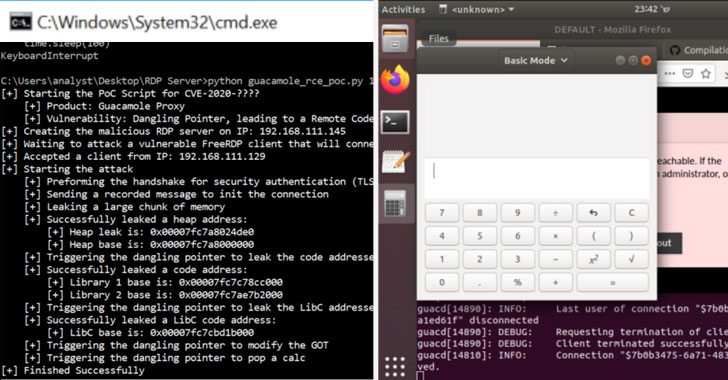
A new research has uncovered multiple critical reverse RDP vulnerabilities in Apache Guacamole, a popular remote desktop application used by system administrators to access and manage Windows and Linux machines remotely.The reported flaws could potentially let bad actors achieve full control over the Guacamole server, intercept, and control all other connected … [Read more...] about Critical Apache Guacamole Flaws Put Remote Desktops at Risk of Hacking
remote
Threat Intelligence to Protect a Remote Workforce
Introduction Adversaries are preying on the fear and disruption caused by the coronavirus pandemic. Their use of COVID-19-related phishing lures with promises of aid or information is now commonplace. In addition, the rapid pivot of organizations to work-from-home has created opportunities for adversaries to probe for security gaps in the newly deployed infrastructure. How can … [Read more...] about Threat Intelligence to Protect a Remote Workforce
New Partnership Secures Remote Workforce With Integrated Solution
CrowdStrike, Netskope, Okta and Proofpoint are joining together to help better safeguard organizations by delivering an integrated, Zero Trust security strategy that is designed to protect today’s dynamic and remote working environments at scale. The sudden shift to a remote workforce due to the COVID-19 pandemic has driven many organizations to accelerate their multi-year … [Read more...] about New Partnership Secures Remote Workforce With Integrated Solution
CrowdStrike’s Real Time Response Enables Remote Remediation
Introduction Remote systems can be easy targets for attackers. When these systems are compromised, responders need to work quickly to understand the attack and take action to remediate. The responders need remote system visibility and access since users can’t walk a laptop over to IT. Do responders have the visibility and context they need to understand the threat? Can they … [Read more...] about CrowdStrike’s Real Time Response Enables Remote Remediation
THREAT HUNTING WITH A REMOTE WORKFORCE
Introduction In the world of cybersecurity, adversaries and defenders are constantly trying to outmaneuver each other and gain strategic advantage. For example, attackers are keenly aware that the shift to work-from-home has placed tremendous pressure on security teams and realize that now is the time to exploit potential infrastructure and security gaps caused by this … [Read more...] about THREAT HUNTING WITH A REMOTE WORKFORCE
Remote Access Trojans – Cisco Blog
You’re working for a high-profile technology company, close to releasing a market-changing product to the public. It’s a highly contested space, with many competitors, both domestic and international. There’s also a lot of buzz in the media and online speculation on the scope and impact your new product will have. And it goes without question that customers are keen to know … [Read more...] about Remote Access Trojans – Cisco Blog
SIM Cards in 29 Countries Vulnerable to Remote Simjacker Attacks
Until now, I'm sure you all might have heard of the SimJacker vulnerability disclosed exactly a month ago that affects a wide range of SIM cards and can remotely be exploited to hack into any mobile phone just by sending a specially crafted binary SMS.If you are unaware, the name "SimJacker" has been given to a class of vulnerabilities that resides due to a lack of … [Read more...] about SIM Cards in 29 Countries Vulnerable to Remote Simjacker Attacks
Exim TLS Flaw Opens Email Servers to Remote ‘Root’ Code Execution Attacks
A critical remote code execution vulnerability has been discovered in the popular open-source Exim email server software, leaving at least over half a million email servers vulnerable to remote hackers.Exim maintainers today released Exim version 4.92.2 after publishing an early warning two days ago, giving system administrators a heads-up on its upcoming security patches that … [Read more...] about Exim TLS Flaw Opens Email Servers to Remote ‘Root’ Code Execution Attacks
BMC Vulnerabilities Expose Supermicro Servers to Remote USB-Attacks
Enterprise servers powered by Supermicro motherboards can remotely be compromised by virtually plugging in malicious USB devices, cybersecurity researchers at firmware security company Eclypsium told The Hacker News.Yes, that's correct. You can launch all types of USB attacks against vulnerable Supermicro servers without actually physically accessing them or waiting for your … [Read more...] about BMC Vulnerabilities Expose Supermicro Servers to Remote USB-Attacks
Pre-Installed Software Flaw Exposes Most Dell Computers to Remote Hacking
If you use a Dell computer, then beware — hackers could compromise your system remotely.Bill Demirkapi, a 17-year-old independent security researcher, has discovered a critical remote code execution vulnerability in the Dell SupportAssist utility that comes pre-installed on most Dell computers.Dell SupportAssist, formerly known as Dell System Detect, checks the health of your … [Read more...] about Pre-Installed Software Flaw Exposes Most Dell Computers to Remote Hacking