A group of academics from the North Carolina State University and Dokuz Eylul University have demonstrated what they say is the "first side-channel attack" on homomorphic encryption that could be exploited to leak data as the encryption process is underway. "Basically, by monitoring power consumption in a device that is encoding data for homomorphic encryption, we are able to … [Read more...] about Researchers Demonstrate New Side-Channel Attack on Homomorphic Encryption
Researchers
Researchers Link ShadowPad Malware Attacks to Chinese Ministry and PLA
Cybersecurity researchers have detailed the inner workings of ShadowPad, a sophisticated and modular backdoor that has been adopted by a growing number of Chinese threat groups in recent years, while also linking it to the country's civilian and military intelligence agencies. "ShadowPad is decrypted in memory using a custom decryption algorithm," researchers from Secureworks … [Read more...] about Researchers Link ShadowPad Malware Attacks to Chinese Ministry and PLA
Researchers Find Bugs in Over A Dozen Widely Used URL Parser Libraries
A study of 16 different Uniform Resource Locator (URL) parsing libraries has unearthed inconsistencies and confusions that could be exploited to bypass validations and open the door to a wide range of attack vectors. In a deep-dive analysis jointly conducted by cybersecurity firms Claroty and Synk, eight security vulnerabilities were identified in as many third-party libraries … [Read more...] about Researchers Find Bugs in Over A Dozen Widely Used URL Parser Libraries
Researchers Uncover Hacker Group Behind Organized Financial-Theft Operation
Cybersecurity researchers have taken the wraps of an organized financial-theft operation undertaken by a discreet actor to target transaction processing systems and siphon funds from entities primarily located in Latin America for at least four years. The malicious hacking group has been codenamed Elephant Beetle by Israeli incident response firm Sygnia, with the intrusions … [Read more...] about Researchers Uncover Hacker Group Behind Organized Financial-Theft Operation
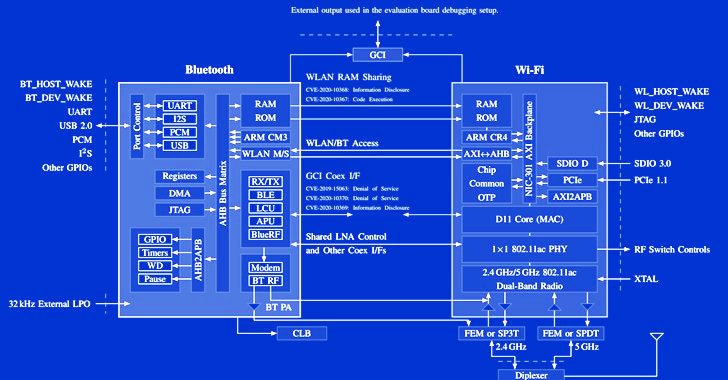
Researchers Uncover New Coexistence Attacks On Wi-Fi and Bluetooth Chips
Cybersecurity researchers have demonstrated a new attack technique that makes it possible to leverage a device's Bluetooth component to directly extract network passwords and manipulate traffic on a Wi-Fi chip. The novel attacks work against the so-called "combo chips," which are specialized chips that are equipped to handle different types of radio wave-based wireless … [Read more...] about Researchers Uncover New Coexistence Attacks On Wi-Fi and Bluetooth Chips
Researchers Detail How Pakistani Hackers Targeting Indian and Afghan Governments
A Pakistani threat actor successfully socially engineered a number of ministries in Afghanistan and a shared government computer in India to steal sensitive Google, Twitter, and Facebook credentials from its targets and stealthily obtain access to government portals. Malwarebytes' latest findings go into detail about the new tactics and tools adopted by the APT group known as … [Read more...] about Researchers Detail How Pakistani Hackers Targeting Indian and Afghan Governments
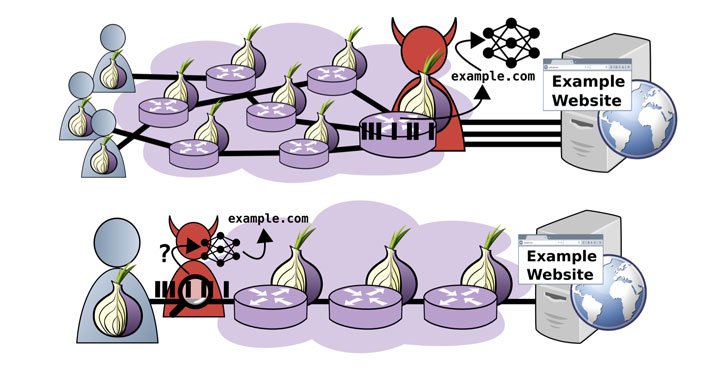
Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
A new analysis of website fingerprinting (WF) attacks aimed at the Tor web browser has revealed that it's possible for an adversary to glean a website frequented by a victim, but only in scenarios where the threat actor is interested in a specific subset of the websites visited by users. "While attacks can exceed 95% accuracy when monitoring a small set of five popular … [Read more...] about Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
Researchers Uncover Hacker-for-Hire Group That’s Active Since 2015
A new cyber mercenary hacker-for-hire group dubbed "Void Balaur" has been linked to a string of cyberespionage and data theft activities targeting thousands of entities as well as human rights activists, politicians, and government officials around the world at least since 2015 for financial gain while lurking in the shadows. Named after a many-headed dragon from Romanian … [Read more...] about Researchers Uncover Hacker-for-Hire Group That’s Active Since 2015
Researchers Discover PhoneSpy Malware Spying on South Korean Citizens
An ongoing mobile spyware campaign has been uncovered snooping on South Korean residents using a family of 23 malicious Android apps to siphon sensitive information and gain remote control of the devices. "With more than a thousand South Korean victims, the malicious group behind this invasive campaign has had access to all the data, communications, and services on their … [Read more...] about Researchers Discover PhoneSpy Malware Spying on South Korean Citizens
Researchers Break Intel SGX With New ‘SmashEx’ CPU Attack Technique
A newly disclosed vulnerability affecting Intel processors could be abused by an adversary to gain access to sensitive information stored within enclaves and even run arbitrary code on vulnerable systems. The vulnerability (CVE-2021-0186, CVSS score: 8.2) was discovered by a group of academics from ETH Zurich, the National University of Singapore, and the Chinese National … [Read more...] about Researchers Break Intel SGX With New ‘SmashEx’ CPU Attack Technique