strategies for improving workflows with … [Read more...] about Supercharging Engineer Productivity with Real World AI
Real
Inside the MITRE ATT&CK Evaluation: How CrowdStrike’s Elite Managed Services Operate in the Real World
Following CrowdStrike’s strong performance in the first-ever MITRE ATT&CK® Evaluations for Security Managed Services Providers with 99% detection coverage, we take a deep dive into the testing process and how our elite managed services operate in the real world. We recently announced CrowdStrike achieved 99% detection coverage in the inaugural MITRE ATT&CK Evaluations … [Read more...] about Inside the MITRE ATT&CK Evaluation: How CrowdStrike’s Elite Managed Services Operate in the Real World
British Hacker Charged for Operating “The Real Deal” Dark Web Marketplace
A 34-year-old U.K. national has been arraigned in the U.S. for operating a dark web marketplace called The Real Deal that specialized in the sales of hacking tools and stolen login credentials. Daniel Kaye, who went by a litany of pseudonyms Popopret, Bestbuy, UserL0ser, and Spdrman, has been charged with five counts of access device fraud and one count of money laundering … [Read more...] about British Hacker Charged for Operating “The Real Deal” Dark Web Marketplace
Performing Real User Monitoring (RUM) with Elastic APM
Sorry if I lured you into the mood of having a sip of a wonderful cocktail made with rum and you realized that the RUM I’m talking about is not the rum you are craving. But, be assured that Elastic RUM is equally wonderful! Let’s take a sip! I do want to warn you that it will take a bit of time to go through the amount of detail I will cover in this blog.What is RUM?Elastic … [Read more...] about Performing Real User Monitoring (RUM) with Elastic APM
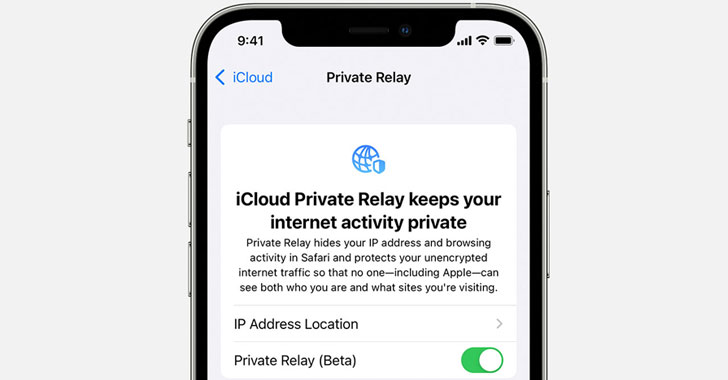
Apple’s New iCloud Private Relay Service Leaks Users’ Real IP Addresses
A new as-yet unpatched weakness in Apple's iCloud Private Relay feature could be circumvented to leak users' true IP addresses from iOS devices running the latest version of the operating system. Introduced with iOS 15, which was officially released this week, iCloud Private Relay aims to improve anonymity on the web by employing a dual-hop architecture that effectively shields … [Read more...] about Apple’s New iCloud Private Relay Service Leaks Users’ Real IP Addresses
Unleashing SecureX on a real Cyber Campaign
There’s so much excitement around the general availability (GA) for SecureX. Let’s take a look under the hood as the industry learns to define what we should all expect from a security platform. And while I have your attention, I am going to attempt to thoroughly explain how SecureX delivers simplicity, visibility and efficiency through a cloud-native, built-in platform with an … [Read more...] about Unleashing SecureX on a real Cyber Campaign
CrowdStrike’s Real Time Response Enables System Recovery
Introduction Cyberattacks including ransomware have increased as work environments have changed, and organizations have shifted to supporting more remote personnel. With threats increasing against these remote systems, the ability to block attacks and respond rapidly in the event of a compromise is even more challenging. Do security teams have the visibility and context they … [Read more...] about CrowdStrike’s Real Time Response Enables System Recovery
SMB Cybersecurity: The Real Benefits of a Top-Down Approach
The security industry has sometimes underestimated small and medium sized businesses. Several myths haunt SMBs, leading to the misconception that they don’t take security as seriously as larger organizations. But thanks to a recent survey, data collected from almost 500 SMBs (defined here as organizations with 250-499 employees) reveals a different story. In a recent Cisco Chat … [Read more...] about SMB Cybersecurity: The Real Benefits of a Top-Down Approach
CrowdStrike’s Real Time Response Expands Protections
Introduction Sinkholes can be used by both bad actors and system administrators alike. Bad actors can redirect systems to malicious domains and security admins can stop systems from reaching those domains. If remote employees are not using the corporate VPN, do security teams have the ability to manipulate system redirects and sinkhole malicious … [Read more...] about CrowdStrike’s Real Time Response Expands Protections
CrowdStrike’s Real Time Response Enables Remote Remediation
Introduction Remote systems can be easy targets for attackers. When these systems are compromised, responders need to work quickly to understand the attack and take action to remediate. The responders need remote system visibility and access since users can’t walk a laptop over to IT. Do responders have the visibility and context they need to understand the threat? Can they … [Read more...] about CrowdStrike’s Real Time Response Enables Remote Remediation